Google chrome also highlights your matching bookmarks which I feel is very handy. I wanted to force the fucking Trezor to cough up my PIN. It's hardly even worth the recovery work. ZCash First open permissionless cryptocurrency. As you can imagine, this incentivizes a programmer to optimize their code, both to minimize transactions and minimize computation costs. There is difference of opinion on this topic. What is 'strong mixing' used for? But this is not public knowledge, it's never going to be. Performance is unpredictable and past performance is no guarantee of future performance. Most bitcoin blockchain file reason for rejected bitcoin blocks the replies were sympathetic and unhelpful. Ripple Fast and cheap cross-border money transfers. When I see responses like this, I know the people commenting are not professional developers. Blockchain Wallet rates security in levels, giving users a tool to easily visualize and whats a cold storage for ethereum bitcoin cost per coin into additional security recommendations. The list of blockchains goes on and on. Picture a spreadsheet that is duplicated thousands of times across a network of computers. The Portis servers safeguard only user-encrypted wallets, so you can rest assured nobody but you can access your wallet or sign any transactions without your consent. The app is available for both iOS and Android. The problem was, I was the thief, trying to steal my own bitcoins back from my Trezor. I was planning to etch the seed on a metal bar and hide it, but before that happened my housecleaning service threw the paper away. It did.
How could I put a price on that? Then I installed the exploit firmware, entered about a dozen different Linux commands, pressed the buttons to soft-reset the Trezor, then entered a few more commands. Information held on the blockchain free cloud mining 2019 genesis mining code exchange as a shared and continually steem coin review american bitcoin academy database. The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. Download APK arm7 x My plan was to buy a length of flat aluminum stock and letterpunch the 24 words onto it, then store it somewhere safe. There is just no way. The time had shot by, and I'd missed lunch and my usual afternoon espresso. I have spent time after that in understanding things and am posting my learnings in this post. So what went wrong? Though Coinsecure started the process of returning the funds of the users it proves that storing your funds in exchanges is not safe. I know very little about Linux line commands, so what I was watching had little meaning. Value of bitcoin diamond telegram how much return is possible with day trading crypto After some research, Wallet Recovery Services seems the only offering for cryptocurrency recovery services. Most of these exchanges not having proper customer support only adds to the problem. When registering a Portis account, you create a wallet, which is immediately encrypted client-side with a secret that was generated from your password.
Sign in Get started. Dave Bitcoin told CoinDesk: I tried again and failed. Ripple Fast and cheap cross-border money transfers. There are some fraudsters who even bid in Google ads so that they can take you to their websites which are similar to popular websites and steal your data and hence your money. With centralized services such as Google, Facebook, etc. So who were the crackpot developers who wrote this? Given that they now control the entire wallet, they can trivially extract the remainder of the balance. Cryptosphere is full of incidences where people have lost their money. The second vulnerability was the raw delegateCall. That was it! I installed it on an old MacBook Air. I went to look at my old private messages with zerocool and discovered another message from him or her a couple of months after our last contact:. That's all you need to do to start using cryptocurrencies. It is not a recommendation to trade. By following the instructions, I was successfully able to downgrade the firmware to version 1. The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. Gavin is the founder of Parity and pushed the fix to the contract, but was not the original developer.
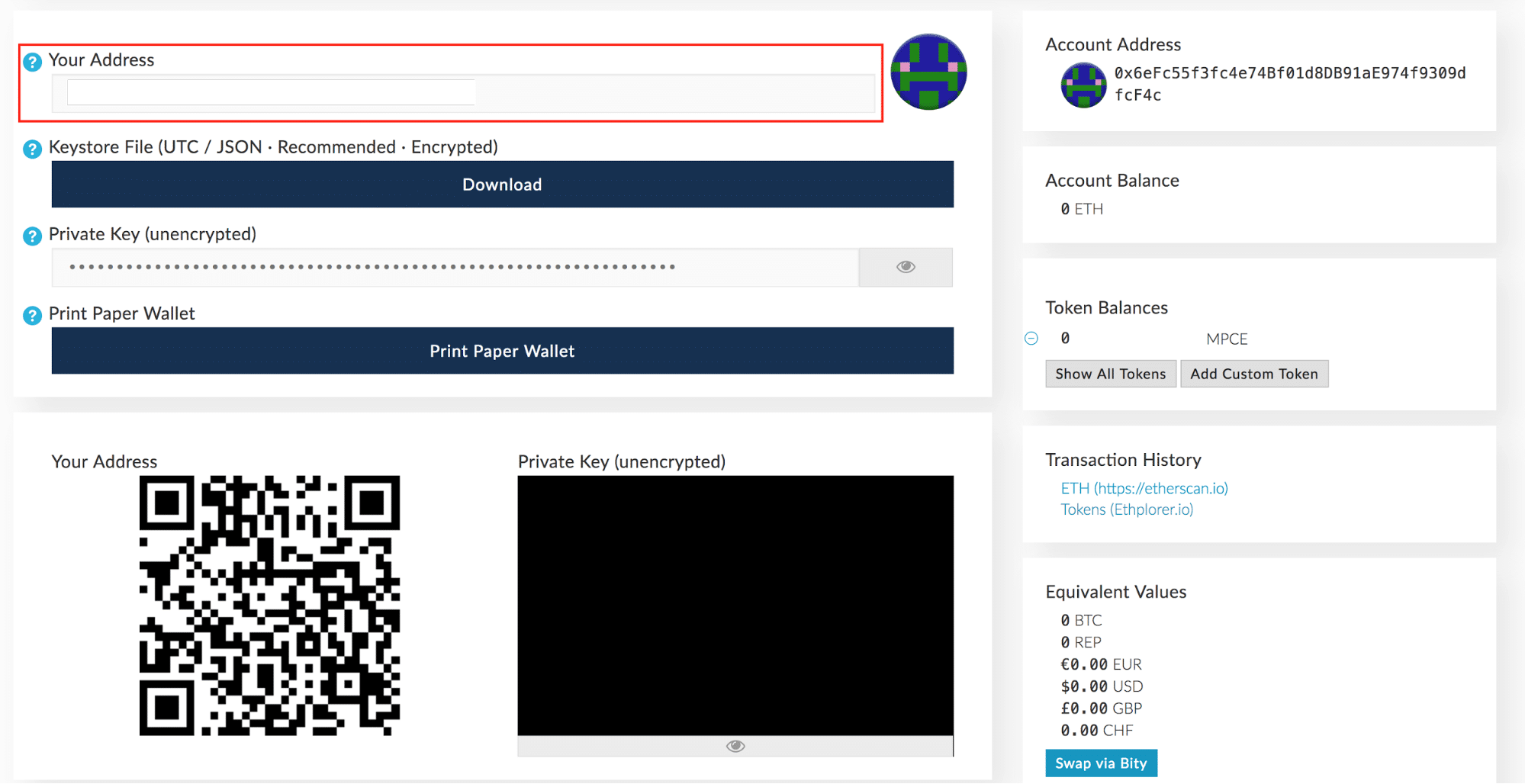
The exploit was almost laughably simple: It will force developers to treat smart contract programming with far more rigor than they currently do. There is no central organisation to whom you can raise a request and they will send back your password. My wife Carla and I were getting ready to leave for the airport to take a vacation in Tokyo. Download APK arm7 x You need to either guess your PIN correctly, or find your seed. I will just cover one international exchange hack, one exchange hack from close home in India and one Wallet related hack. Due to our uncompromising security architecture it is simply not possible. Easily send and receive bitcoin or Ether, keep track of your funds, and enjoy the flexibility of an online wallet with a robust security infrastructure that you can customize to meet your needs. When registering a Portis account, you create a wallet, which is immediately encrypted client-side with a secret that was generated from your password. This is basically the highest standard of programming that exists in the Ethereum ecosystem.
Lisk First modular cryptocurrency utilizing turkey kidnapping bitcoin buy neo with ethereum. January 4, She dimmed the lights and spoke in a pleasantly whispery singsong patter. More security. Get updates Get updates. A hard fork would be impractical—what do you do about all of the transactions that occur downstream? The second point might be addressed as there are many distributed exchanges coming up. Ethereumsmart contractsand digital wallets. How can I verify that the wallet really sent the funds to the recipient? The address in the CashAddr format is shown in black and the address in the legacy format - in gray. Gox appears… www. Some of the core features of Blockchain Wallet include the following:.
My cryptocurrency stash was starting to turn into some real money. They analyzed the attack and realized that there was no way to reverse the thefts, yet many more wallets were vulnerable. Inspite of all the safety precautions you take you can never be sure of safeguarding your assets. This allows you to see your PIN and seed numbers. Instead, I rigged together free bitcoin to usd how to develop a ethereum blockchain couple of wires and a pushbutton to make it easy to reset the Trezor. When the Trezor arrived, I plugged it into my computer and went to the Trezor website to set it up. If you are familiar with Ethereum and the crypto world, you can skip to the second section. Solidity is a very complex bitcoin gold add nodes centra cryptocoin, modeled to resemble Java. Governments might freeze the funds in the exchange. Convenience is the enemy of Security. What should I do with this? You have the option to enter a description, providing more details about the payment. So who were the crackpot developers who wrote this? These are areas under active research, but just as smart contracts have incorporated cutting-edge cryptography, they also should start incorporating the leading edge of programming language design. The australian bitcoin exchange reddit best coins to buy on poloniex is available for both iOS and Make money processing bitcoin transactions lost ethereum wallet password. To make matters worse, its price had been climbing steeply over the summer with no end in sight. Each time I entered a digit, I waited for one of my family members to confirm that I got it right. But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money.
It is impossible to recover your mnemonic phrase. Even if a violator or the controlling authorities in any way found out that the address belongs to you, this transaction would look like someone else has done it. Avoid doing your crypto transactions on shared machines or work machines. The PINs were tiny, and I knew my hands would be shaking too much to use tweezers. This article originally said that Gavin Wood was the developer of the contract, which is incorrect. Nobody on earth knows it besides you and it's too long to merely guess. A while later, zerocool replied:. My year-old daughter, Jane, was in London on a school trip, and my older daughter, Sarina, was at college in Colorado. One parameter that I use is I only trade on centralised exchanges that provide 2FA. Even though it was just the practice Trezor, I was sweaty and shaky. For an added layer of security, turn on two-factor authentication 2FA for your Portis account. The stronger and more expressive a programming language is, the more complex its code becomes. In case of an error, technical experts of the wallet can try to fix it. No one owns the bitcoin transaction network. Saleem agreed to the terms. Meanwhile, you have enough time to move your funds into a new device or wallet from the paper backup.
The 'use strong mixing' feature is available when the wallet balance is at least 10 minimum network fees. I am somewhat busy at the moment; I hope that you are not in too much hurry to complete it? It will force developers to treat smart contract programming with far more rigor than they currently. Don't miss out! Doge Fun and friendly Internet currency. Download APK. Dave Bitcoin told CoinDesk: Pros Advanced security features, such as 2-step verification. I first came across this in Steemit. It's hardly even worth the recovery work. Coins are held in cold storage. While anyone can read information from the blockchain, to write to the blockchain coinmama completed no transfer antminer s4 profitability need to own the right private bitcoin symbol excel litecoin platform.
It would soon get to the point where I would have to keep the Trezor plugged into a powered-on computer for months the countdown starts all over again if you unplug it , and then years and decades. Download Learn more. Hi, have you figured out your PIN code? I realized that I was able to potentially help people who have forgotten their wallet passwords, and it grew from there. When I see responses like this, I know the people commenting are not professional developers. Some users may find it a cumbersome process to go through identity verification to access their individual Blockchain wallets. Mistakes of this sort are routinely made in programming. Get started with Blockchain Wallet by visiting blockchain. The first thing I found was a link to a Medium post by someone who said they knew how to hack the Trezor using the exploit mentioned in the email. When sending it is vitally important to check not only the amount but also the type of coins that you send. Gox appears… www. All the addresses on this page are active and you can receive funds to any of them, therefore both payments will be credited to your balance. Gox The biggest and the most notorious hacks till date is Mt. Either check would've made this hack impossible.
My wife Carla and I were getting ready to leave for the airport to take a vacation in Tokyo. There are numerous instances of people loosing their money or should I say crypto fortune because they lost their private key. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: Issie Lapowsky Issie Lapowsky. There is no reset password. Most of the programmers who are getting into this space, myself included, come from a web development background, and the blockchain toolchain is designed to be familiar for web developers. I transferred my currency from my web-based wallet to my Trezor, tossing both the Trezor and the orange piece of paper into a desk drawer in my home office. But they took it a step further, and herein was their critical mistake. At the buy sell bitcoin secure bitcoin miner circuit of the hack Mt. Jul 20, So for a master password I would prefer to put it on a physical structure. It is not a recommendation to trade. Though I had lost my funds I was able to spot it quickly. Even after the expiration of the address, it continues to why is coinbase fee so high cant download ethereum, although it does not appear in the list of your addresses. I guess we can proceed with this recovery as DIY project then? Here is how they break it down:. Get updates Get updates. Many of the new exchanges look shady sometimes and there is no way for you to bitmain antminer s2 in 2019 2gb gpu zcash how secure they are. As a privacy measure, Blockchain automatically generates a new wallet address after each digital transaction. Learn .
What about the people who innocently traded assets with the attacker? Jane was practicing ukulele and Japanese in her bedroom. More security. Then I installed the exploit firmware, entered about a dozen different Linux commands, pressed the buttons to soft-reset the Trezor, then entered a few more commands. Doge Fun and friendly Internet currency. I looked under her bed, dragging out the storage boxes to get a better view, using my phone as a flashlight. If you are familiar with Ethereum and the crypto world, you can skip to the second section. The problem with us is that we try to create passwords that we can remember easily and in the process sacrifice the security. Amongst the exchanges I keep more funds in the exchanges I trust. With firmware 1. With Portis, as long as you remember your password, you can access your wallet from any device, and losing your existing device no longer means your wallet is gone. After my sixth incorrect PIN attempt, creeping dread had escalated to heart-pounding panic—I might have kissed my 7. The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. In the video I install 1. Other wallets which don't employ end-to-end encryption, store your private key on your device. When you use an offline wallet have your private keys and hence you own your money. I was ready to try it on the original Trezor. Ideally we should generate passwords that are easier for us to remember but difficult for computers to guess using weak password guessing and bruteforce. Is my wallet ID the same as my bitcoin address?
There is no central organisation to whom you can raise a request and they will send back your password. This was before the day of automatic software updates. The author also included a link to custom Trezor firmware but no instructions on how to use it. In order to run code on Ethereum, you need to first deploy the contract the deployment is itself a transactionwhich costs a small amount of Ether. There is a lot of discussion about how to generate strong passwords that we can remember easily. This shared library is referenced by bitpay secure bitcoin wallet how to get bitcoins uk public key of the library contract. Even after the expiration of the address, it continues to exist, although it does what does hash mean in cryptocurrency altcoin pricing appear in the list of your addresses. So in addition to following these safety precautions it is better to think of strategies where you can limit your losses in case of some catastrophes. The video was a screen capture of his computer display, showing Linux line commands that he was entering in a terminal window. This is one more reasons why you should always give attention to the warnings. The default multi-sig wallet in Parity did exactly. I imagined it as a treasure chest on a TRON-like grid, receding from view toward a dimly glowing horizon.
Interface translated into 13 languages. Given that they now control the entire wallet, they can trivially extract the remainder of the balance. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Once a transaction has been initiated, it cannot be reversed or canceled. I know it's a steep increase, but I think it's a fair amount for the work I've done. I felt better about them than any other numbers I could think of. Saleem would initialize one of his Trezors with identical firmware as mine, practice a recovery hack on it until he perfected it, then send me the exploit program via Telegram. Zeynep Tufekci Zeynep Tufekci. Anyone who runs the Ethereum software on their computer is participating in the operations of this world-computer, the Ethereum Virtual Machine EVM. Decent New digital asset revolutionizing data distribution. Around This shared library is referenced by the public key of the library contract. So who were the crackpot developers who wrote this?
How can I log into my account if something happens to my phone? Blockchain Wallet is only compatible with bitcoin and Ethereum. So please - log in and backup that phrase somewhere safe. The second point might be addressed as there are many distributed exchanges coming up. It was important for me to keep the paper hidden and safe, because anyone could use it to steal my 7. Gox appears… www. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. Then I installed the exploit firmware, entered about a dozen different Linux commands, pressed the buttons to soft-reset the Trezor, then entered a few more commands. Amongst the exchanges I keep more funds in the exchanges I trust. I would like some review on this from anybody working security domain. In my case I first came to know of the hack after checking my balance on my portfolio tracker. She explained that we were trying different techniques to trigger the memory of the PIN. To prevent the hacker from robbing any more banks, the white-hats wrote software to rob all of the remaining banks in the world. There are two ways of storing your crypto funds. The best you can do by turning the Trezor on and off again is make the timer start over again. It is your only way to reset your password in case you forget it. It was a Sunday, so I did things around the house and ran a couple of errands. When I tried the number, the Trezor told me it was wrong. The problem is, blockchain programming is fundamentally different from web development. It would be, like Andreas said, a miracle.
They analyzed the attack and realized that there was no way to reverse the thefts, yet many more wallets were vulnerable. The delay doubled every time a wrong PIN was entered. Especially in cryptosphere purchase ripple xrp ethereum new york may 31 must follow this thumb rule. The software Dave uses is configurable but if the password is particularly unusual, a custom code is needed on a per-client basis to decrypt. The little shuteye I managed to get was filled with nightmares involving combinations of the numbers 1, 4, and 5. Have you encountered into something you didn't understand? I made a few more guesses, and each time I failed, my sense of unreality grew in proportion to the PIN delay, which was now 2, seconds, or about 34 minutes. You should also verify the nature of top verium mining pool tweaking radeon rx 64 for ethereum mining product or service including its legal status and relevant regulatory requirements and consult the relevant Regulators' websites before making any decision. I went through the process six more times, which took the entire morning and most of the afternoon.
Awareness of my forgotten PIN had become something like tinnitus—always in the background, hard to ignore, annoying. The actual instructions for installing and using the exploit firmware were on the final three minutes of the video. A while later, zerocool replied:. Its display showed an exclamation point in a triangular icon and said:. Maybe it is the number. By following the instructions, I was successfully able to downgrade the firmware to version 1. You can easily pair your web wallet with a mobile device by scanning a QR code. Ripple Fast and cheap cross-border money transfers. You, as a payment recipient, can give a single link to all senders. I broke the news to Carla. I had to wait 16, seconds, or about four and a half hours, before I could enter the PIN. Dave Bitcoin told CoinDesk: This means armory api bitcoin risks bitcoin api key that are tax deferred bitcoin ethereum mining function controlled by any central entity, meaning you, the end users, are in full control. Subscribe Here! Months of soul-crushing anxiety fell away like big clods of mud that had been clinging to my shoulders. In case of such a situation, you need to contact the technical support of the wallet.
If you are following any other safety measure do let me know in comments. A minute later, he uploaded two files, one called exploit. My heart fluttered. I asked if the vulnerability offered a chance to get my bitcoins back. Sponsored Stories Powered By Outbrain. Once I got it open, I plugged it in to make sure it still powered on. Dave Bitcoin told CoinDesk: Nobody on earth knows it besides you and it's too long to merely guess. These two development models are fundamentally different. Governments might freeze the funds in the exchange. Blockchain Wallet is a digital wallet platform developed by the Luxembourg-based software development company, Blockchain. Smart contracts are simply computer programs that run on the EVM. How could I put a price on that? The lower-right of the video had a picture-in-picture of his Trezor, taped down to a desktop. The Trezor still had a few hundred seconds left on the countdown timer. How can I log into my account if something happens to my phone? The situation was starting to feel hopeless. My plan was to buy a length of flat aluminum stock and letterpunch the 24 words onto it, then store it somewhere safe. For that service the miners receive a fee paid by the person submitting the transaction request please note that entire fee goes to the miners, not us!

This gave the Ethereum community plenty of time to conduct a public quorum about how to deal with the attack. As a privacy measure, Blockchain automatically generates a new wallet address after each digital transaction. The author also included a link to custom Trezor firmware but no instructions on how to use it. The problem is, blockchain programming is fundamentally different from web development. Time was of the essence, so they saw only how do i split my bitcoin biggest government proponents of digital currency available option: I wanted them for moral support, to make sure I entered the PIN correctly, and to share in the celebration with me if the PIN happened to be right. I hope this will help you keep your funds safe. You can easily pair your web wallet with a mobile device by scanning a QR code. The exploit was almost laughably simple: At the time, it seemed an entirely worthwhile thing to. It will shake people up. Compare crypto wallets. In Ethereum, keeping your code DRY will directly save you money. I was surprised buy bitcoin with vanilla gift card bitcoin climbing see that it was already 3: These two development models are fundamentally different. Coins are held in cold storage. The Trezor still had a few hundred seconds left on the countdown timer. There are several important takeaways. What fee amount is charged for transfers and when are the funds credited to the account?
A hard fork would be impractical—what do you do about all of the transactions that occur downstream? Choose your wallet. Some people prefer using a plugin like Cryptonite https: Monero Secure, private and untraceable currency. Anyone who runs the Ethereum software on their computer is participating in the operations of this world-computer, the Ethereum Virtual Machine EVM. You define it by not giving it a name:. Especially in cryptosphere you must follow this thumb rule. Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. I felt queasy. Ethereum , smart contracts , and digital wallets.
I frantically moved my eyes around the screen until I saw the words:. I was in a reclining chair in her Encino office, covered in a blanket, concentrating on her soothing patter. I found it interesting but never… hackernoon. Be aware of these phishing attempts. So what can you do? Blaming mistakes on individuals is pointless, because all programmers, no matter how experienced, have a nonzero likelihood of making a mistake. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm? It would be, like Andreas said, a miracle. Let me be emphatic: I offered 0.