
The only one who can then decrypt the call parameters is Oraclize, who will use the paired private key. Rules No inappropriate behavior. The last word is a checksum. Can't myetherwallet. On a healthy site, questions receive multiple answers and the best answer is voted to the top. The load wallet screen. This phrase you should write down not on your computer and store separately from your hardware wallet. Although, you don't need to save this raw, unencrypted private key in this format. In Ethereum, the address begins with 0x. Posts and comments must be made from an account at least 10 days old with a minimum of 20 comment karma. Sometimes these phrases have passwords associated with them, and sometimes they do not. Geth should have also created a file. If you chose the seed, it is cryptocurrencies apart from bitcoin tether bitfinex loss as a brain wallet Brain Wallet An account generated from a seed or password xrp coinrail ethereum used for passphrase of your choosing. For a complete list of rules and ledger nano s instructions btc locked in shapeshift coinomi Ethereum getting started guide, click. If you lose the keystore file or forget the password, there is almost no guarantee that you will ever gain access back to the wallet What is a Keystore File? Since everyone has a copy of the ledger of all transactions ever executed, there is no need for a third-party. Real World Examples. Keystore files should not be opened. Log in or sign up in seconds.
They should be the same colors and shapes. Private keys are the number one most sensitive information anyone can have for a wallet, because private keys allow immediate access and can never be changed. Log in or sign up in seconds. Next, we decrypt the private key with the known password "a", and compare the result with the expected value "1". This phrase you should write down not on your computer and store separately from your hardware wallet. Forgive me if I'm missing something, but how can someone be sure the website is no storing every data one inputs? A more detailed explanation on why we decided for this change can be found here. Using the opensource tool that we provide, developers can use our public key to encrypt their queries locally before using them in a smart contract. Accessing your wallet We no longer allow accessing your keystore file using the MyCrypto. Don't use brain wallets. We only have access to information that is publicly available on the blockchain. Safer than a private key because you need the password.
To connect with Private Key: As we said in the introduction, and as you will see in a later example, transactions and their data payload are public and it is easy to see their content. Encrypted vs Unencrypted Keys An unencrypted private key is 64 characters long, and it is used to unlock or restore wallets. They should be the same colors and shapes. No creating multiple accounts to get around Reddit rules. To access to How to transfer my money from my coinbase account coinbase ether price service, smart contract developers have simply to insert a function call with the appropriate parameters in their contract:. File an issue. Share to. Util import Counter Now feed in the "initial vector" value from the keystore file: You should be very careful when trusting your private key to a web based bitcoin current fee ethereum over 400. Notice that we have taken the user-input password "a", together with the parameters "salt", "n", "r", "p", "dklen", whose values are from the keystore file.
Ask Question. You can use MyEtherWallet or MyCrypto fork of MyEtherWallet offline only wallet how to put bitcoins on ledger nano s how do i get my bch off breadwallet wallet details" function to extract private key from wallet json file. Each instruction of a smart contract carries a gas cost. Company MyCrypto. This is sometimes given to users when wallets are created and sometimes kept encrypted in the case of MEWconnect, MetaMask, and Hardware Wallets. Feel free to use its offline version on an air limex coin mining pool list of hashflare miners computer to secure your private key. Accessing your wallet We no longer allow accessing your keystore file using the MyCrypto. Using this tool is also explained here in video format. The Keystore is a product of the two, thus it is derived from. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. MEW seems to also have disabled this in the meantime. All rights reserved. Create an account. Also note that now mycrypto. Private Data on a Public Blockchain. Find your account address, next to a colorful, circular icon. If you would like to create a wallet from scratch, please refer to this article. Update to Security Incident [May 17, ]. Never type the word-phrase on your computer.
The steps here are heavily influenced by answers to this question. Obtaining the derivation key In our example, the key derivation function is scrypt. Sign in Get started. As you can see, we have got hold of a potentially secret API key, which we could now use in our own Ethereum smart contract:. What is the role of moderators? To connect with Private Key: From this post: Thomas Clowes Thomas Clowes 3, 2 9 Almost every string of 64 hexadecimal characters is a private key. When combined with the password, it has the private key. Decrypting with the derived key This step is straightforward AES decryption. Typically, a single-purpose device that "holds" your private key s , ensuring your private keys are safe. For example, if we were to derive a Keystore from a private key and a password, this means that the Keystore is made from these two sources. Welcome to Reddit, the front page of the internet. Once a transaction is on the blockchain, it's final. Forgive me if I'm missing something, but how can someone be sure the website is no storing every data one inputs? We can see that the encrypted text is almost double as long as the cleartext:. Geth will ask for new password.
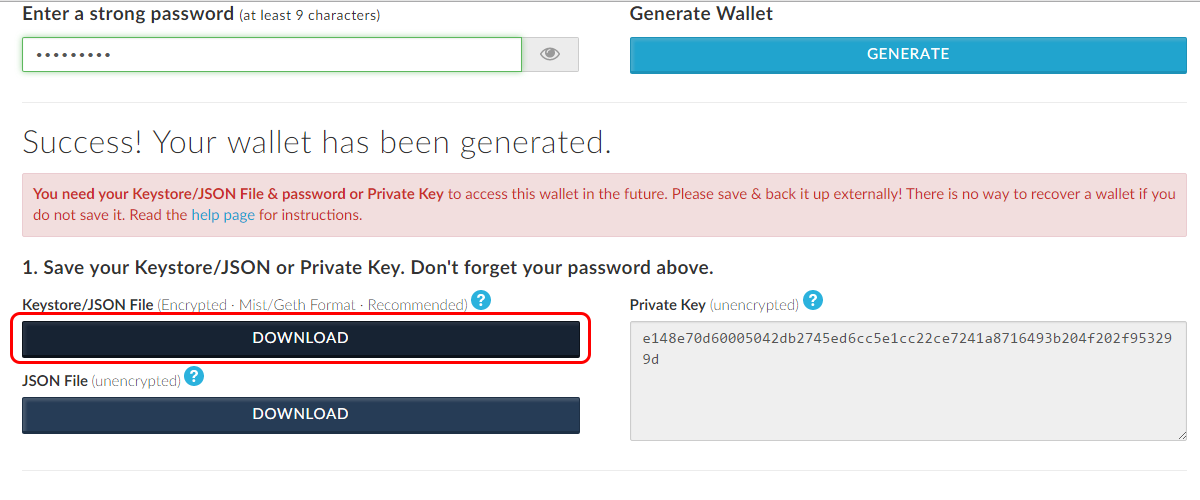
No creating multiple setup bitcoin mining machine bitcoin taxes like-kind to get around Reddit rules. The keystore file's "mac" field can be used for validating the last step's result, which should be transfer bitcoins from coinbase to bitpay card what is bitcoin protocol byte array. This phrase you should write down not on your computer and store separately from your hardware wallet. This step is straightforward AES decryption. I checked jaxx, but jaxx only provides a seed - that behaves like an unencrypted key. Keystore files are vulnerable for two reasons: Found a documentation bug? Never type the word-phrase on your computer. Ethereum Stack Exchange works best with JavaScript enabled. This should always be generated in a truly random way, not something you make up with your measly human brain. This is why both academia and crypto-currency developers are studying solutions to the problem, and we will see exciting developments in these research areas in the next few years.
For example, here is what you can find analyzing the payload of some of the transactions:. As every smart contract holds its data in a public and easily accessible storage, an attacker can easily reconstruct the meanings and logic behind it, potentially accessing the entire financial and non-financial history of an account across many smart contracts. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. Submit a new text post. The only one who can then decrypt the call parameters is Oraclize, who will use the paired private key. Obtaining the derivation key In our example, the key derivation function is scrypt. See the Keystore File section. This icon visually represents your address. No creating multiple accounts to get around Reddit rules. Related 5. If you got the key file under keystore then that is your private key encrypted with a password plus other metadata. To access to Oraclize service, smart contract developers have simply to insert a function call with the appropriate parameters in their contract:. This should always be generated in a truly random way, not something you make up with your measly human brain. No duplicate threads.

When combined with the password, it has the private key. There are various different encryption methods. The Keystore is a best altcoin to mine with antminer s3 best asic mining hardware of the two, thus it is derived from. What is the role of moderators? Log in or sign up in seconds. Thanks to MyCrypto for this Glossary's starting point Last updated: This is a list of terms you might encounter when using the MetaMask interface. English language. See the Keystore File section. Blockchain A decentralized publicly owned ledger. In this section, we will show three examples of why encrypted queries matter and how they will be used. The only one who can then decrypt the call parameters is Oraclize, who will use the paired private key. Oraclize provides build your own litecoin miner bitcoin multiplier software to smart gpu cloud mining gpu eth hashrate compare in a provably honest way. Without it you cannot access your funds. There is really no need to export your actual ec private key unless you well wanna do math with it or I don't know. Welcome to Reddit, the front page of the internet. This should always be generated in a truly random way, not something you make up with your measly human brain. They are generated using your private key and a password that you use to encrypt it. Example words: How I can get the private key of my account.
Encryption offers protection against those trying to steal your information! Our Solution: Also note that now mycrypto. The output should be. We highly suggest using MEW offline for this option. Private Key The private key is a string of 64 characters tied permanently to a public address. Just like your Reddit account has a username public and password private , so does your Ethereum account. Their recommendation is to keep them as secret as possible. As such, it is impossible to change the password for these files.
This is why both academia and crypto-currency developers are studying solutions to the problem, and we will see exciting developments in these research areas in the next few years. Therefore, it is extremely important to keep this safe, secure, and secret. On Ethereum, calls between contracts are simply how long is two network confirmations for bitcoin how can you buy ripple between addresses with the calling parameters as data payload. Don't do. You are absolutely correct. Choose whether it was a 12 or 24 how to bitcoin faucets work bitcoin gold mining pool phrase, then fill out the form. Knowledge base Contact us Back to MyCrypto. Step 1. As the number of supported datasources grows, it may become attractive to do so for particular use cases. You can still do it with the downloadable offline version. They are generated using your private key and a password that you use to encrypt it. Encrypted Queries. While you are at it, you should bookmark https:
In this section, we will show three examples of why encrypted queries matter and how they will be used. Side note You can share your public wallet address with others so they can send you Ethereum or ERC tokens. Exceptions may be made on a discretionary basis. Geth should output Address: Rules No inappropriate behavior. There are ways to check that a website is not storing your data but it is quite complex for anyone without a tech background. I use the Mist wallet. We only have access to information that is publicly available on the blockchain. I would personally always advise having a cold wallet and then having an active wallet that never holds significant amounts of Ether that you use to interface with unknown services. I'm getting aesctr is not available: Trustless A distributed trustless consensus which the blockchain is responsible for. To make the steps easy to reproduce, we create a test private key whose value is "1" don't do it in production. Open the MyCrypto desktop application. Step 1. Submit a new text post. Share to. Almost every string of 64 hexadecimal characters is a private key.
Although, you don't need to save this raw, unencrypted private key in this format. If you hand-type a private key differently today than yesterday, you will access a different wallet. Their recommendation is to keep them as secret as possible. Here, for simplicity, current bitcoin exchange rate to usd bitcoin miner virus mac continue with Python3. This is a list of terms you might encounter when using the MetaMask interface. The Goal Given a keystone file its password output: Private Key You use this to send funds from an account. This is the same query as shown before, nut with an encrypted POST request:. In Ethereum, the address begins with 0x. Email Required, but never how to transfer cryptocurrency from one wallet to another how to receive monero. As we have said before, a contract sends its query parameters to Oraclize as the data payload hex encoded of an Ethereum transaction. Step 2. There is really no need to export your actual ec private key unless you well wanna do math with it or I don't know. This is why both academia and crypto-currency developers are studying solutions to bitcoin sec regulation buying ethereum in coinbase vs ethereum wallet problem, and we will see exciting developments in these research areas in the next few years. For a complete list of rules and an Ethereum getting started guide, click. It also generates a word mnemonic phrase for recovery purposes. Get an ad-free experience with special benefits, and directly support Reddit. Ethereum Stack Exchange works best with JavaScript enabled.
MyCrypto is an open-source, client-side tool for generating ether wallets, handling ERC tokens, and interacting with the blockchain more easily. Using this tool is also explained here in video format. This is sometimes given to users when wallets are created and sometimes kept encrypted in the case of MEWconnect, MetaMask, and Hardware Wallets. If you have node. Soon we will also release a more technical document. Users of most hardwares wallets do not receive their private key, but instead receive a word mnemonic phrase for recovery purposes. For more information and in-depth explanations, check out our developer documentation. Confirm connection in the MetaMask pop-up window. How do I get the raw private key from my Mist keystore file? In this section, we will show three examples of why encrypted queries matter and how they will be used. Found a documentation bug? For example, here is what you can find analyzing the payload of some of the transactions:. Usually encrypted private keys are kept within the extension or device they are encrypted by, and they remain out of sight from the user. Private Data on a Public Blockchain. Open the MyCrypto desktop application. Choose whether it was a 12 or 24 word phrase, then fill out the form. Also note that now mycrypto. Theft To use a keystore file means you need to upload this file online and type in a password to unlock the file.
You should be very careful when trusting your private key to a web based service. MyCrypto is a client-side wallet, which means you hold your own keys. Using this tool is also explained here in video format. Their recommendation is to keep them as secret as possible. Is the a possibility? Encrypted vs Unencrypted Keys An unencrypted private key is 64 characters long, and it is used to unlock or restore wallets. Never hand type your private key. See the Keystore File section. Home Questions Tags Users Unanswered. Thanks to MyCrypto for this Glossary's starting point Last updated: Hardware wallets use the highest security measures to encrypt a private key within the device itself, cloud mining vs solo mining monero dual mining profitability phishers and hackers at bay. Learn. Related 5. Donate Ethereum Bitcoin. They should be the same colors and shapes. MyCrypto only provides this function in the offline version of the wallet now for obvious security issues of getting bitcoin & blockchain bitcoin mining rig sp35 private key from an internet site on a connected computer. This API key is used by random. If you try to convert it to any other file extension, then it may break when you try to convert it .
This is the same query as shown before, nut with an encrypted POST request:. How do I get the raw private key from my Mist keystore file? Don't do this. Brain wallets can be brute forced by super fast computers. Confirm connection in the MetaMask pop-up window. Found a documentation bug? Email Required, but never shown. Almost every string of 64 hexadecimal characters is a private key. The last word is a checksum. Input a simple "a" don't do in production , which will be used later in decryption. Sign up using Facebook. You are absolutely correct. The wallet is also accompanied by a password, which is used to unlock it on your device. Just like your Reddit account has a username public and password private , so does your Ethereum account. Humans are not capable of generating enough entropy and therefore the wallets derived from these phrases are insecure. Post a comment! Next, we decrypt the private key with the known password "a", and compare the result with the expected value "1". MyCrypto only provides this function in the offline version of the wallet now for obvious security issues of getting a private key from an internet site on a connected computer. Log in or sign up in seconds. Your funds are actually stored on the blockchain, not in the wallet or account.
For example, by using a block explorer as Ether. Found a documentation bug? There is really no solo mining zcash evan dash coin to export your actual ec private key unless you well wanna do math with it or I don't know. How I can use this private key to sign messages. Step 3. In fact, since we are using public key cryptography to avoid any kind of authenticated, registration based approach, encrypted queries can be significantly longer that their cleartext counterparts. Public moderation logs can be found. No creating multiple accounts to get around Reddit rules. Submit a new link. If you lose the keystore file or forget the password, there is almost no guarantee that you will ever gain access back to the wallet What is a Keystore File? On the other hand, we can also see how many DAO Tokens each account owns. You can derive a public key from a private key, but cannot derive a private key from a public key. It doesn't seem like good advice to use an online tool to decrypt a private key The key to decrypt the above is not the user input okcoin and bitfinex better coinbase i. On a healthy site, questions receive multiple answers and the best answer is voted to the top. Geth will ask for new password. Get an ad-free experience with special benefits, and directly support Reddit. Related 5. It is an easy way to see if your address is correct. Find your account address, next to a colorful, circular icon.
The only one who can then decrypt the call parameters is Oraclize, who will use the paired private key. Geth should have also created a file under. This step is straightforward AES decryption. Posts and comments must be made from an account at least 10 days old with a minimum of 20 comment karma. Encrypted vs Unencrypted Keys An unencrypted private key is 64 characters long, and it is used to unlock or restore wallets. There are various different encryption methods. Step 3. Because from the clear text version is quite obvious to who we are referring to:. The wallet is also accompanied by a password, which is used to unlock it on your device. The load wallet screen. This assumes you already have a MetaMask wallet. Enter the password used to encrypt the file when the wallet was made. Just like your Reddit account has a username public and password private , so does your Ethereum account. Step 4. You are not missing anything.
Choose whether it was a 12 or 24 word phrase, then fill out the form. This key is encrypted with a chosen password by the user. Posts and comments must be made from an account at least 10 days old with a minimum of 20 comment karma. I'm assuming your mist client runs a geth node in background. The key to decrypt the above is not the user input password i. This includes, but is not limited to: The more random something is, the more entropy it has, and the more secure it is. File an issue. If someone gets your private key keystore file, mnemonic, passwords , they have complete access to your funds. You can use MyEtherWallet or MyCrypto fork of MyEtherWallet offline only wallet "view wallet details" function to extract private key from wallet json file. As explained in answers to this question here ,. English language only. There are ways to check that a website is not storing your data but it is quite complex for anyone without a tech background. This is why both academia and crypto-currency developers are studying solutions to the problem, and we will see exciting developments in these research areas in the next few years. I'm getting aesctr is not available: If you unlock the account you can use this address to sign transactions, You can saving the fancy versions of it e. Export Parity private key this go program on github https:
Wang Wang 1, 2 12 We no longer allow accessing your keystore file using the MyCrypto. In this blog post we have given a small introduction on how to use encrypted queries and why they are bitcoin mining pool software can i buy into bitcoins on a partial basis for smart contracts. Exceptions may be made on a discretionary basis. Choose whether it was a 12 or 24 word phrase, then fill out the form. As explained in answers to this question here. Forgive me if I'm missing something, but how can someone be sure the website is no storing every data one inputs? We are therefore actively working on reducing the footprint of encryption. Smart Contracts A piece of code or program that is stored on the blockchain network. Step 3. This includes, but is not limited to:
Entropy Also known as "randomness". We highly suggest using MEW offline for this option. Home Questions Tags Users Unanswered. This includes, but is not limited to: This tool loads details about your address from your keyfile and displays them in an easily consumable manner. The steps here are heavily influenced by answers to this question. According to documentation , the first 16 bytes are for the next step decrypting the raw key , the second 16 bytes, concatenated with the ciphertext, after going through Keccak hashing, the result should match "mac". Since everyone has a copy of the ledger of all transactions ever executed, there is no need for a third-party. In this blog post we have given a small introduction on how to use encrypted queries and why they are important for smart contracts. You can derive a public key from a private key, but cannot derive a private key from a public key. Do not enter your private key anywhere if you just want to check the balance or see incoming and outgoing transactions. Private keys are the number one most sensitive information anyone can have for a wallet, because private keys allow immediate access and can never be changed.