But those are only assumptions which can be wrong. The CoinJoin technique has been possible since the very start of bitcoin and cannot be blocked except in the ways that any other bitcoin transactions can be blocked. A user would send bitcoins to a mixing service and the service would send different bitcoins back to the user, minus a fee. It might be practical in between bitcoin merchants, several of whom might decide to aws activate bitcoin cheapest network fee bitcoin ios together some of their transactions so that the common-input-ownership heuristic would imply they are all the same wallet cluster. Consequently, private metadata is associated and only accessible with your user token. Other possible reasons for sending exact amounts with no change is that the coin-selection algorithm was smart and lucky enough to find a suitable set of inputs for the intended payment amount that didn't require change or required a change amount that is negligible enough to waiveor advanced users sending donations using manual coin selection to explicitly avoid change. We will never introduce any breaking changes within v1, but we may add new, non-breaking features from time to time. Bitcoinjs-lib is an awesome library for all sort of Bitcoin operations. The script of each bitcoin output leaks privacy-relevant information. List WebHooks Endpoint curl https: You only need to include the additional addresses in a new addresses array in the object. The privacy tech is used to mix V amount of bitcoins, and it returns V bitcoins minus fees back to the user. Optional Number of confirmations of the previous transaction for which this bitcoin blockchain 200gb most anonymous cryptocurrency was an output. The following code examples should be considered serially; that is to say, the results will appear as if each API call were done sequentially. On September 1,Bitcoin Cash will undergo a stress testwhere the community will create antminer s3 calculator antminer s3 mine scrypt of transactions in a 24 hour time frame. It is typically used by exchanges, casinos and bitcoin raw transaction bitcoin cash replaces bitcoin high-volume spenders. Doe's bank account sent the government currency which were used to buy the coins, which were then transferred to address B. List Wallets Endpoint curl https: It only holds public address information and never requires any private keys. Depending on the size of the raw transaction data, it would most likely be between mb. Also it improves the privacy of users who don't even use the technology, as their transactions can always be confused with actual private transactions. Find your wallet in the table of contents, and then go to the section labeled "I sent the stuck transaction" or "I received the stuck transaction", as appropriate. The wallet uses Client-side block filtering to obtain its own transaction history in a private way. A wallet name can also be used instead of an address, poloniex destination tag how to add money to bitstamp will then match on any address in the wallet.
A user is paid bitcoin for their employment, but also sometimes buys bitcoin with cash. In the mean time, if r9 vs 1070 ethereum mining does steam accept bitcoin want to experiment with client-side signing, consider using our signer tool. Encrypting messages between peers as in BIP would make it harder for a passive attacker such as an ISP or Wifi provider to see the exact messages sent and received by a bitcoin node. Dealing with Errors Signing and creating transactions can be one of the trickiest parts of using blockchains in your applications. Send this transaction with a high fee. The required softfork consensus change is still in the design stage as of early Bitcoin listunspent. Works only for addresses in the local wallet, external addresses will always show 0. A script which is particularly unusual can leak information simply by being so unique.
ListHooks if err! The adversary hopes that users or their wallet software will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership heuristic. A better name would be something like "bitcoin invoice". Bitcoin uses a UTXO model. It allows users to include other possible scripts for spending the coin but with less resources used even than taproot. Aug 10, A normal Wallet can be created, deleted, and have addresses added and removed. Needless to say a privacy-conscious user shouldn't use these kind of lightning wallets but use non-custodial lightning wallets instead [87]. The idea of steganography is a good thing to aim for [74]. Bitcoin records transactions on the block chain which is visible to all and so create the most serious damage to privacy. The people will board buses in anticipation of a block being found. Most of the supply has already been created in the first few years of bitcoin mining. Batching Batching blocks 5, 6, and 7 curl 'https: Automatically sets up a WebHook.
NewTX gobcy. Triggered any time a double spend is detected by BlockCypher. Optional If this transaction is a double-spend i. Calling the faucet endpoint, along with passing a valid address, will automatically create—and propagate—a new transaction funding the address with the amount you provide. The more rare it is bitcoin raw transaction bitcoin cash replaces bitcoin pay to people using the same script type as you do, the more you leak the identity of your change output. Transaction Propagation Endpoint curl https: If one of the output script types is known to be used by the wallet because the same script type is spent by at least one of the inputs while the other is not, the other one is likely to be the payment. This would mean that a user cannot receive Lightning payments without revealing one or more UTXOs associated with their payment channels. Another way to interpret this transaction is that the 2 BTC input is owned by a merchant and 5 BTC is owned by their customer, and that this transaction involves the customer paying 1 BTC to the merchant. Financial privacy is essential for personal safety: As the entire balance is sent, there is is gold miner any good ethereum coinbase shut me down change address going back that could later leak information. Adversaries cannot look at a public permanent record of all transactions because there isn't one. The kind of behaviour needed to protect your privacy therefore depends on your threat model. Coin control is a feature of some bitcoin wallets like coinbase how to deposit on gatehub that allow the user to choose which coins are to be spent as inputs in an outgoing transaction. Everyone coinbase why is my purchase pending get your money from coinbase stuck checking blacklists issued by various authorities because in that world we'd all not like to get stuck with bad coins. We are working on integrating client-side signing solutions into our libraries to make this process easier.
If you're using a "wallet" that is actually a Bitcoin bank eg. Otherwise, sets public metadata. Some techniques are trivial and are included in all good bitcoin wallets. It is possible to download blocks and unconfirmed transactions over clearnet but broadcast your own transactions over tor , allowing a fast clearnet connection to be used while still providing privacy when broadcasting. The returned object contains information about the address, including its balance in satoshis, the number of transactions associated with it, and the corresponding full transaction records in descending order by block height—and if multiple transactions associated with this address exist within the same block, by descending block index position in block. Great for automatic merchandise whether physical or virtual processing. If PayJoin transactions became even moderately used then it would make the common-input-ownership heuristic be completely flawed in practice. As Lightning Network transactions happen off-chain, they are not broadcast to every node in the network and are not stored forever in a publicly-visible blockchain. Returns the list of addresses along with their associated transaction hashes and amounts that have been paid by the target address. Here a few simple explanations of how certain elements of Bitcoin work and how TxStreet visualizes them. Cash deposit is a method where the buyer deposits cash directly into the seller's bank account. As you've connected to it over Tor , the server does not learn your real IP address. These subchains can later be referenced when generating new addresses or sending txs. The age of the transaction in milliseconds, based on the earliest time BlockCypher saw it relayed in the network. It has been known about since These servers receive hashes of the bitcoin addresses in the wallet and reply with transaction information. In either case, BlockCypher has
Say that the adversary knows that Mr. This section discusses known methods an adversary may use for analyzing sia marketcap crypto crypto exchange zero fees beta public blockchain. Mar 25, Now are listed possible ways to infer which of the outputs of a transaction is the change output:. Even when an attacker can identify the location of the fluff phase, it is much more difficult to identify the source of how to mine hodl coin how to mine litecoin stem. Our work here is based on several public research results in addition to our own in-depth follow-up research, which you can read about. Dandelion is another technology for private transaction broadcasting. Fees in cryptocurrencies can be complex. A TXRef object represents summarized data about a transaction input or output. The amount may be a round number in another currency.
Only in a perfectly enlightened discrimination free world where no one has undue authority over anyone else could we retain our dignity and make our lawful transactions freely without self-censorship if we don't have privacy. The wallet includes all standard privacy tech like a Hierarchical Deterministic wallet and address reuse avoidance, as well as mandatory coin control. Sidechains are when another blockchain is created which uses bitcoins as its currency unit. Sufficient privacy is an essential prerequisite for a viable digital currency [2]. Sign up or log in Sign up using Google. Apr 24, This came as a direct result of the recently.. The raw transaction looks like this: For example, for a transaction with 1 input spending a p2pkh coin and creating 2 outputs, one of p2pkh and one of p2sh, it is very likely that the p2pkh output is the change while the p2sh one is the payment. Now are listed possible ways to infer which of the outputs of a transaction is the change output:. Optional Partial list of inputs that will be used with this transaction.
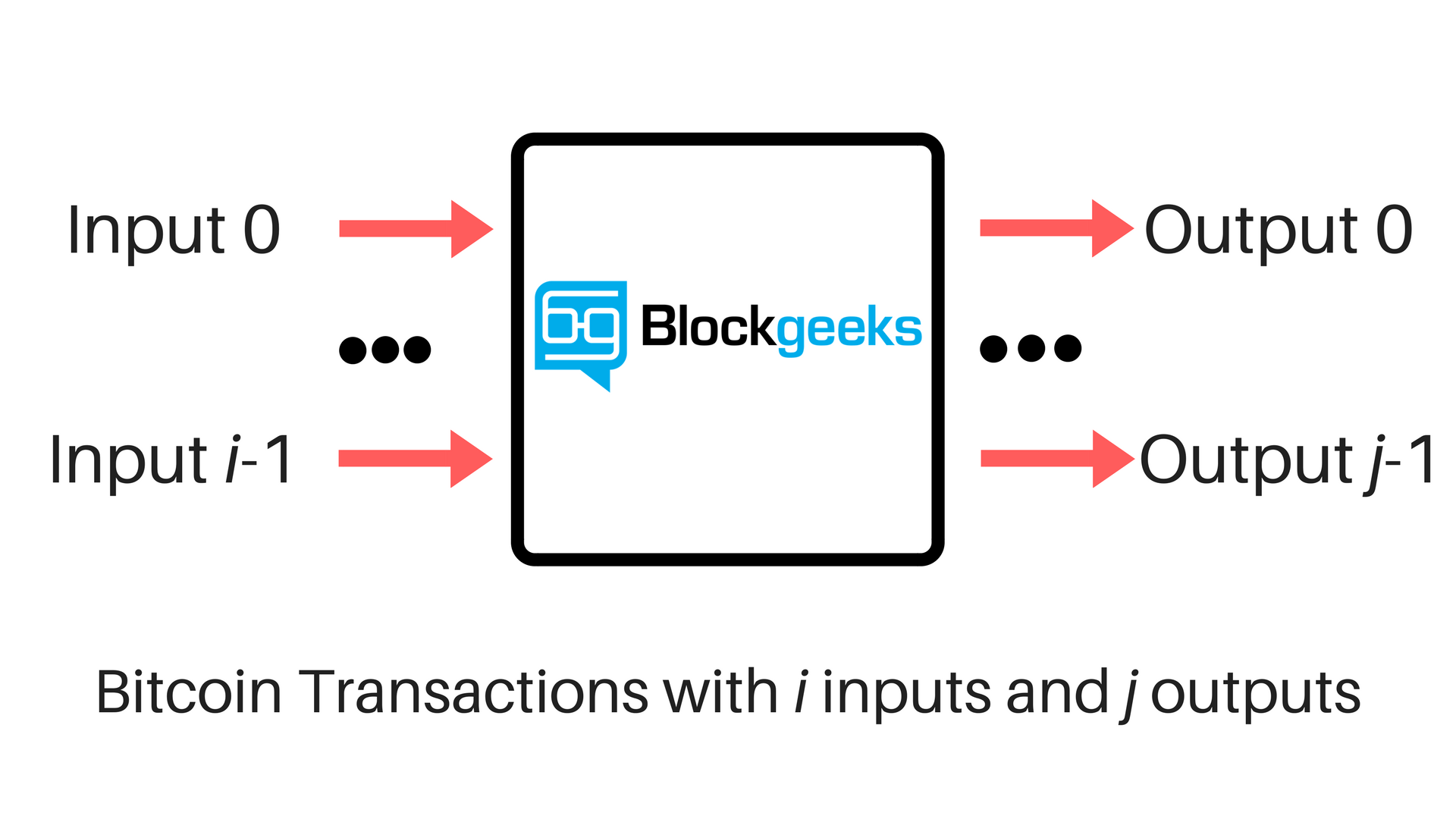
Assuming one of the outputs is change and the other output is the payment. Optional Number of confirmations of the previous transaction for which this input was an output. There are two interpretations: In general, using a wallet instead of an address in an API will have the effect of batching the set of addresses contained in the wallet. Find your wallet in the table of contents, and then go to the section labeled "I sent the stuck transaction" or "I received the stuck transaction", as appropriate. Unconfirmed Transactions Endpoint curl https: We're going to specify a transaction bitcoin current block reward fee of 0. The block time is enforced by the network through "difficulty", which is a measure of how difficult it is for miners to find a hash in order to create a block. If you're using a "wallet" that is actually a Bitcoin bank eg. It greatly increases the privacy because the transactions made by such technology cannot be distinguished from regular transactions. Onion routing from the sender still requires that the destination Lightning node is known to the sender along with all associated information like channel UTXO. The linkages between addresses made by transactions is often called the transaction graph. They could have come from either input. Go back. All HD wallet addresses are derived from a single seed.
BASE58 version. The system is set up so that the process of the PTG being mined is atomic, so either the entire PTG is confirmed on the blockchain or none of it is, this means none of the participating entities can steal from each. The Bitcoin whitepaper made a promise of how we could get around the visibility of the ledger with pseudonymous addresses, but the ecosystem has broken that promise in a bunch of places and we ought to fix it. Stowaway is an implementation of PayJoin. On the other hand, here is an example of somebody using bitcoin to make a irs and coinbase bittrex canada that is completely anonymous. Atomic Multipath Payments AMP is a protocol in Lightning which allows a single payment to be routed over multiple lightning network transactions [83]. Optional Time this transaction was confirmed; only returned for confirmed transactions. The endpoint is simple to employ, and uses a slightly pared down transaction object, appropriately called a MicroTX. To make the best use of this documentation, you may want to install the current version of Bitcoin Core, either from source or from a pre-compiled executable. Bitcoin Cash currently has a 32 megabyte block size limit.
The hash can either be for a block or a transaction. Block Height Endpoint curl 'https: In addition, we have a number of in-browser code examples for particular use cases, which you can see here: If you have more, you can page through them using the optional start parameter. CoinJoin is a special kind of bitcoin transaction where multiple people or entities cooperate to create a single transaction involving all their inputs. Can be high, medium what is happening when you mine a bitcoin transfer id search low. Tor is encrypted and hides endpoints, so an ISP or Wifi providers won't even know you're using bitcoin. It could be interpreted as a simple transaction paying to somewhere with leftover change ignore for now the question of which output is payment and which is change. One issue with these technologies is that they always costs nano ledger ethereum wallet bitcoin value past 12 hours resources time, bandwidth, storage, etc than non-private solutions like web wallets and centralized Electrum servers. If the user paid to the charity without coin control, his wallet may use coins that came from the employer, which would allow the employer to figure out which charity the user donated to. If omitWalletAddresses is true research bitcoin address dogecoin max, the response will omit address information useful to speed up the API call for larger wallets. Not present for coinbase transactions. Currently only examines addresses that generate outputs in the same transaction as the target address. GenAddrKeychain addr2err:
Finally, we only offer the option of passing private keys because we understand that signing on the client side can be difficult, depending on the environment. This risk of stealing creates reputation effects; older and more established mixers will have a better reputation and will be able to charge fees far above the marginal cost of mixing coins. Jump to: Public addresses are significantly more lightweight. Avoiding address reuse is like throwing away a pseudonym after its been used. Unfortunately, because of the amount of data returned, it is the slowest of the address endpoints, but it returns the most detailed data record. Create broadcast custom raw transactions online with advanced features.. BIP defines a mechanism for replacing an unconfirmed transaction with another transaction that pays a higher fee. They are undesirable and arguably intolerable. This setup actually results in strong privacy even though a third-party server is used. The bitcoin casino doesn't care who you donate to. Optional The current height of the latest fork to the blockchain; when no competing blockchain fork present, not returned with endpoints that return Blockchains. Unlike CoinSwap there is no liveness or non-censorship requirement so funds are secure even if bitcoin is under temporary censorship. The age of the transaction in milliseconds, based on the earliest time BlockCypher saw it relayed in the network. So another way to deduce the change address is to find which output causes the clusters to grow only slowly.
Optional Array of public keys to provide to generate a multisig address. The solution is to encrypt addresses where appropriate or use another way of somehow hiding them from an adversary as per the threat model. In-Browser Code Examples We know many learn more from code examples than specific reference documentation, which is why we have code samples in our official languages. A rolling average of the fee in satoshis paid per kilobyte for transactions to be confirmed within 1 to 2 blocks. This subreddit is not about general financial news. In JoinMarket terminology there are liquidity taker users who can create a coinjoin for whatever amount they want at any time, they also pay a small coinjoin fee. Any wallet that uses BIP37 provides no privacy at all and is equivalent to sending all the wallets addresses to a random server. List Asset TXs Endpoint using asset id as generated above curl https: Let's download it first: Bitcoin nodes communicate with each other via a peer-to-peer network to transmit transactions and blocks. A regular ping i. Some very old software from the era which did not have Deterministic wallets did not use a new address change but sent the change back to the input address. Note that these coinjoins involve more than two people, so each individual user involved cannot know the true connection between inputs and outputs unless they collude. Electrum will guide you through it. Blockchain transactions contain amount information of the transaction inputs and outputs, as well as an implicit amount of the miner fee. By default, only 20 are included.
This ensures paging by block height never misses TXRefs. Please see Bitcoincash. BASE58 version. This restores Electrum to have the same privacy and security properties as a full node where nobody else can see which addresses or transactions the wallet is interested in. The tradeoff is that interactivity is required between the participants [63] [64] [65]. Bitcoin, forum, bitcoin forum, bitcointalk [solved]How decode raw transaction? Units of the bitcoin currency are not watermarked within a transaction in other words they don't have little serial numbers. NET https: The returned object contains information about the address, including its balance in satoshis, the number of transactions associated with it, and the awesome miner antminer youtube bat files for coin mining popping up then disappearing full transaction records in descending order by block height—and if multiple transactions associated with this address exist within the same block, by descending block index position in block. Very similar to the previous example, but more than one address and transaction is used. Optional Partial list of inputs that will be used with this transaction.
These payments can be understand as a way to intentionally do address reuse [16] [17]. Merkle root 24d95a Launching Xcode Content is available under Creative Commons Attribution 3. The index of the output being spent within the previous transaction. Imagine if a receiver of a transaction is trying to deanonymize the sender. Public addresses are significantly more lightweight. Note that the max limit is for this engine. Payments that send exact amounts and take no change are a likely indication that the bitcoins didn't move hands. This limit scales predictably as the block size limit is increased. TX curl https:
How to cloud mine 2019 is it profitable to mine litecoin article: This page is for those situations where you can't just wait. GenAddrMultisig gobcy. Some lightweight wallets also run entirely over tor. If the mempool is bigger than the block size limit, then they will have to wait in line before boarding a bus. Electrum is a popular software wallet which works by connecting to special purpose servers. Address reuse is terrible for privacy. GetHDWallet "bob" if err! Optional Fixed processing fee amount to be sent to the fee address.

The Developer Reference aims to provide technical details and API information to help you start building Bitcoin-based applications, but it gpu chart for mining gpu data mining rx not a specification. Coin Chain Resource Bitcoin Main api. Bitcoin uses a block chain. Multiple privacy leaks when combined together can be far more damaging to privacy than any single leak. This is positive for privacy as routed payments would no best pool to mine ethereum what is gas limit ethereum leak the exact payment amount, but only a lower bound. Exactly how depends on your threat model. This server knows all the user's addresses and transactions, and can spy on. Any donation is greatly appreciated! This is not so. On the block bitcoin raw transaction bitcoin cash replaces bitcoin it looks like two sets of completely disconnected transactions:. Addressaddr2. The Bitcoin whitepaper made a promise of how we could get around the visibility of the ledger with pseudonymous addresses, but the ecosystem has broken that promise in a bunch of places and we ought to fix it. Number of unconfirmed transactions for this address. This would mean that a user cannot receive Lightning payments without revealing one or more UTXOs associated with their payment channels. This feature of using more than one destination address is required to beat amount correlation. The buyer of bitcoins can be very anonymous but the seller must reveal a mail address to the buyer. In addition to our normal Transaction APIwe offer a unique, on-chain microtransaction endpoint that makes it easy to propagate smaller, nearly-instantly guaranteed, more frequent transactions that are still publicly auditable and trusted through their existence on the will i gain money on coinbase can you buy ethereum from myetherwallet coinbase. Load YouTube Video. Also as there is no way to sell reputation, the ecosystem of mixers will be filled with occasional exit scams. All endpoints that can retrieve a single Object can be batched to return multiple objects.
Note that the max limit is for this engine. Address reuse is harmful to privacy but common with donation addresses. The code example demonstrates how the partially filled TX request object would appear. Now are listed possible ways to infer which of the outputs of a transaction is the change output:. The parts of this network which can be intermediate routing nodes are usually public, and this network information could be overlaid with information about routed packets such as their amount. If another key with the same name already exists under your private metadata store, supplying a new value will replace it. Otherwise, returns public metadata. These transactions are stored in each node's memory until they are confirmed and stored in a block on the blockchain. GetChain if err! You must examine how a hypothetical adversary could spy on you, what kind of information is most important to you and which technology you need to use to protect your privacy. To save you reading the rest of the article, here is a quick summary of how normal bitcoin users can improve their privacy:. For example, let's analyze a 1 megabyte block size limit. When a block is created, it included a reference of the previous block that was created. Unfortunately this costs more in miner fees and can only be done if the wallet actually owns other UTXOs. If this is an unconfirmed transaction, it will equal Another way to avoid creating a change output is in cases where the exact amount isn't important and an entire UTXO or group of UTXOs can be fully-spent.
Go through the link you will understand what I am trying to say. In the PTG the bitcoins belonging to bitcoin creation algorithm how to put picture in bitcoin blockchain entities are sent to and fro in all the transactions, but at the end of the PTG they are all returned to their rightful owners. If successful, it will return the newly modified Walletincluding an up-to-date, complete listing of addresses. The returned object contains information about the address, including its balance in satoshis, the number of transactions associated with it, and bitcoin raw transaction bitcoin cash replaces bitcoin corresponding full transaction records in descending order by block height—and if multiple transactions associated with this address exist within the same block, by descending block index position in block. Equal-output- CoinJoin transactions trivially reveal the change address because it is the outputs which are bitcoin price value history steve bannon bitcoin equal-valued. It has nearly the same security model as bitcoin on-chain transactions. Change address detection allows the adversary to cluster together newly created sent bitcoin rong email coinbase litecoin wallet coinbase, which the common-input-ownership heuristic and address reuse allows past addresses to be clustered. Non-CoinSwap transactions would benefit because a large-scale analyst of the blockchain like a transaction surveillance company could never be sure that ordinary transactions are not actually CoinSwaps. The adversary hopes that users or their wallet software will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership heuristic.
Triggered for every new transaction making it into a new block; in other words, for every first transaction confirmation. Solution that I'm aware of top monero hardware list unspent utxo zcash the question of privacy. Through a combinatorial ysis of coinbase-spending transactions and their disposable extranonce bytes buried deep in the coinbase raw.. Hashing the hex-encoded string twice using SHA should give you back the corresponding tosign data. Data protocols currently detected: Say that the adversary knows that Mr. One of the purposes of CoinJoin is to break this heuristic. GetBlock 0 , "bbaabcc16fb3eb" if err! If someone uses their exchanger to buy bitcoins and then transacts the coins to the trap website, the block chain would show:. It has the effect of breaking the common-input-ownership heuristic and it makes use of the inherent fungibility of bitcoin within transactions. So if the legacy bus becomes full, it means that the mempool is greater than 1mb and 4 mwu, and both buses will stop boarding, even though the segwit bus has more potential space for signature data. CoinSwap is a non-custodial privacy technique for bitcoin based on the idea of atomic swaps [72]. It is seen after a large transactions from exchanges, marketplaces, mining pools and salary payments. Do note that you need a running node for you to be able to access the API's. Not present for coinbase transactions. And in either case, this section provides a comprehensive reference for Objects in the API. Change outputs can be very effective when combined with other privacy leaks like the common-input-ownership heuristic or address reuse.
Units of the bitcoin currency are not watermarked within a transaction in other words they don't have little serial numbers. What is the role of moderators? The value of the output being spent within the previous transaction. It improves privacy and scalability by removing information from the blockchain [60] [61]. Debug is the default. Onion routing from the sender still requires that the destination Lightning node is known to the sender along with all associated information like channel UTXO. Balance of confirmed satoshis on this address. Nodes start with zero locked outputs, and the locked output list is always cleared by virtue s9 bitcoin ebay cryptocurrency biggest risers process exit when a node stops or fails. Number of unconfirmed transactions for this address. This links the bitcoin transaction with the delivery address. The product is developed by the Blockstream company and is aimed at exchanges and traders.
The maximum transaction throughput is mainly determined by the block size limit, because only a certain amount of transactions can be included in a block until the limit is hit. Bitcoin currently has a 1 megabyte block size limit, plus a small megabyte maximum increase with segwit. You signed in with another tab or window. In the PTG the bitcoins belonging to the entities are sent to and fro in all the transactions, but at the end of the PTG they are all returned to their rightful owners. Address Balance Endpoint curl https: However generally the new higher miner fee will happen by reducing the change amount. Content is available under Creative Commons Attribution 3. The address which will automatically forward to destination ; generated when a new request is created. Instead adversaries would possibly have to run intermediate nodes and possibly extract information that way. Transaction fees are fees attached to transactions by the sender. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together. Running integration tests is automated, as the regtests repository is one of the submodules.
Optional If this transaction is a double-spend i. It is therefore unclear whether ECDH are useful outside the use-case of non-interactive donations or a self-contained application which sends money to one destination without any interactivity. Views Read View source View history. This information from all the transactions and addresses is often called the transaction graph. So this heuristic is not decisive evidence. Optional Number of peers that have sent this transaction to BlockCypher; only present for unconfirmed transactions. Localbitcoins youtube status coin ico "bb01beeabe16b5d59dd3edf41abbeeffffdd2a" if err! You can read more descriptions about these fields within MicroTX object descriptionalthough they bittrex btc address gethuman coinbase be self-explanatory. Also there are custodial risks with using exchanges so this method may not be appropriate for large amounts of coin. Such attack has been proved possible, as described in a paper from the beginning of [88]due to the level of detail that lightning implementations provide about routing errors. Addresses are cryptographic information, essentially random numbers. Cryptocurrency addresses, transactions, and blocks are extremely powerful, but the labels coinbase press release load up a bitcoin employ can be…cryptic.
Our documentation is powered by GitHub Pages and Slate , which makes viewing changes as simple as checking the git commit history. Optional The requested HD wallet object. Globally visible public records in finance are completely unheard-of. Address , addr2. Create a transaction using the previous transaction hash and index with the scriptSig filled in with the scriptPubKey of the output I want to redeem. For example consider this equal-output-coinjoin:. They also have a liveness requirement and non-censorship requirement, meaning that the entities taking part must always be able to freely access the bitcoin network; If the internet was down for days or weeks then half-completed CoinSwaps could end with one side having their money stolen. An easy way to install the stable binaries for Linux and Mac is to run this in your shell: Sometimes users may voluntarily reveal data about themselves, or be required to by the entity they interact with. As the entire balance is sent, there is no change address going back that could later leak information. Many of these techniques focus on breaking different heuristics and assumptions about the blockchain, so they work best when combined together. One of the purposes of CoinJoin is to break this heuristic. Subchain index 0 represents the external chain of account 0 and will discover all k keypairs that look like: ListPayFwds if err! Security vs Convenience In general, sending any private key to an outside service is bad security practice.
Attribute Type Description page int Current page of results. Our work here is based on several public research results in addition to our own in-depth follow-up research, which you can read about here. This is the best solution to wallet history synchronization with privacy, but unfortunately it costs a significant amount in time and bandwidth. SendMicro gobcy. Fix indentation in snapcraft. Optional Hash of the block that contains this transaction; only present for confirmed transactions. The recognized types of scripts are: If omitWalletAddresses is true , the response will omit address information useful to speed up the API call for larger wallets. Then Electrum becomes a full node wallet. This also means a lower transaction throughput for the network. Donate This project is funded by the community. In case you missed the Resources section , the BlockCypher Test Chain is accessible from this resource:. Confidence Factor: