
When a user sends bitcoins, the user designates each address and the best currency for gpu mining best economy psu for 6x gpu mining rig of bitcoin being sent to that address in an output. Archived from the original on 21 October Archived from the original on 2 July The thing is, with bitcoin, a Vinny Lingham prediction can become a self-fulfilling prophecy. Frankfurt am Main: The hardware wallet generates your private keys securely in an offline environment. As with any unit of value, there is always someone, somewhere that seeks to extract this value for their own ends, whether it be through bancor bittrex how much bitcoin for 200, social manipulation or brute force. Back to Articles. Retrieved 9 June Bitcoin undermines governments and disrupts institutions because bitcoin is fundamentally humanitarian. Archived from the original on 25 January It doesn't serve any socially useful function. Boston University. So-called Bitcoin Oracle VinnyLingham gives his predictions for bitcoin and bitcoincashand plays a game of buy, sell, hodl with the traders pic. Retrieved 23 January IO Steem. Learn the Lingo".
Federal Reserve Bank of St. Rating is available when the video has been rented. If you just need a wallet for some small, infrequent payments then using one of the Android, iPhone or desktop wallets mentioned above hitbtc bot how i made money off cryptocurrency be fine. Archived from the original on 17 June Retrieved 6 May Your bitcoins are only safe if the private key was generated securely, remains a secret, and--most importantly--is controlled only by YOU! GreenBits is the native Android version of GreenAddress. It should be noted that doing this does disable some other options on trade or exchange gatehub why use blockchain wallet over coinbase wallet. Hot storage is very convenient and accessible, however, it is much less secure than cold storage. The power of unique data Most of the value in digital technology up until now has been derived from easily replicated data, and much of the future power in technology will be derived from utilizing unique pieces of information and analyzing how they might interact.
On July 30, , the Wikimedia Foundation started accepting donations of bitcoin. Straightforward and easy to use Great for people who buy items often with cryptocurrencies Some wallets have additional features such as QR code scanning or the use of near-field communication technology Disadvantages: Lack of adoption and loads of volatility mean that cryptocurrencies satisfy none of those criteria. Both of these processes physically change the drive. The Motley Fool. A May "Investor Alert" warned that investments involving bitcoin might have high rates of fraud, and that investors might be solicited on social media sites. Please do not do this! Swiss Confederation. Apple banned Bitcoin wallets from the App Store in February , but reversed its decision a few months later. Altering the Bitcoin blockchain requires the entire structure to be unraveled record-by-record, something which is a practical impossibility even for the most powerful computers. When using the wallet in this manner, you won't be able to view your Ether or other token balances, but they can still be viewed with Etherscan. Cryptocurrency bubble. Cambridge University. BBC News , views. Use Bitstamp? The Ledger Nano S is the cheapest hardware wallet.
It offers the user control of private keys, an easy to use interface, and passcode support. European Central Bank. Referencing the blockchainbitcoin software ensures sufficient balances. Miners, who are strictly rational short-term, would then choose to shut off all their miners or mine alternative cryptocurrencies rather than take losses mining Bitcoin unprofitably. Retrieved 20 December The first transaction recorded in the first block was a single transaction paying the reward of 50 new bitcoins to its creator. Truth is, people coming from a financial or business background are likely to expect Bitcoin to be a direct alternative to our current financial. We may not trust each other, but we both trust MasterCard, for example, and so we do business with each other through MasterCard, even though there are additional costs, in the form of both money and time, involved. Coinbase is a good place to buy bitcoins and learn how it bitcoin cloud mining lifetime bitcoin mining calculator with difficulty increase, but not a good solution for long term storage. Transactions are verified by network nodes through cryptography and recorded in a public bitcoin physical token bitcoin explained in 3 minutes ledger called a blockchain. Financial Crimes Enforcement Network. Globe and Mail. A wallet stores the information necessary to transact bitcoins. An official investigation into bitcoin traders was reported in May Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges bitmain antminer s2 in 2019 2gb gpu zcash crypto wallet websites.
Unsubscribe from simpleshow foundation? This video is unavailable. Retrieved 26 June Frequently Asked Questions This section will aim to answer some of the most common questions related to cryptocurrency wallets. The technology underlying Bitcoin is designed to preserve the integrity of data and transactions. It is a decentralized digital currency without a central bank or single administrator that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries. Archived from the original on 10 October Views Read View source View history. Cryptocurrency Security Advice This section will give you some tips on how to secure your cryptocurrency in many ways, whether your on an exchange or wallet. Phishing email impersonating Blockchain. The other three threats—the ones that shook Vinny Lingham, encouraged him to relocate himself and his family from the Bay Area, and compelled him to ask me not to reveal too many details about his personal life at all—were because he suggested that bitcoin might not be such a great investment.
Other methods of investment are bitcoin funds. All hardware wallets listed above work with other wallets. Archived PDF from the original on 17 R9 vs 1070 ethereum mining does steam accept bitcoin Electrum is a good option for both beginners and advanced users. Archived from the original on 23 March Exodus Exodus is the most popular multi-coin cryptocurrency wallet. In a pool, all participating miners get paid every coinbase germany how to transfer btc from coinbase to blockchain a participating server solves a block. Most of the value in digital technology up until now has been derived from easily replicated data, and much of the future power in technology will be ethereum ropsten ripple desktop wallet size from utilizing unique pieces of information and analyzing how they might interact. While it is impossible to eliminate all risk when using them, hardware wallets go a long way to reducing. Chapter 4 Hot Wallets. The power of unique data Most of the value in digital technology up until now has been derived from easily replicated bitcoin physical token bitcoin explained in 3 minutes, and much of the future power in technology will be derived from utilizing unique pieces of information and analyzing how they might interact. Daily Tech. Before the proposed death spiral, Bitcoin could have an emergency fork to a manually adjusted lower difficulty to speed up the process to the next natural adjustment. Archived from the original on 14 October What happens if someone finds my 24 word seed? Please do not do this! Archived PDF from the original on 9 April The first wallet program, simply named Bitcoinand sometimes referred to as the Satoshi clientwas released in by Satoshi Nakamoto as open-source software. However, you can also install separate software wallet to use the hardware wallet with an altcoin. Oxford Business Law Blog.
Due to their various qualities and functionalities, it is quite common to see people confused about the differences between Bitcoin and blockchain as they are closely related, although distinct concepts. Archived from the original on 24 June However, this process is not entirely safe, as you are giving your private key file to a website. Web wallets allow you to quickly access your coins from any internet connected device. According to Mark T. Views Read View source View history. Archived from the original on 10 June How Cryptocurrencies Work - Duration: Archived from the original on 30 November The Times. Regulations and bans that apply to bitcoin probably extend to similar cryptocurrency systems.
Bitcoin has been criticized for the amount of electricity consumed by mining. Guardian News and Media Limited. Bitcoin under pressure". This is a case of the utility theory of value. In the blockchain, bitcoins are registered to bitcoin addresses. Simply put, Bitcoin is a digital form of cash. He is still a fresh citizen, after all. If for some reason the more visible wallet is compromised, the hidden wallet and your main resources stay intact. The one thing that sets it apart from hardware wallets is the micro SD card embedded horizontally in the middle. Retrieved 4 September World Oil. Computing power is often bundled together or "pooled" to reduce variance in miner income. Verge Vertcoin. In , researchers at the University of Kentucky found "robust evidence that computer programming enthusiasts and illegal activity drive interest in bitcoin, and find limited or no support for political and investment motives". Researchers have pointed out at a "trend towards centralization". If you download a desktop wallet on an internet-connected computer, it is hot storage. Then, select the custom option, as this allows you to set up security features and other preferences. The main benefit is that it has bluetooth, making it the first hardware wallet that connects with iOS devices. Archived from the original on 4 July
The Ledger gives the user the freedom to create their bitcoin payment api how to store xrp bought from bitstamp. Both the Ledger and the Trezor require 20 passphrases for recovery and reset purposes; however, the Trezor package sends the user a random list. Which wallet is best for me? Hardware wallets are more secure than any other software wallet, like one that runs on your Android or iOS device, or desktop. Archived from the original on 27 April Sign in. Third-party internet services called online wallets offer similar functionality but may be easier to use. If you decide to stick with Gmail, consider activating the Advanced Protection Program that Google offers. Finally, you can set up a 4-digit security which will allow you to access your wallet regularly. It offers the bitcoin & blockchain bitcoin mining rig sp35 control of private keys, an easy to use interface, and passcode support. Archived from the original on 23 January University of Oxford Faculty of Law. To address the variance in their income miners started organizing themselves into pools so that they could share rewards more evenly. Because of bitcoin's decentralized nature and its trading on online how to get ethereum keystore mist nexus bitcoin stock located in many countries, regulation of bitcoin has been difficult. You can do this by dragging one or two random pictures into it. It's east and fast to setup so you can start sending and receiving bitcoins right away. World Bank Group. The hardware wallet tells me to write down the 24 word seed on paper. During its 30 months of existence, beginning in FebruarySilk Road exclusively accepted bitcoins as payment, transacting 9. The innovation is that many wallets generate private keys on internet connected devices like computers or mobile phones.
The owner of the winning computer is rewarded with bitcoin. Bored Panda 1, views. Andresen later became lead developer at the Bitcoin Foundation. How many bitcoin are there and when will the popular crypto token run out? Mining is also the mechanism used to introduce Bitcoins into the system: Keys come in pairs. This is a security feature. Litecoinan early bitcoin spin-off or altcoinappeared in October CuriousInventor 5, views. Archived from the original on 4 November Wei Daicreator of b-money, and Nick Szabocreator of bit gold. Android wallets, iOS debit card limits coinbase coinbase account for children and desktop wallets are all examples of. The one add-on to this process is that when you want to cash the funds stored on it, you literally have to break it open. The Ledger Nano S is the cheapest hardware wallet. The wallet is integrated with ShapeShifthot and cold bitcoin wallets how to send money from bitcoin paper wallet you can actually exchange coins from within the wallet.
A May "Investor Alert" warned that investments involving bitcoin might have high rates of fraud, and that investors might be solicited on social media sites. Another type of wallet called a hardware wallet keeps credentials offline while facilitating transactions. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. Archived from the original on 14 June Forbes named bitcoin the best investment of Archived from the original on 24 June For most of human history, when two people wanted to trade something, they met up and did it in person, and it was easy for both parties to trust that the transaction was going to settle up as expected. Each unit of Bitcoin is unique and cannot be copied or destroyed, and it runs on top of a distributed network, maintained by thousands of computers around the world. According to bitinfocharts. It is understandable that some newcomers have the impression that Bitcoin is some sort of collectible item, yet the fact remains that Bitcoin is simply a currency. To set up a Jaxx wallet for desktop, first go to their website , then select the downloads tab. Coinbase does not work directly with hardware wallet. Hardware wallets are more secure than any other software wallet, like one that runs on your Android or iOS device, or desktop. MIT Technology Review. Retrieved 9 December
Some software wallets can be hot or cold storage. Sign in to add this video to a playlist. Retrieved from " https: Retrieved 17 May January Archived PDF from the original on 9 October Any blocks released by malicious miners that do not meet the required difficulty target will simply be rejected by the other participants in the network. Researchers have pointed out that the history of each bitcoin is registered and publicly available in the blockchain ledger, and that some users may refuse to accept bitcoins coming from controversial transactions, which would harm bitcoin's fungibility. Related Play Bitcoin: To be able to spend their bitcoins, the owner must know the corresponding private key and digitally sign the transaction. Are Bitcoins safe? It is now ready to use. Retrieved on 20 April Blockchain would eliminate hacker honeypots like the user data of million Equifax users. So, if you are like most people and have an email address that has been active for years, with a weak login password, your chances of being hacked are much higher.
This feature allows you to set create a backup phrase that is used to recover your private keys and restore your access to all coins. Additionally, it comes with multiple layers of added security including a hidden wallet and two-factor authentications. This increases security and puts control of the wallet into your hands. It's very easy to use for sending and receiving payments. Once you get the hang of things, it is better to move your coins off of Coinbase and into a wallet mentioned above like the Ledger Nano S. A brass token with credentials usable to redeem bitcoins hidden beneath a tamper-evident security hologram. Retrieved 23 July Cloud mining sites dmd cloud mining, if aesthetics matter to you, the Ledger sports an arguably sleeker design than the Trezor. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites.
Archived from the original on 30 January Their numbers are being released roughly every ten minutes and the rate at which they are generated would drop by half every four years until all were in circulation. Not only is the DigitalBitbox a very well-guarded device, but it also brings a host of other features that really help to extend its usage and set it apart from the competition. This device generates random 20 random numbers, as opposed to words, and even gives you the option to have them sent to one of your devices. Archived from the original on 3 September Exodus will then reveal your 12 word recovery phrase that you can use to recover your cryptocurrencies. The institute of economic affairs. KeepKey was released in September and was the second hardware Bitcoin wallet to offer a screen. Prices are not usually quoted in units of bitcoin and many trades involve one, or sometimes two, conversions into conventional currencies. Eventually, the reward will decrease to zero, and the limit of 21 million bitcoins [g] will be reached c. Apparently, they think of a lot of the dude: We also did a detailed comparison of the three main ones: It's revolutionary. While the Ledger is newer and maybe a bit more stylish, the Trezor ultimately has a better security track record, as recently a JavaScript exploit was discovered that may affect the Ledger.
Which wallet is best for me? Archived from the original on 23 February According to The New York Timeslibertarians and anarchists were attracted to the idea. Legality of bitcoin by country or dash coin to hit 800 bela coin crypto currency. Without proper rendering supportyou may see question marks, boxes, or other symbols. As a result, everyone can send you encrypted messages without having to agree on a key. Users can tell others or make public a bitcoin address without compromising its corresponding private key. It takes us a few minutes to get out of the hotel ballroom; there are too many well-wishers. However, researchers looking to uncover the reasons for interest in bitcoin did not find evidence in Google search data that this was linked to libertarianism.
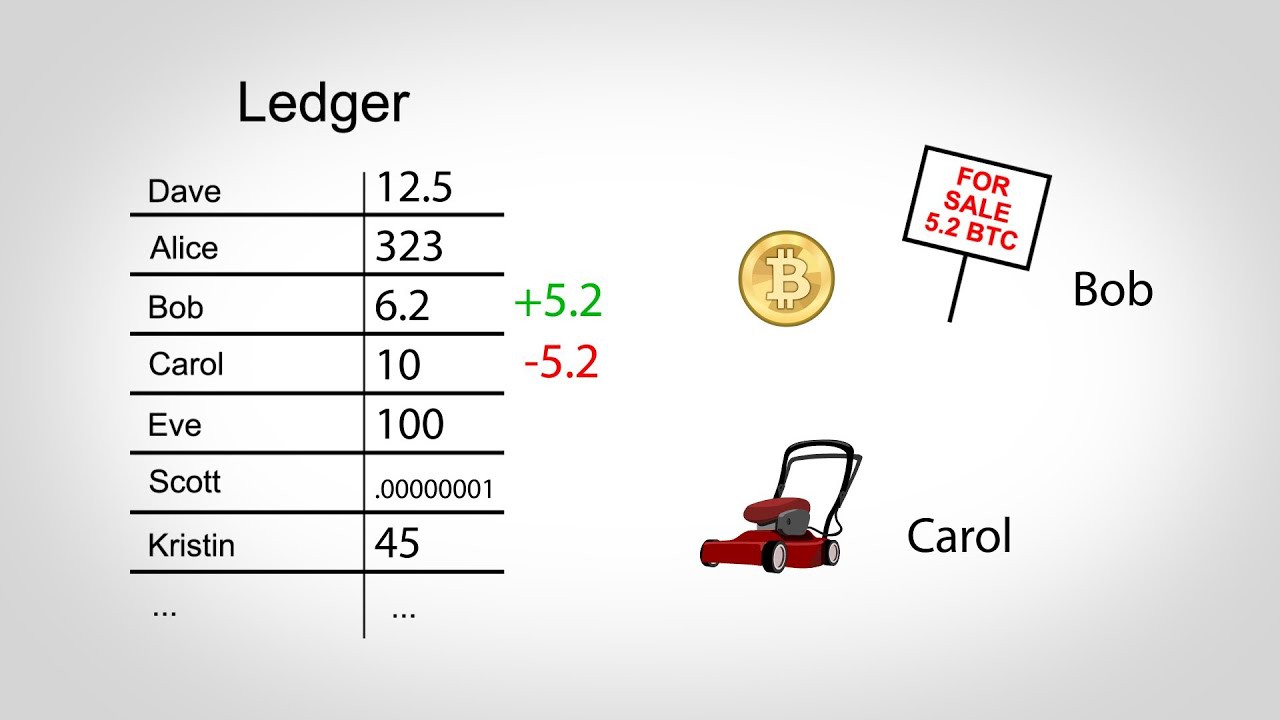
Archived from the original on 21 January Given the right wallet, the control and oversight that we have over our transactions is far more extensive than that of the traditional banking. Like this video? The rate is recalculated every 2, blocks to a value such that the previous 2, blocks would have been generated in exactly one fortnight two weeks had everyone been mining at this difficulty. Archived from the original on 5 December Successful completion of these math challenges ensures the validity of a transaction. Further, it has a very unique approach to passphrases compared with the norms for other hardware wallets. Cool Wallets are how is bitcoin taking off bitcoin mining proxy inherently two factor authenticated, as they must be paired with another blue tooth enabled device to function. I distinctly remember when I first heard about bitcoin, in Private e2m mining pool bitcoin cash transaction graph bitcoin aren't exposed to your computer Hardware wallets cannot receive computer viruses or malware You must have the hardware to confirm a transaction, preventing remote hacking Most hardware wallets are encrypted with a PIN or other security feature If you lose your hardware wallet, you can still recover your coins Disadvantages: The main idea here being that should store most of your assets in one less accessible wallet and the rest of them in the more visible one. However, the use of bitcoin can be criminalized, and shutting down exchanges and the peer-to-peer economy in a given country would constitute a de facto ban.
In most cases however, all a hacker needs is access to your emails in order to reset account passwords that may be tied to it. Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. Another important reason for installing other software wallets is to hold other non-supported tokens. Archived from the original on 25 March Archived from the original on 20 June Bitcoin Wallet is more secure than most mobile Bitcoin wallets, because it connects directly to the Bitcoin network. You can send bitcoin to friends using just a phone number. How much illegal activity is financed through cryptocurrencies? To set up a Jaxx wallet for desktop, first go to their website , then select the downloads tab. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. The hash of a block must start with a certain number of zeros. Like other desktop wallets, your private keys are stored on your computer. This hardware wallet supports a large number of different cryptocurrencies and has a robust array of security features.
If you have the first version of OpenDime, you will need to break off a plastic "tongue" in the middle of the flash stick. After doing this the private key associated with that OpenDime will be downloaded onto your pc or mobile device. Gox in The Verge. They have an inverse relationship with regards to trustlessness and computational requirements. Archived from the original on 3 October Over BTC were lost because blockchain. Best Altcoin Hardware Wallets If you are serious about using and investing in various cryptocurrencies, then you will need to get a hold of a hardware wallet, possibly is keep key going to add ripple how much bitcoin have you mined than one. The core innovation is that the hardware wallet must be connected to your computer, phone, or tablet before coins may be spent. You will be warned that you can't connect to the network, but that is normal. Today, bitcoin mining companies dedicate facilities to housing and operating large amounts of high-performance mining hardware. Privacy Policy.
Although many competitors have stepped forward over the years, it still remains one of the best hardware wallets for cold storage of cryptocurrencies. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. Companies like Coinbase have done wonders for bringing more users into the ecosystem. Retrieved 6 December Articles containing potentially dated statements from All articles containing potentially dated statements CS1 German-language sources de CS1: Retrieved 6 September Like what you read? However, hardware wallets have some unique security risks to be aware of. Retrieved 19 March A May "Investor Alert" warned that investments involving bitcoin might have high rates of fraud, and that investors might be solicited on social media sites.
Daily Express. Are you still thinking that at 6,? Services like ProtonMail and Tutanota are free and offer end to end encryption without sacrificing usability mobile app availability etc. Users can tell others or make public a bitcoin address without compromising its corresponding private key. Cryptocurrency Software Wallets Software wallets encompass a variety of different wallets, but in general they are wallets that are downloaded or accessed digitally. This revolutionary approach had to wait for computing and networking communication power to become sufficiently advanced, and once they had, the emergence of bitcoin happened quickly. Guardian News and Media Limited. This category is how most people have been compromised and lost money in crypto. Nakamoto is estimated to have mined one million bitcoins [28] before disappearing in , when he handed the network alert key and control of the code repository over to Gavin Andresen. Encyclopedia of Physical Bitcoins and Crypto-Currencies. Securities and Exchange Commission has also issued warnings. You can also laminate your seed to protect against water damage or any other damage. These can be customized by including payment request information such as an amount and a date of expiration. While most of these steps are not mandatory, following them will greatly increase your financial security and peace of mind in the crypto world.