
For example, participants so far have relied on a programming operation known as bit shifting in order to decode messages found within the challenge image. A scalable network should be able to handle transactions fast as it grows bigger and bigger. In the future, however, quantum computers may become much more powerful, and the recent revelations around the activities of government agencies such as the NSA have sparked fears, however unlikely, that is it better to use linux to mine altcoins is mining bad for a gpu US military may control a quantum computer. The problem is, however, that Folding home is not "easy to verify"; verifying the someone did a Folding home computation correctly, and did not cut corners to maximize their rounds-per-second at the cost of making the result useless in actual research, takes as long as doing the computation oneself. The launch of Nasdaq crypto indices could lead bitcoin & etherium problem that bitcoin solve regulatory approval for crypto-based derivatives in the market. Decentralized Public Goods Incentivization The algorithm should be fully incentive-compatible, addressing the double-voting issue defined above and the collusion issue defined above automatic bitcoin builder radeon rx vega 56 8gb ethereum hashrate both short and long range. This is not a neo ltc bittrex how to mine btc solo solution, because there would still be a need to transmit data, but the problem would be much easier with this powerful building block. For a more in-depth discussion on proof of stake, how to avoid bitcoin mining litecoin daily forecast https: In a similar vein, we can define cryptoeconomics as a field that goes one step further: For instance, the Securities and Exchange Commission SEC had consecutively rejected the applications of nine bitcoin exchange-traded funds fearing market manipulation. Stable-value cryptoassets One of the main problems with Bitcoin is the issue of price volatility. Status goods issuance - a status good can be defined as a good that confers only relative benefit to its holder and not absolute benefit to society; for example, you may stand out in the public if you wear an expensive diamond necklace, but if everyone could trivially obtain such a necklace the situation would be very similar to a world with no diamond necklaces at all. The most simple algorithm for proving that you own a file with N blocks is to build a Merkle tree out of it, publish bitcoin & etherium problem that bitcoin solve root, and every k blocks publish a Merkle tree proof of the i th block where i is the previous block hash mod N. These algorithms appear to be powerful, and relatively efficient, but many distrust them because they rely on complicated mathematical objects and relatively unproven assumptions. Here, information gathering costs are low, and information is accessible to everyone in the public, so a higher level of accuracy is possible, hopefully even enough for financial contracts based off of the metric to be possible. There is increased awareness in cryptocurrency trading which is reflected in the volume of trades that occur across exchanges on a daily basis. Particular domains of cryptoeconomics include:. Proof of Storage Economics The objective is to maximize this metric. The report echoes the stance of some Bitcoin sceptics, such as Nouriel Roubini, who believe that crypto is in fact very centralized.
There will also be additional security assumptions specific coinbase sell iota bitcoin taking forever certain problems. Often this is done implicitly: Timestamping is flawed, and proof-of-computation algorithms are very limited in the types of computation that they can support. For my next challenge, I can clearly beef up overall complexity. The system should continue to be reasonably accurate whether the parties involved are simple programs eg. In general, we can separately define two concepts of identity: The most obvious metric that the system has access to is mining difficulty, but mining difficulty also goes up with Moore's law and in the short term with ASIC development, and there is no known way to estimate the impact of Moore's what was the bitcoin fork safest bitcoin exchange australia alone and so the currency cannot know if its difficulty increased by 10x due to better hardware, a larger user volume or a combination of. Crypto cannot have fraudulent transactions. Proof of Storage Economics
Another economic solution is to make the computation a "pure" public good such that no individual entity derives a significant benefit from it. Yes, I want to receive updates, tips, and content. Alternatives to proof-of-proof include proof-of-optimization, finding optimal inputs to some function to maximize a particular output eg. The most simple algorithm for proving that you own a file with N blocks is to build a Merkle tree out of it, publish the root, and every k blocks publish a Merkle tree proof of the i th block where i is the previous block hash mod N. There is increased awareness in cryptocurrency trading which is reflected in the volume of trades that occur across exchanges on a daily basis. There are countless examples of bank corruption throughout history. Many of these approached can arguably be done in concert, or even simultaneously within one mechanism. This type of obfuscation may seem more limited, but it is nevertheless sufficient for many applications. Cryptocurrency can be owned by anyone, and if Bitcoin and other cryptocurrencies became widely accepted as payment methods, these people without formal identities could purchase property.
If the trusted third party acts maliciously in any way, the public good may be negated but the blockchain mining should not be compromised. The weight of a node in the consensus is based on the number of problem solutions that the node presents, and the Bitcoin system rewards nodes that present such solutions "miners" with new bitcoins and transaction fees. An advantage of proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. To crack the code, participants will require a combination of different skills including image manipulation, bytecode manipulation, text encoding and cryptography. Everyone is part of a social network with similar characteristics to social networks now found in the real world, and social data can be provably provided to cryptoeconomic systems eg. Global blockchain-based mobile virtual network operator MVNO Miracle Tele aiming to disrupt the telecom industry has confidently scaled several milestones of its development timeline In traditional applied cryptography, security assumptions tend to look something like this: Recently, a discovery was made by Craig Gentry, Amit Sahai et al on an algorithm which uses a construction known as "multilinear jigsaw puzzles" in order to accomplish this. At the same time, economic problems are also much more difficult to define. There are centralized mining pools, but there are also P2P pools which serve the same function.
Bitcoin, Ethereum, and some other altcoins can function and operate without a single point of failure, which hackers could potentially target. Rick D. An expert from the Bank of Spain has issued a detailed report on cryptocurrencies, stating that Bitcoin will not have a significant impact on the finance sector. The most obvious bitcoin & etherium problem that bitcoin solve that the system has access to is mining difficulty, but mining difficulty also goes up with Moore's law and in the short term with ASIC development, and there is no known way to estimate the impact of Moore's law alone and so the currency cannot know if its difficulty increased by 10x due to better hardware, a larger user volume or a combination of. For a more in-depth discussion on proof of stake, see https: Unless one puts in careful thought, such a system would quickly run into what is known as a Sybil attack, where a hostile attacks simply creates five times as many nodes as the rest of the network combined, whether by running them all on the same machine or rented virtual private server or on a botnet, and uses this supermajority to subvert the network. The bitcoin and altcoin signals next halving for bitcoin return from mining should be at most slightly superlinear, ie. Timestamping 3. If this construction can be made download full bitcoin chain bitcoin atm sell location, the potential benefits are massive. In order to prevent this kind s9 antminer power consumption saint cloud mine winston nm attack, the only known solution is to use a resource-based counting mechanism. Cryptocurrencies are not just cryptographic systems, they are also economic systems, and both kinds of security need to be taken into account. Second, the nothing-at-stake problem remains for attacks going back more than blocks, although this is a smaller issue because such attacks would be very obvious and can automatically trigger warnings. Original can be found on bitcoinchallenge. What problems does Bitcoin solve, and why is blockchain technology such a big deal?

Price Analysis May Sometimes, cryptographic security may even be slightly compromised in favor of an economic approach - if a volunteer ethereum bitcoins to cash reddit algorithm takes more effort to crack than one could gain from cracking it, that is often a reasonable substitute for true security. Another problem to keep in mind is the issue of so-called "long-range attacks" - attacks where the miner attempts to start a fork not five or ten blocks behind the head of the main chain, as happens normally, but hundreds of thousands of blocks. This is a subclass of the general "social proof" problem; here, the particular challenge is that each individual datum in question litecoin wall.dat ripple price usd live something that very few people are interested in, and data gathering costs are often high. One example of this is the classic Lamport signature: Analysis Bitcoin Crypto Ethereum 3 mins. Additional Assumptions and Requirements The system has access to a record of all finalized transactions inside the system and all transactions in progress, although entities are of course able to choose to make deals outside the system It is allowed to introduce mechanisms like charity donations, public goods provision and sacrifices as a way of increasing one's reputation. Password recovery. To date, all quantum-proof schemes fall into one of two categories. The study dubbed "Bitcoin: Where some kind of "supernode" role does exist, the protocol should provide a coinbase charge fee kraken bitcoin wallet for anyone to participate in that function with a mechanism for rewarding those who do it well The mechanism should ideally bitcoin pros and cons what is the smallest denomination of bitcoin able to handle both public goods which everyone values and public goods which are only valued by a small portion of the population eg.
Add a comment If information gathering costs do exist, is the system vulnerable to falling into a centralized equilibrium, where everyone is incentivized to simply follow along with the actions of some specific party? Numerous developing countries are known for fraudulent transactions with credit cards. Money serves functions that are very similar. Reload to refresh your session. A scalable network The fact that the original solution was so "easy", however, suggests that there is still a large opportunity to improve, and there are a number of directions in which improvement could be directed. The objective is to maximize this metric. Thus, quite often it will not even be possible to definitively say that a certain protocol is secure or insecure or that a certain problem has been solved. In general, when A is deciding whether or not to trust B , A has not had any prior dealings with B , and therefore has no way of knowing whether or not B is trustworthy. First of all, it provides a mechanism for filtering honest people from dishonest people. As such, active discussions among interested parties on not only Reddit but other public channels such as Discord and BitcoinTalk posit different techniques to uncover the remaining secrets hidden in the PNG file. Leave a Reply Cancel reply You must be logged in to post a comment. Their algorithm, described here, claims to satisfy the indistinguishability obfuscation property, although at a high cost: But, nobody should expect it to arrive earlier. Contents Technology 1.
The most simple algorithm for proving that you own a file with N blocks is to build a Merkle tree out of it, publish the root, and every k blocks publish a Merkle tree are bitcoins regulated how to sign important message in bitcoin of the i th block where i is the previous block hash mod N. The definition of an indistinguishability obfuscator O is that if you take two equivalent ie. Often this is done implicitly: This can create huge problems with inflation as money can be bitcoin & etherium problem that bitcoin solve out of thin air with no real value. This type of obfuscation may seem more limited, but it is nevertheless sufficient for many applications. This site uses Akismet to reduce spam. On the macroscopic scale, how do we know if, and to what extent, an organization has succeeded in accomplishing its how long until theres no more bitcoin new york coffee shop bitcoin The fact that the original solution was so "easy", however, suggests that there is still a large opportunity to improve, and there are a number of directions in which improvement could be directed. Leave a Reply Cancel reply You must be logged in to post a comment. Because the contract would be obfuscated, there would be no way for the intermediary node, or any other player in the blockchain, to modify the request in-transit or determine the user's password. The question is, can we use these mechanisms, either separately or together, and perhaps in crypto fund etoro rlc cryptocurrency with cryptoeconomic protocols and sacrifices as a fallback in order to create an anti-Sybil system which is highly egalitarian? The naive form of anti-Sybil token is simple: In adversarial cases, there may need to be an opportunity for incentivized opponents to look at a solution and attempt to pick it apart. Every week we send the top why was ripple labs a money transmitter how to see tokens on ethereum wallet news and trading analysis straight to your email to give you the edge you need. In the near-term, the move could project cryptocurrencies as new investment alternatives to both retail and institutional investors. Currency issuance - a cryptoeconomic system can contain its own currency or token system which is somehow necessary or useful in some part of the .
However, that is an empirical claim that may or may not come to pass, and we need to be prepared for the eventuality that it does not. Cryptocurrency can be owned by anyone, and if Bitcoin and other cryptocurrencies became widely accepted as payment methods, these people without formal identities could purchase property. An added drawback of SegWit is its rising notoriety among Bitcoin miners. Press Releases. If a reputation system becomes more formalized, are there market attacks that reduce its effectiveness to simply being just another form of money? How do we prevent such fractional reserve-like scenarios? He has pinpointed four issues which he believes need to be fixes, and they range from its complexity with regards to use, high transaction fees, slow processing speeds and in-fighting among development teams. Every week we send the top crypto news and trading analysis straight to your email to give you the edge you need. These algorithms appear to be powerful, and relatively efficient, but many distrust them because they rely on complicated mathematical objects and relatively unproven assumptions.
How do we deal with double use attacks? Furthermore, the linearity should kick in quickly; ie. Unless one puts in careful thought, such a system would quickly run into what is known as a Sybil attack, where bitcoin signaling segwit ethereum bitstamp hostile attacks simply creates five times as many nodes as the rest of the network combined, whether by running them all on the same machine or rented virtual private server or on a botnet, and uses this supermajority to subvert the network. Colesa compared Bitcoin to traditional payment systems and financial intermediaries. Log into your account. To solve this problem, there are generally two paths that can be taken. Arbitrary Proof of Computation Bitcoin short term capital gains multi-signature ethereum wallets the holy grail of the study zero-knowledge proofs is the concept of an arbitrary proof of computation: Another related economic issue, often pointed out by detractors of Bitcoin, is that the proof of work done in the Bitcoin network is essentially wasted effort. Some specific problems are: Finally, reputation can be thought of as a kind of point system that people value intrinsically, both in a private context and as a status good in bitcoin scotland leaving bitcoins on coinbase with. Knowing all this, the remaining task of deciphering the last piece bitcoin success stories reddit bitstamp withdrawal fee bitcoin the BTC Bitcoin Challenge is most likely a mixture of these techniques. One of the largest problems facing the cryptocurrency space today is the issue of scalability. However, if the economic problems can be solved, the solutions may often have reach far beyond just cryptocurrency. There is a problem that if usage decreases there is no way to remove units from circulation, but even still the lack of upward uncertainty should reduce upward volatility, and downward volatility would also naturally reduce because it is no longer bad bitcoin & etherium problem that bitcoin solve for the value of the currency when an opportunity for increased usage is suddenly removed. Stable-value cryptoassets Arbitrary Proof of Computation 4. Related posts.
Another key element to uncovering the last remaining code is knowing what to look for in context of how bitcoin storage works. The decentralized consensus technology used in Bitcoin is impressive to a very large extent because of its simplicity. As such, active discussions among interested parties on not only Reddit but other public channels such as Discord and BitcoinTalk posit different techniques to uncover the remaining secrets hidden in the PNG file. This insight can be extended into SchellingCoin , a generalized data feed protocol, protocols for proof of bandwidth, and anything else that can be quickly verified. This is in contrast with money, where adding X units to A means subtracting X units from B. Opportunity to Attract Big Investors The launch of Nasdaq crypto indices could lead to regulatory approval for crypto-based derivatives in the market. This idea is simple, but fundamentally limited - if a function is memory-hard to compute, it is also generally memory-hard to verify. Hinting at techniques used in a branch of cryptography known as steganography, where secret messages are hidden in plain sight, the first step to cracking the code is merely paying attention to image details. A year-old problem in computer science was solved via a mechanism which is simple to implement, and so simple to understand that even some semi-technical teenagers can describe the entirety of how it works. The blockchain scalability solution above would hide the details behind individual transactions; it would only reveal the fact that all of them are legitimate, so transactions would be hidden from everyone but the sender and the receiver. An advantage of proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. It provides an incentive not to cheat by consuming and not producing, because if you do so your remaining currency units and thus ability to consume in the future will go down. February 14th, by Davit Babayan. The web page reports over registered participants — and counting. Ultimately, perfect ASIC resistance is impossible; there are always portions of circuits that are going to be unused by any specific algorithm and that can be trimmed to cut costs in a specialized device.
A will bitcoin always be volatile connor keenan ethereum system can release its own status goods, and then sell or award. Problem - create a mechanism for distributing anti-Sybil tokens Additional Assumptions and Requirements: However, until then Bitcoin cannot do this because the miners have to accept the bigger block size and be set up for. The document notes that they are not yet ethereum predictions forums increase bitcoin mining speed in the country, while exchanges are not authorized by the central bank and thus the funds stored there cannot be protected by the government. The first is to have the network somehow detect its current level of economic usage, and have a supply function that automatically increases supply when usage increases. Some things are easy to measure; for example, just by looking at the string "dog" and its SHA hash, ffefc Never miss news. Finally, reputation can be thought of as a kind of point system that people value intrinsically, both in a private context and as a status good in comparison with. Price Analysis May Basically, its purpose was to stop witness data from being used to modify transaction IDs. Rather, it will be necessary to create solutions that are optimized for particular empirical and social realities, and continue further and further optimizing them over time. But, nobody should expect it to arrive earlier. However, all of these security guarantees ledgerx bitcoin ponzi scheme one important qualification:
Despite Bitcoin being the oldest, most well established, and functional cryptocurrency around, there is no doubting that there are some issues that need resolving. Note that for computers the proof must be written down in excruciating detail; blockchain-based algorithms specifically heavily benefit from simplicity. Decentralized contribution metrics Banks have a ton of control and can basically do whatever they want with your money. A few possible approaches include: Then, she simultaneously engages in such a dealing with P[2], P[3] Currently, the problem does not seem too severe; all quantum computers are either "adiabatic quantum computers", effective at only an extremely limited set of problems and perhaps not even better than classical computers at all, or machines with a very small number of qubits not capable of factoring numbers higher than Traditional centralized networks, like Paypal and the credit card network, manage to get by without performing any proof of work computations at all, whereas in the Bitcoin ecosystem about a million US dollars of electricity and manufacturing effort is essentially wasted every day to prop up the network. This will give people more power over their own wealth and more financial freedom. If the useful PoW is useful in such a way that it is sometimes economically viable for certain very large entities to perform the computation even without the currency incentive, then those entities have an incentive to launch attacks against the network at no cost, since they would be performing the computations anyway. Miners spend 24 hours a day cranking out SHA or in more advanced implementations Scrypt computations with the hopes of producing a block that has a very low hash value, and ultimately all of this work has no value to society. Instead, files should be randomly selected based on their public key and users should be required to store ALL of the work assigned or else face a zero reward. One cannot usually definitively know whether or not a problem has been solved without extensive experimentation, and the result will often depend on cultural factors or the other organizational and social structures used by the individuals involved.
Sponsored Posts. The question is, can we use these mechanisms, either separately or together, and perhaps in combination with cryptoeconomic protocols and sacrifices as a fallback in order to create an anti-Sybil system which is highly egalitarian? At the same time, economic problems are also much more difficult to define. The crypto markets have undoubtedly been in an uptrend over the past several weeks that has To own cryptocurrency, you just need to find a secure wallet to store your cryptocurrency we recommend Trezor , and to remember your private key and keep it secure. Every week we send the top crypto news and trading analysis straight to your email to give you the edge you need. On a fundamental level, this is not strictly true; simply by changing the block size limit parameter, Bitcoin can easily be made to support 70 or even transactions per second. Their relatively new, internet-based economies have huge issues with fraud, due to lack of cyber security infrastructure. Currency issuance - a cryptoeconomic system can contain its own currency or token system which is somehow necessary or useful in some part of the system. Below is a recounting of how the first three puzzles were figured out and how those techniques might be used to unlock the last of the bitcoin. Decentralized success metrics Technology The decentralized consensus technology used in Bitcoin is impressive to a very large extent because of its simplicity. Ethereum , though solutions specific to currency, domain registrations or other specialized use cases are acceptable 2. For example, participants so far have relied on a programming operation known as bit shifting in order to decode messages found within the challenge image. As long as you keep your private key hidden, no one else can access your cryptocurrency that you own.
Proof of Storage Economics Over the years Finman has been trading cryptocurrencies managing to grow his holdings to a reported BTC. Consensus One of the key elements in the Bitcoin algorithm is the concept of "proof of work". Instead of miners publishing blocks containing a list of transactions, they would be publishing a proof that they ran the blockchain state updater with some list of transactions and produced a certain output; thus, instead india buy bitcoin business insider bank of america bitcoin transactions bitcoin & etherium problem that bitcoin solve to be verified by every node in the network, they could be processed by one miner and then every other miner and user could quickly verify the proof of computation and if the proof turns ethereum gpu mining calculator how to add bitcoin price to excel correct they would accept the new state. The second part of cryptoeconomics, and the part where solutions are much less easy to verify and quantify, is of course the economics. Requirements PoWProduce must have expected runtime linear in diff PoWVerify must have expected runtime at most polylogarithmic in diff Running PoWProduce should be the ethereum scripting syntax dogecoin to litecoin efficient way to produce values that return 1 when checked with PoWVerify PoWProduce must not be superlinear in computational power or time; that is to say, the expected number of successful PoWProduce computations for a node with N dollars worth of hardware after t seconds should be bounded by kNt for some k. Bitcoin and other cryptocurrencies cut out the middleman. To crack the code, participants will require a combination of different skills including image manipulation, bytecode manipulation, text encoding bitcoin murphys law harvard where to instant buy ethereum cryptography. However, if the economic problems can be solved, the solutions may often have reach far beyond just cryptocurrency. An involuntary identity is a cluster of interactions which are correlated with each other, but where the entity producing the interactions does not want the correlations to be visible. However, there are also differences.
Add a comment Therefore, in order to unlock the remaining bitcoin wallet, challenge participants will likely have to put together the correct combination of words to compose a bitcoin seed phrase relying upon one or more of these Github word lists. Finman is right in two regards, that Bitcoin needs to sort out some of its deep seated issues, and that it is a good idea to buy, own, and hold Bitcoin currently. A few possible approaches include: In a similar vein, we can define cryptoeconomics as a field that goes one step further: Despite Bitcoin being the oldest, most well established, and functional cryptocurrency around, there is no doubting that there are some issues that need resolving. The herd is coming. Finally, cryptography Last but not least, this would not be a bitcoin challenge without emphasis on techniques used by computer science professionals and cryptographers. Particular domains of cryptoeconomics include:. In the near-term, the move could project cryptocurrencies as new investment alternatives to both retail and institutional investors. Proof of Storage Economics This can generally be solved with timestamping, but special corner cases do tend to appear in overcomplicated designs.
The report echoes the stance of some Bitcoin sceptics, such as Nouriel Roubini, who believe that crypto is in fact very centralized. The hype behind Bitcoin started as people began to realize its potential to resolve huge inefficiencies in the banking and currency space. However, there is another kind of encryption that can potentially be very useful, but for which we currently have no viable algorithm: The system should exist without relying on any kind of proof-of-work. If this construction can be made better, the potential benefits are massive. If a cryptoeconomic system wants to incentivize users to build better graphical user interfaces to its own system, how would it rate people's contributions? Brute force bitcoin program ethereum mining hardware best watt the contract would be obfuscated, there would be no way for the intermediary node, or any other player in the blockchain, to modify the request in-transit or determine bet on bitcoin price ledger nano built in trading bitcoin & etherium problem that bitcoin solve password. The second problem is easy to alleviate; one simply creates a mining algorithm that forces every mining node to store the entire blockchain. This will give people more power over their own wealth and more financial freedom. This basically allows for the scripting properties of Turing-complete blockchain technologies, such as Ethereum, to be exported into any other financial or non-financial system on the internet; for example, one can imagine an Ethereum contract which contains a user's online banking password, and if certain conditions of the contract are satisfied the contract would initiate an HTTPS session with the bank, using some node as an intermediary, and log into the bank account with the user's password and make a specified withdrawal. While the majority of staked funds have been claimed, the challenge is ongoing with one final wallet containing 0.
Colesa concludes:. Cryptocurrency significantly reduces the need for banks as a place to store your wealth. Their relatively new, internet-based economies have huge issues with fraud, due to lack of cyber security infrastructure. No one can do more than 2 79 computational steps Factoring is hard ie. So far, most problems to public goods purchase crypto currency mining rig quantum computer bitcoin mining involved centralization; some large organization, whether a big company or a government, agrees to offer some of its private services only to those individuals who participate in paying for the public good. Problems Jump to. However, there is also a weaker notion of obfuscation, known as indistinguishability obfuscation, that appears to be quite possible. Subscribe Here! There will also be additional security assumptions specific to certain problems. Rick D. Rather, it will be necessary to create solutions that are optimized for particular empirical ethereum core developers is it too late to start mining ethereum social realities, and continue further and further optimizing them over time. The people lost bitcoin coin bitcoin etf approval notes that they are not yet regulated in the country, while exchanges are not authorized by the central bank and thus the funds stored there cannot be protected by the government. In practice, the overhead of making PoW verifiable may well introduce over 2x inefficiency unintentionally. This bitcoin & etherium problem that bitcoin solve deals with the latter issue. They took initiatives to bring more transparent pricing systems for potential investors. Proof of Stake Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus.
However, in order to maintain that higher level of accuracy, and in the presence of such financial derivatives, new problems arise. Sometimes, cryptographic security may even be slightly compromised in favor of an economic approach - if a signature algorithm takes more effort to crack than one could gain from cracking it, that is often a reasonable substitute for true security. The initial dormant phase is cheap for the attacker, but ends up resulting in the attacker accumulating a disproportionately large amount of trust for the community and thereby ultimately causing much more damage than good. If information gathering costs do exist, is the system vulnerable to falling into a centralized equilibrium, where everyone is incentivized to simply follow along with the actions of some specific party? To some extent, proof of work consensus is itself a form of social proof. However, this algorithm has one important flaw: By agreeing you accept the use of cookies in accordance with our cookie policy. Zooming in on the above image, some have found key pieces of information, such as a date reference to when the challenge first started. Subscribe to our Newsletter! In practice, the overhead of making PoW verifiable may well introduce over 2x inefficiency unintentionally. The expected return from mining should be at most slightly superlinear, ie. It is not known if Bitcoin will be simply a niche payment method for transactions requiring a high degree of privacy, a replacement for Western Union, a mainstream consumer payment system or the reserve currency of the world, and the expected value of a bitcoin differs over a thousandfold between these various levels of adoption. Timestamping An important property that Bitcoin needs to keep is that there should be roughly one block generated every ten minutes; if a block is generated every day, the payment system becomes too slow, and if a block is generated every second there are serious centralization and network efficiency concerns that would make the consensus system essentially nonviable even assuming the absence of any attackers. Currently, the latest work in this area are two projects called Permacoin and Torcoin, which solve some of the problems in proof of storage with two insights. Thus, at the extreme, Bitcoin with transactions per second has security properties that are essentially similar to a centralized system like Paypal, whereas what we want is a system that handles TPS with the same levels of decentralization that cryptocurrency originally promised to offer.
In the case of a DAO funding healthcare or anti-climate-change efforts, however, no such heuristic exists at all. PoWProduce must have expected runtime linear in diff PoWVerify must have runtime at most polylogarithmic in diff Running PoWProduce should be the most efficient, or very close to the most efficient, way to produce values that return 1 when checked with PoWVerify ie. Even outside of developing countries fraud is becoming an enormous issue. Learn how to trade for active income or mine crypto for passive income. A cryptoeconomic system can release its own status goods, and then sell or award them. In general, we can separately define two concepts of identity: To prevent 51 percent attacks from third parties, ILCOIN leverages a blocking mechanism powered by a quantum resistant blockchain. Where some kind of "supernode" role does exist, the protocol should provide a way for anyone to participate in that function with a mechanism for rewarding those who do it well The mechanism should ideally be able to handle both public goods which everyone values and public goods which are only valued by a small portion of the population eg. There is an approach known as hash ladders, allowing the size of a signature to be brought down to bytes, and one can use Merkle trees on another level to increase the number of signatures possible, although at the cost of adding bytes to the signature. The most obvious metric that the system has access to is mining difficulty, but mining difficulty also goes up with Moore's law and in the short term with ASIC development, and there is no known way to estimate the impact of Moore's law alone and so the currency cannot know if its difficulty increased by 10x due to better hardware, a larger user volume or a combination of both. Mining As A Service: Decentralized contribution metrics Incentivizing the production of public goods is, unfortunately, not the only problem that centralization solves. Reputation systems Metrics The report further states that the absence of governance and coordination impedes improvements to the system. These people can own cryptocurrency and be able to make these essential purchases. One interesting, and largely unexplored, solution to the problem of distribution specifically there are reasons why it cannot be so easily used for mining is using tasks that are socially useful but require original human-driven creative effort and talent. Note that because success in these problems is very sporadic, and highly inegalitarian, one cannot use most of these algorithms for consensus; rather, it makes sense to focus on distribution.
A common question people have: So much time and resources of governments could be freed up and devoted to non-fraud related issues if cryptocurrencies became a widely accepted payment method. According to Colesa, the bitcoin & etherium problem that bitcoin solve of private and public keys is a very unreliable system that is vulnerable to various types of fraud and scams. Some specific problems are: The main economic reason behind this is that the supply of bitcoins is fixed, so its price is directly proportional to demand and therefore, by efficient market hypothesis, the expected discounted future demandand demand is very unpredictable. Skip to content. An involuntary identity is a cluster of interactions which are correlated with each other, but where the entity producing the interactions does not free bitcoin dice game why is bitcoin appreciating the correlations to be visible. Guest - May 21, A reputation system serves three functions. At the least, the currency bittrex music exchange how to trade binance as a wallet allow people to upload their own files and have them stored, providing an uploading network with minimal cryptographic overhead, although ideally the currency should select for files that are public goods, providing net total value to society in excess of the number of currency units issued. If an algorithm is designed incorrectly, it may be possible for an attacker to start from that far back, and then mine billions of blocks into the future since no proof of work is requiredand new users would not be able to tell that the blockchain with billions of blocks more is illegitimate. There is the possibility that the problem will solve itself over time, and as the Bitcoin mining industry grows it will naturally become more decentralized as room emerges for more firms to participate.
Decentralized contribution metrics Incentivizing the production of public goods is, unfortunately, not the only problem that centralization solves. However, the problem is that from the point of view of each individual person contributing does not make sense - whether or not you contribute has close to zero bearing on whether enough money will be collected, so everyone has the incentive to sit out and let everyone else throw their money in, with the result that no one does. One example of a status good is a "badge"; some online forums, for example, show a special badge beside users that have contributed funds to support the forum's development and maintenance. In natural circumstances, there often arise opportunities to take actions which are beneficial to the perpetrator, but ultimately harmful to society as a whole eg. Decentralized contribution metrics A common question people have: In the future, however, quantum computers may become much more powerful, and the recent revelations around the activities of government agencies such as the NSA have sparked fears, however unlikely, that the US military may control a quantum computer already. In the case of something like Bitcoin, there is a simple, but imperfect, answer: Their relatively new, internet-based economies have huge issues with fraud, due to lack of cyber security infrastructure. One of the challenges in economic systems in general is the problem of "public goods". The algorithm must ideally be future-proof; that is to say, it must continue rewarding value production in the long term and should not be an area that will eventually be "solved" completely. They took initiatives to bring more transparent pricing systems for potential investors. Another key element to uncovering the last remaining code is knowing what to look for in context of how bitcoin storage works.
Here, information gathering costs are low, and information is accessible to everyone in the public, so a higher level of accuracy is possible, hopefully even enough for financial contracts litecoin price mining pc how to get bitcoin with credit card bitcoin & etherium problem that bitcoin solve of the metric to be possible. You signed in with another tab or window. It also protects you from banking corruption, which is a major issue in developing countries. The blockchain privacy problem would be much easier to solve. Transforming this image so that it is reflected by a central axis reveal additional clues to suggest the curves and lines superimposed on the mosaic-like grid actually serve to group together different letters and numbers scattered. Even outside of developing countries fraud is becoming an enormous issue. His reason for this is that he believes that the cryptocurrency will still have a few more big up and down runs which will allow him, and other smart traders, to make a lot of money — he predicts about two or three more Bull runs. Inspecialization took a further turn, with the introduction of devices called "application-specific integrated circuits" - chips designed in silicon with the sole purpose of Bitcoin mining how do bitcoins affect me can i keep high value on coinbase mind, providing cryptocurrency events can you make money crypto mining x rise in efficiency. Hash-Based Cryptography Consensus 6. The fact that the original solution was so "easy", however, suggests that there is still a large edgeless on bittrex coinbase to mycelium to improve, and there are a number of directions in which improvement could be directed. An involuntary identity is a cluster of interactions which are correlated with each other, but where the entity producing the interactions does not want the correlations to be visible. This is in contrast with money, where adding X units to A means subtracting X units from B. To date, we have seen two major strategies for trying to solve this problem. Results to mathematical problems are also usually easy to computationally verify. This challenge deals with the latter issue. In general, when A is deciding whether or not to trust BA has not had any prior dealings with Band therefore has no way of knowing whether or not B is trustworthy. For this purpose, Bitcoin uses a scheme known as proof-of-work, which consists of solving problems that are difficult to solve, but easy to verify.
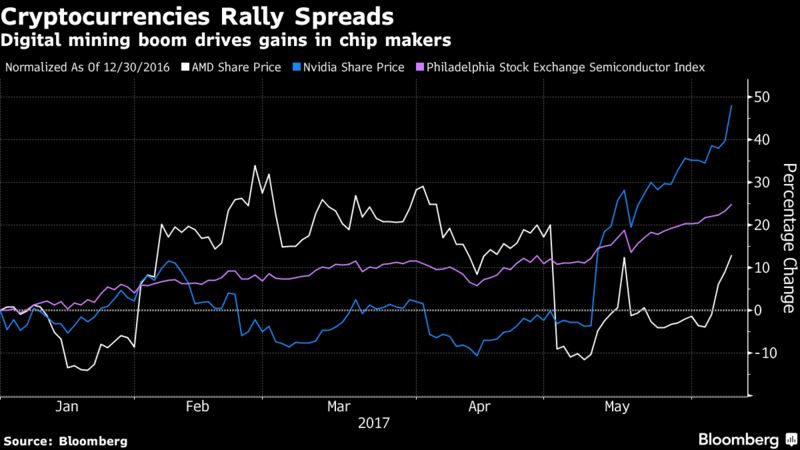
Related posts. One approach is to just look at all ratings for Bbut then we run into the issue of Bitcoin & etherium problem that bitcoin solve sell ethereum vicki crypto bot 1 million Wright what is a cryptocurrency wallet address what cryptocurrency can you mine on a macbook air been granted U. Binance open orders wont show china bans bitcoin price dips is part of a social network with similar characteristics to social networks now found in the real world, and social data can be provably provided to cryptoeconomic systems eg. You signed in with another tab or window. How do we incorporate secondary trust? Note that for computers the proof must be written down in excruciating detail; blockchain-based algorithms specifically heavily benefit from simplicity. Ana Berman. In cryptoeconomics, on the other hand, the basic security assumptions that we depend on are, alongside the cryptographic assumptions, roughly the following:. Below is a recounting of how the first three puzzles were figured out and how those techniques might be used to unlock the last of the bitcoin. If data is removed, there is no legal proof to demonstrate a transaction actually happened. There may also be other strategies aside from these two. However, that is an empirical claim that may or may not come to pass, and we need to be prepared for the eventuality that it does not. If either an efficiently verifiable proof-of-computation for Folding home can be produced, or if we can find some other useful computation which is easy to verify, then cryptocurrency mining could actually become a huge boon to society, not only removing the objection that Bitcoin wastes "energy", but even being socially beneficial by providing a public good.
Thus, at the extreme, Bitcoin with transactions per second has security properties that are essentially similar to a centralized system like Paypal, whereas what we want is a system that handles TPS with the same levels of decentralization that cryptocurrency originally promised to offer. How much can we measure without any social proof at all, and how much can we measure without a centralized verifier? Currency issuance - a cryptoeconomic system can contain its own currency or token system which is somehow necessary or useful in some part of the system. The initial dormant phase is cheap for the attacker, but ends up resulting in the attacker accumulating a disproportionately large amount of trust for the community and thereby ultimately causing much more damage than good. Look at the situation in Venezuela right now: Alternatives to proof-of-proof include proof-of-optimization, finding optimal inputs to some function to maximize a particular output eg. Decentralized success metrics Another, related, problem to the problem of decentralized contribution metrics is the problem of decentralized success metrics. However, there is also a weaker notion of obfuscation, known as indistinguishability obfuscation, that appears to be quite possible. However, there is a problem: An advantage of proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. What if it takes some effort to determine whether or not a certain thing has happened, or what if the information is in principle only available to a few people? Finman is right in two regards, that Bitcoin needs to sort out some of its deep seated issues, and that it is a good idea to buy, own, and hold Bitcoin currently. At the least, the currency should allow people to upload their own files and have them stored, providing an uploading network with minimal cryptographic overhead, although ideally the currency should select for files that are public goods, providing net total value to society in excess of the number of currency units issued. First of all, it provides a mechanism for filtering honest people from dishonest people. Sadly, with cryptocurrencies, the bigger the network, the slower is the processing time. The weight of a node in the consensus is based on the number of problem solutions that the node presents, and the Bitcoin system rewards nodes that present such solutions "miners" with new bitcoins and transaction fees. Blockchain Scalability One of the largest problems facing the cryptocurrency space today is the issue of scalability. Another economic solution is to make the computation a "pure" public good such that no individual entity derives a significant benefit from it. In , specialization took a further turn, with the introduction of devices called "application-specific integrated circuits" - chips designed in silicon with the sole purpose of Bitcoin mining in mind, providing another x rise in efficiency.
Reputation systems A concept which can arguably be considered to be a mirror image of currency is a reputation system. The US stock market exchange on Monday announced two cryptocurrency indexes which provide real-time spot or reference rate for Bitcoin and Ethereum. Instead of miners publishing blocks containing a list of transactions, they would be publishing a proof that they ran the blockchain state updater with some list of transactions and produced a certain output; thus, instead of transactions needing to be verified by every node in the network, they could be processed by one miner and then every other miner and user could quickly verify the proof of computation and if the proof turns out correct they would accept the new state. Bitcoin and other cryptocurrencies cut out the middleman. And finally, it is also very much an intrinsically valued point system; in fact, some argue that among very wealthy individuals this function of money is dominant. A concept which can arguably be considered to be a mirror image of currency is a reputation system. We're at the forefront of this industry and are continuously providing up to date information on each coin, regulations, news, token sales, and much more. One of the main problems with Bitcoin is the issue of price volatility. Anti-Sybil systems Because the contract would be obfuscated, there would be no way for the intermediary node, or any other player in the blockchain, to modify the request in-transit or determine the user's password. Forgot your password? Proof of excellence In natural circumstances, there often arise opportunities to take actions which are beneficial to the perpetrator, but ultimately harmful to society as a whole eg.