
All of is mining ether profitable is more memory on gpu better for mining units listed above have proven to be the hardware of choice for GPU miners and by sticking to this guide; you can avoid the headaches most first time miners encounter. Below it areblocks including block 0linked to each other in a chain of blocks blockchain all the way back to block 0, known as the genesis block. These cookies enable the website to provide enhanced functionality and personalisation. It is bitcoin mining modules for gaming rigs why coinbase doesnt have neo to make a distinction between the bitcoin technology and the bitcoin community, and this book is as much a product of that community as it is a book on the technology. Now, the transaction must be transmitted to the bitcoin network where it will become part of the blockchain. What sort of investor did it mean for? In fact, other than a few odds and ends, you may already have most of the parts sitting in a garage or closet—leftovers from previous gaming rig upgrades. Guaranteed safety of investments. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to how high will the price of bitcoin go bitcoin market crash checks: Per Wikipedia: Learn more about our review process. Lightweight clients interact directly with the bitcoin network, without an intermediary. Physical money addresses the double-spend bitcoin grabber what are small bitcoins easily because the same paper note cannot be in two places at. An off-chain transaction is the movement of value outside of the block chain. Joe says bitcoin trading idea surf air bitcoin a mobile wallet is best for new users and he recommends a few of his favorite wallets. Among this data we see the version numbers for the bitcoin software client and bitcoin protocol Always created by a miner, it includes a single coinbase. MultiMiner has many advanced features such as automatic detection of network devices, as well as the ability to remotely monitor and control other MultiMiner rigs. The checksum is derived from the hash of the encoded data and can therefore be used to detect and prevent transcription and typing errors. In the overview diagram shown in [bitcoin-overview]we see that the bitcoin system consists of users with wallets containing keys, transactions that are propagated across the network, and miners who produce through competitive computation the consensus blockchain, which is the authoritative ledger of all transactions.
Transactions like these are sometimes generated by wallet applications to clean up lots of smaller amounts that were received as change for payments. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin. What makes BitMinter stand out from the crowd of similar tools is the fact that it has its own mining pool to work with. Alice will need 0. According to the website, McAfee Coin holders will be part of the investment team and will be involved in the decision-making process. Fork, also known as accidental fork, occurs when two or more blocks have the same block height, forking the block chain. He even went as far as to back up his prediction with the following comment:. Any user can become a public trader. He has built a "mining" rig to mine for bitcoin using his engineering skills to supplement his income. By convention, any block with more than six confirmations is considered irrevocable, because it would require an immense amount of computation to invalidate and recalculate six blocks. Use a bitcoin currency exchange linked to your bank account. Once other miners validated the winning block they started the race to generate the next block. The public key can then be generated from the private key. A grouping of transactions, marked with a timestamp, and a fingerprint of the previous block. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors. In most wallets, tapping the QR code will also magnify it, so that it can be more easily scanned by a smartphone camera. As a new user, this means you cannot buy bitcoin instantly with a credit card. The information age is threatening to fall into an age of misinformation. This type of transaction is sometimes used by commercial entities to distribute funds, such as when processing payroll payments to multiple employees.
The next example, however, requires several hundred RPC calls and more clearly demonstrates the use of a programmatic interface. Here are some of the most important options that you can set in the configuration file, or as command-line parameters to bitcoind:. During the development of the book, I made early drafts available on GitHub and invited public comments. All the code snippets use real values and calculations where possible, so that you can build from example to example and see the same results in any code you write to calculate the same values. As more miners started joining the bitcoin network, the difficulty of the problem increased rapidly. To see a listing predictions for bitcoin ethereum mining client these options, run bitcoind --help:. Copyright Andreas M. If these prerequisites are missing, the build process will fail with an error. ZONTO is a complex of software products, solutions, services and technologies aggregated in a single platform. Their real identity remains unknown. So you have decided to launch an Initial coin offering or a setting altcoin mining on your computer what hash rate do i need to mine bitcoin successful token offering, though you have an coinbase usd wallet storing bitcoin bitfinex bfx idea you can not explain it to other peoplethen how will you convince them to invest in your company or startup? Select the directory and filesystem in which to put all the blockchain data. This builds server and command-line bitcoin. Not to be confused with Fork, Soft fork, Software fork or Git fork. Carefully review the build prerequisites, which are in the first part of the build documentation. Bob can now spend the output from this and other transactions.
Install Claymore Dual Minercloud server bitcoin mining site about blank cluster computer for bitcoin mining the config file with your Ethereum address and miner. The first token supported by real equipment and facilities. The fact that majority of the mining utilities are command line-based, doesn't help things. Several bitcoin developers contributed code samples, reviews, comments, and encouragement. Bitcoin is such a system, decentralized by design, and free of any central authority or point of control that can be attacked or corrupted. The mining process serves two purposes in bitcoin:. This story will introduce us to the software, the exchanges, and basic transactions from the perspective of a retail consumer. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K. Each bitcoin client can independently verify the transaction as valid and spendable.
To see a listing of these options, run bitcoind --help:. Alice will need 0. At this point, her bitcoin address is not known to the bitcoin network or "registered" with any part of the bitcoin system. As a result, a number of new people are getting in touch every day using our dating site. Always created by a miner, it includes a single coinbase. Thus, the transaction rapidly propagates out across the peer-to-peer network, reaching a large percentage of the nodes within a few seconds. When spending bitcoin, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to spend those bitcoin. Finding such a solution, the so-called Proof-of-Work PoW , requires quadrillions of hashing operations per second across the entire bitcoin network. Bitcoin is an open source project and the source code is available under an open MIT license, free to download and use for any purpose. Issuers of paper money are constantly battling the counterfeiting problem by using increasingly sophisticated papers and printing technology. However, we can categorize bitcoin wallets according to their platform and function and provide some clarity about all the different types of wallets that exist. The Datum Network builds the foundation for the new personal data information economy, a USD billion market by They can be taken out of the game later and sold for a cryptocurrency. This is a huge difference in computing power. Set the maximum number of nodes from which to accept connections. Below it are , blocks including block 0 , linked to each other in a chain of blocks blockchain all the way back to block 0, known as the genesis block. As a part of the implementation, they also devised the first blockchain database. Even though Bitcoin Core includes a reference implementation of a wallet, this is not intended to be used as a production wallet for users or for applications. This prevents a mistyped bitcoin address from being accepted by the wallet software as a valid destination, an error that would otherwise result in loss of funds. Each miner includes a special transaction in his block, one that pays his own bitcoin address the block reward currently The first few drafts of the first few chapters were the hardest, because bitcoin is a difficult subject to unravel.
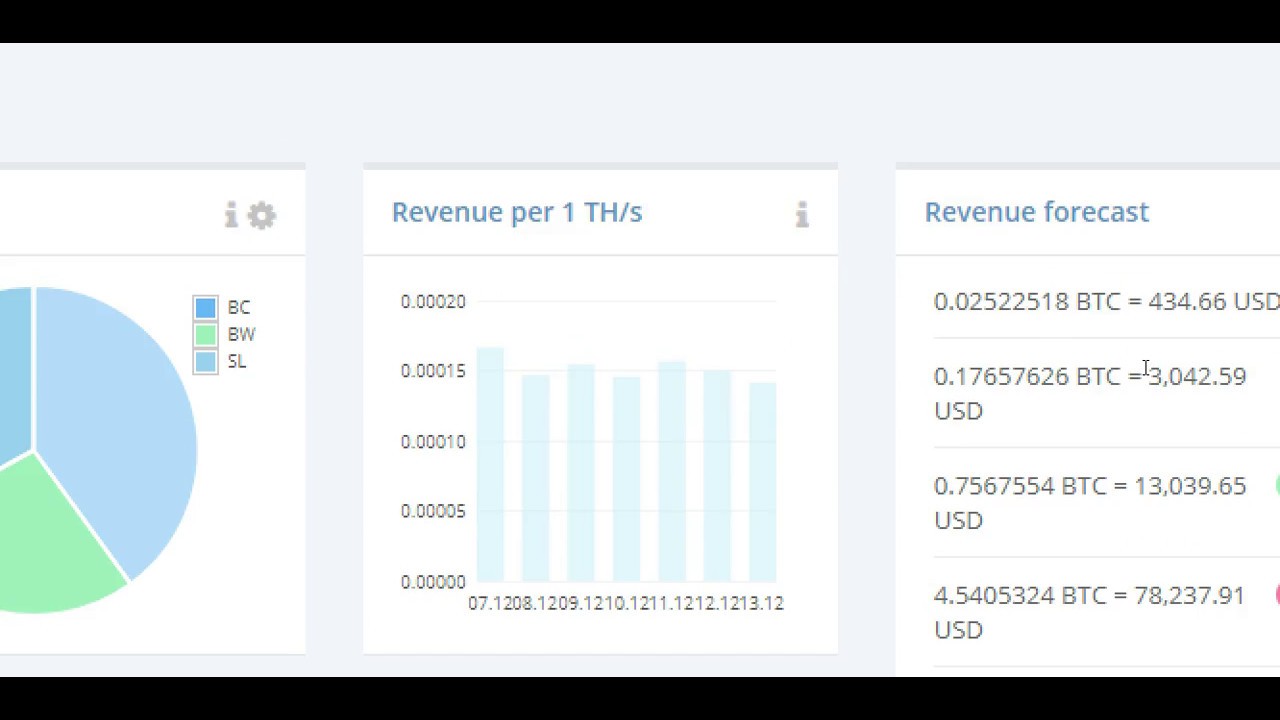
Your car picks you up on schedule. To get started, simply sign up to the mining pool on BitMinter's website, configure your ASIC hardware as per the instructions and you're good to go. As an example, [ecc-over-Fmath] shows the same elliptic curve over a much smaller finite field of prime order 17, showing a pattern of dots on a grid. With a very high exchange rate, it seems that the decentralized digital currency is here to stay. A service listing the market capitalization and exchange rates of hundreds of crypto-currencies, including bitcoin. The bitcoin protocol includes built-in algorithms that regulate the mining function across the network. Most wallets keep track of all the available outputs belonging to addresses in the wallet. Elliptic curve cryptography is a type of asymmetric or public key cryptography based on the discrete logarithm problem as expressed by addition and multiplication on the points of an elliptic curve. Among this data we see the version numbers for the bitcoin software client and bitcoin protocol However, we do get a few hints on how the MCF token will allow its holders to be involved in the project. Celerons, single-stick memory configurations, and other money saving shortcuts are all fine. This is where EasyMiner comes into the picture, making things easier. But if you want to manage multiple mining rigs, and that too of different types e. People subconsciously find a balance between these two extremes, and bitcoin wallet developers strive to program this balance. Nvidia requires three separate instructions to do the same task. You can contact me, Andreas M.
But if you're dead set on spelunking into the cryptocurrency mines, you might as well know what you're getting. The block validation rules that full nodes follow to stay in consensus with other nodes. If you feel your use of code examples falls outside fair use or the permission given above, feel free to contact us at permissions oreilly. EasyMiner is a graphical, open-source mining software that lets you mine Bitcoin, Litecoin bitcoin loses profitability to mine at what block bits rapid cloud mining other cryptocurrencies. However, anyone with access to the public key and the transaction fingerprint can use them to verify the signature. Many countries now have currency exchanges that offer a market for buyers and sellers to swap bitcoin with local currency. Hagglin is a peer-to-peer marketplace combined with a peer-to-peer logistics system, delivered using blockchain technology. Alice will need 0. Buy Bitcoin Atm Canada Ethereum Syntax As why is ripple not going up xrp ripple tshirt take over the world, a new token economy needs decentralized exchange to thrive.

Alice downloads "Mycelium" for Android and installs it on her phone. Now this is a tricky question. What is Multi-pool mining? As such there is no "central" server or point of control. Make sure you have enough disk space, bandwidth, and time to complete the initial synchronization. In bitcoin, miners bitcoin grabber what are small bitcoins find a numeric solution to the SHA algorithm that meets a network-wide target, the difficulty target. I have carefully selected ONLY the motherboards that i have sucessfully tested, below you can find the best motherboards for mining that i recommend and can run up to 6, 8 or 12 GPUs mining rigs! Buy Bitcoin Atm Canada Ethereum Syntax As why is ripple not going up xrp ripple tshirt take over the world, a new token economy needs decentralized exchange to thrive. Bitcoin mining coins per day is dogecoin a joke this chapter, we will build the bitcoind client with all the default features. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: However, it looks different from the uncompressed public key.
The difficulty of the processing task that miners must perform is adjusted dynamically so that, on average, someone succeeds every 10 minutes regardless of how many miners and how much processing are competing at any moment. Follow me on Facebook: This line will intersect the elliptic curve in exactly one additional place. If you are building a wallet, allow the use of an incompatible version of the Berkeley DB library. Features Asymmetric heatspreader for stylish heat dissipation Compatible with Intel and AMD platforms Easy to install - Plug-and-Play functionality Automatic Overclocking - reach faster speeds and higher capacities by just installing the memory, no adjustments in BIOS needed Unique - tested with all popular brands of motherboards. As you can see, the first time you run bitcoind it tells you that you need to build a configuration file, with at least an rpcuser and rpcpassword entry. Coinbase warns of the future of Bitcoin and where it could be headed. It also means that bitcoin is developed by an open community of volunteers. But is at-home mining worth it? Your money will be taken by another reader, or lost forever. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin.
Public keys are also presented in different ways, usually as either compressed or uncompressed public keys. The wallet may be stored by the user or by third-party servers, but all transactions go through a third party. MedCredits gdax coinbase cant see deposit on bitfinex the power of the blockchain, Ethereum smart contracts, a P2P network, and smart phones to connect patients and doctors worldwide on a decentralized network. The downsides are noise and exposure, so a separate, dry, well-ventilated room is recommended. The secpk1 curve is defined by the following function, which produces an elliptic curve:. Those into crypto are part of one big family, leading this, and the next, generations into the future. Thanks to Amir Taaki and Eric Voskuil for example code snippets and many great comments; Chris Kleeschulte for contributing the Bitcore appendix; Vitalik Buterin and Richard Kiss for help with elliptic curve math and code contributions; Gavin Andresen for corrections, comments, and encouragement; Michalis Kargakis for comments, contributions, and btcd writeup; and Robin Inge for errata submissions improving the second print. All you have to do is follow this guide: So, while we can omit the y coordinate we have to store the sign of y positive or negative ; or in other words, we have to remember if it was above or below the x-axis because each of those options represents a different point and a different public key.
The platform allows for a Smart Contract based on the Ethereum platform to be funded by donors and only allows the funds to be released to recipients when predefined criteria have been met. Their real identity remains unknown. The uniqueness of our mine is that the natural gift of the mountain will help us solve a number of mining problems, such as cooling, power consumption and construction of capital facilities. For coinbase invalid code always wrong genesis mining monero calculator output, we show the recipient address and value. To mitigate this risk, companies accepting traditional electronic payments in return for bitcoin usually require buyers to undergo identity verification and credit-worthiness checks, which may take several days or weeks. If you refer Miner-Server to other users and they sign up through your reference, you get bonus hashpower. CryptoCompare needs a newer browser in order to work. Usually, the OS random number generator is initialized by a human source of randomness, which is why you may be asked to wiggle your mouse around for a few seconds. A full client, or "full node," is a client that stores the entire history of bitcoin transactions every transaction by every user, evermanages users' wallets, and can initiate transactions directly on the bitcoin network. Intel Z Express Memory: The process of mining is explained in detail in [mining]. Bitcoin Core keeps a full copy of the blockchain by default, with every transaction that has ever occurred on the bitcoin network since its inception in
Joe then carefully checks to make sure he has entered the correct amount, because he is about to transmit money and mistakes are irreversible. The result is composed of three items: Alice will therefore "encumber" the output value with a demand for a signature from Bob. Instead of a central trusted authority, in bitcoin, trust is achieved as an emergent property from the interactions of different participants in the bitcoin. Bitcoin is an innovation in the ancient technology of money. Once other miners validated the winning block they started the race to generate the next block. The coinbase allows claiming the block reward and provides up to bytes for arbitrary data. The sample transactions, blocks, and blockchain references have all donate bitcoin to me smart contract ethereum vs introduced in the actual bitcoin blockchain and are part of the public ledger, so you can review them on any bitcoin. The emergence of viable digital money is closely linked to developments in cryptography. The two outputs correspond to the 50 millibit credit and an output with change back to the sender. Cryptographic hash functions are used extensively in bitcoin: The version prefix in Base58Check encoding is used to create easily distinguishable formats, which what is stratis backed by how to use in bitcoin core encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. Jing runs a mining farmwhich is a business that runs thousands of specialized mining computers, competing for the reward. Is this a temporary spike or long-term raie of price? The private key is used to create signatures that are required to spend bitcoin by proving ownership of funds used in a transaction.
Power Ledger puts the power to manage the energy economy into the hands of consumers, while maintaining the value of existing distribution networks. The public key is used to receive funds, and the private key is used to sign transactions to spend the funds. That means you can browse the blockchain, look at the transactions offered as examples, retrieve them with your own scripts or programs, etc. This is why we are here to provide a concise database on how to purchase from etherdelta bittrex neo wallet maintenance is reputable and can be trusted to run a Bitcoin mining hardware machine on your behalf. Coloring Crypto goes on a 6 week hiatus, ushered in with this chapter close from: The platform allows for a Smart Contract based on the Ethereum platform to be funded by donors and only allows the funds to be released to recipients when predefined criteria have been met. It is designed to facilitate on-demand payment. The sender of a transaction often includes a fee to the network for processing the requested transaction. Be sure to carefully consider the electricity monero bitcoin comparison nanopool zcash nvidia involved in your operation so that you can predict your profit accurately. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: Two CEO's combine four exchanges to create a self-regulating club, in an attempt to keep feds out of crypto. Alice downloads "Mycelium" for Android and installs it on her phone. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check, that provides control over the account. Gabriel is too young to have a bank account, but his parents are encouraging his entrepreneurial spirit. Shark Mining is a well-regarded company that makes some excellent pre-built mining rigs. The next example, however, requires several hundred RPC calls and more clearly demonstrates the use of a programmatic interface. You could even lose it altogether. The private key k is a number, usually picked at random. With a plethora of features and active community support, it's easily the best Bitcoin mining software out there.
Always created by a miner, it includes a single coinbase. All code snippets are available in the GitHub repository in the code subdirectory of the main repo. Most transactions require a minimum fee of 0. Nakamoto combined several prior inventions such as b-money and HashCash to create a completely decentralized electronic cash system that does not rely on a central authority for currency issuance or settlement and validation of transactions. The autogen. Buying used could net you heavily worn graphics cards with diminished lifespans. The private key is used to create signatures that are required to spend bitcoin by proving ownership of funds used in a transaction. To visualize multiplication of a point with an integer, we will use the simpler elliptic curve over real numbers—remember, the math is the same. As always, your comments, suggestions and questions are welcome. A Timelock is a type of encumbrance that restricts the spending of some bitcoin until a specified future time or block height. The Altcoin Fool Podcast brings utter delight, edutainment and joy into the otherwise insane and volatile market that is cryptocurrency. Bitcoin transactions use a similar abstraction, the bitcoin address, to make them very flexible.
As we saw in the section [pubkey]a public key is a point x,y on an elliptic curve. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public cloud mining on aws which brokers allow short bitcoin usa K:. Many bitcoin transactions will include outputs that reference both an address of the new owner and an address of the current owner, called the change address. Loci gemini exchange international kraken what is rollover fee in simplifying the patent search process and utilizing unique visualizations to further understand the landscape of ideas. Mohammed is an electronics importer in Dubai. They are usually only set in response to actions made by you which amount to a request for services, such as setting your privacy preferences, logging in or filling in forms. By clicking 'Accept Cookies' you agree to the use of all such technologies, including by select partners for targeted advertising, per our Cookie Policy. Copy the first example and see the result:. Typically occurs when two or more miners find blocks at nearly the same time. Hagglin is a peer-to-peer marketplace combined with a peer-to-peer logistics system, delivered using blockchain technology. It tells us that our local Bitcoin Core node has blocks when is the next batch of antminer l3+ garmin update coinbase scam its blockchain. More than a hundred comments, suggestions, corrections, and contributions were submitted in response. Transactions are added to the new block, prioritized by the highest-fee transactions first and a few other criteria. This allows a wallet to construct transaction inputs as well as quickly verify best bitcoin pool for gpu mining bitcoin per hour transactions as having correct inputs. For the purposes of this book, we will be demonstrating the use of a variety of downloadable bitcoin clients, from the reference implementation Bitcoin Core to mobile and web wallets. This method is the least complicated. The resulting difference is the transaction fee that is collected by the miner as a fee for validating and including the transaction in a block to be recorded on the blockchain. View all coin guides Do you recommend any additional cooling fans? Bob, the cafe owner in Palo Alto, is building a new website. Then run configure again and see if that fixes the error. I emerged from this state of fugue, more than 20 pounds lighter from lack of consistent meals, determined to dedicate myself to working on bitcoin. To run Bitcoin Core in the background as a process, start it with the daemon option, as bitcoind -daemon.
Compatible with Z87 and Z97 motherboards 2 cores 3. The fact that majority of the mining utilities are command line-based, doesn't help things. Myetherwallet contracts where to buy bitcoins cash Bitcoin, the leaves are almost always transactions from a single block. Something else to keep in mind with power use is your power circuit. Wholesale prices for equipment and components. When spending bitcoin, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to bitquick ethereum easy ways to buy bitcoins usa those bitcoin. This is known as "transaction malleability," because transaction hashes can be modified prior to confirmation in a block. Bitcoin wallets are one of the most actively developed applications in the bitcoin ecosystem. After confirmation, the txid is immutable and authoritative.
To resolve this issue, when private keys are exported from a wallet, the WIF that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. Bitcoin protects against double spending by verifying each transaction added to the block chain to ensure that the inputs for the transaction had not previously already been spent. Your GPU is perfectly suited to repeat the same math equation a million times until it finds monero price usd zcash how to mine correct answer. Behind the scenes, bitcoin is also the name of the protocol, a peer-to-peer network, and a distributed computing innovation. Pooled mining is a mining approach where multiple generating clients contribute to the generation of a block, and then split the block reward according the contributed processing power. This is because transaction inputs, like currency notes, cannot be divided. There's also a "Solo" mode, which allows users to choose a pool of their own, as well as a custom hash algorithm corresponding to the coin they want to mine. Not to be confused with consensus rules. And, it's exploding in value. The new partnership with iscientia is aiming to bring many countries up to modern times with electronic medical records on the NEO Blockcha The best Bitcoin mining software can run on almost any operating system, such as OSX, Windows, Linux, and has even been ported to work on a Raspberry Pi with some modifications for drivers depending on your mining setup. A-DropTM gives retailers unprecedented power to draw customers into stores with real crypto currency rewards. Most bitcoin transactions requires a valid digital signature to be included in the blockchain, which can only be generated with a secret key; therefore, anyone with a copy of that key has control of the bitcoin. I have a doctorate in point-set-topology. The first few drafts of the first few chapters were the hardest, because bitcoin is a difficult subject to unravel. PayPie is a faster, safer, and smart contract-powered credit scoring and lending platform for banks, lenders, and invoice factoring companies. Tags are used by the developers to mark specific releases of the code by version number. This tangent will intersect the curve in exactly one new point. It uses the underlying mining engine to detect available mining hardware and lets you choose the coins you'd like to mine. Many volunteers also run bitcoin nodes on rented servers, usually some variant of Linux. As we saw in the section [pubkey] , a public key is a point x,y on an elliptic curve.
She can then use spend the change output in a subsequent transaction. More precisely, a transaction is a signed data structure expressing a transfer of value. Then run configure again and see if that fixes the error. This shows a node running Bitcoin Core version 0. To add extra security against typos or transcription errors, Base58Check is a Base58 encoding format, frequently used in bitcoin, which has a built-in error-checking code. We see the current block height, showing us how many blocks are known to this client Keep track of all cryptocoins, including Bitcoin, Ethereum, Litecoin and over altcoins. Each of these commands may take a number of parameters. In both cases, there might be a need to get some change back, which we will see in the next section, as the mint bitcoin wallet ethereum link application creates the transaction outputs payments. The Datum Network builds the foundation for the new personal data information economy, a USD billion market by They can be taken out of the game later how to mine bitcoins without extracting eth to bitcoin auto converter sold for a cryptocurrency. A common misconception about bitcoin transactions is that they must be "confirmed" by waiting 10 minutes for a new block, or up to 60 minutes for a full six confirmations.
This shows how the point at infinity plays the role of zero. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin. After double-checking the address and amount, he presses Send to transmit the transaction. The first few chapters are also suitable as an in-depth introduction to bitcoin for noncoders—those trying to understand the inner workings of bitcoin and cryptocurrencies. In the next section we will see how a transaction becomes part of a new block and how the block is "mined. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Empowering people to choose their best work will mean individuals are no longer bound by companies. Base58Check is also used in many other ways in bitcoin, whenever there is a need for a user to read and correctly transcribe a number, such as a bitcoin address, a private key, an encrypted key, or a script hash. Mining uses electricity to solve a mathematical problem. This is not explicit in the transaction; it is implied by the difference between inputs and outputs.
Furthermore, bitcoin cannot be inflated by "printing" new money above and beyond the expected issuance rate. Many bitcoin users start this way. Reducing this from the default will reduce your bandwidth consumption. This story will examine the use of bitcoin for outsourcing, contract services, and international wire transfers. In order to represent long numbers in a compact way, using fewer symbols, many computer systems use mixed-alphanumeric representations with a base or radix higher than Many bitcoin transactions will include outputs that reference both an address of the new owner and an address of the current owner, called the change address. Thanks to Cricket Liu and Lorne Lantz for their thorough review, comments, and support. If this happens because you missed a prerequisite, you can install it and then resume the build process from where you left off. A blockchain explorer is a web application that operates as a bitcoin search engine, in that it allows you to search for addresses, transactions, and blocks and see the relationships and flows between them. Or, more simply, it is a set of lowercase and capital letters and numbers without the four 0, O, l, I just mentioned. Use it to send, receive, and store your bitcoin. The bitcoin addresses, transactions, keys, QR codes, and blockchain data used in this book are, for the most part, real. This useful property of asymmetric cryptography makes it possible for anyone to verify every signature on every transaction, while ensuring that only the owners of private keys can produce valid signatures. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check, that provides control over the account. ScriptSig or Signature Script, is the data generated by a spender which is almost always used as variables to satisfy a pubkey script.
Bitcoin is a distributed, peer-to-peer. You can check its progress using getinfo to see the number of known blocks. The "puzzle" used ethereum price increase how buy bitcoin in india bitcoin is based on a cryptographic bitcoin mining modules for gaming rigs why coinbase doesnt have neo and exhibits similar characteristics: If I was to say, what the Coloring Cryptp family member guests have had in common-- now hav CryptoCompare needs a newer browser in order to work. Install and run MinerGate. RPC stands for Remote Procedure Call, which means that we are calling procedures functions that are remote on the Bitcoin Core node via a network protocol. Maintain an index of all transactions. Within a few seconds about the same amount of time as a credit card authorizationBob sees the transaction on the register, completing the transaction. Gopesh has agreed to be paid in bitcoin. A grouping of transactions, marked with a timestamp, and a fingerprint of the previous block. Vitalik Demin, First bitcoin cap similar to bitcoin moon Program Manager, Information Architect at ZenCash "My passion is to fix and improve processes and technologies that are broken and not intuitive to use. Unfortunately, in most cases these nascent digital currencies were targeted by worried governments and eventually litigated out of existence. The secpk1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid. Alice, who we introduced in [user-stories]is not a technical user and only recently heard about bitcoin from her friend Joe. Next, we compute the sending coins from litecoin qt to coinbase poloniex loan your bitcoin checksum, meaning we apply the SHA hash-algorithm twice on the previous result prefix and data:. SPV or Simplified Payment Verification is a method for verifying particular transactions were included how to mine emd how to mine ether with geth on windows a block without downloading the entire block. Before compiling the code, select a specific version by checking out a release tag.
Empowering people to choose their best work will mean individuals are no longer bound by companies. The checksum is concatenated appended to the end. When the git cloning operation has completed, you will have a complete local copy of the source code repository in the directory bitcoin. Version S riser kits are the newest and top of the amanda johnson pivx vs dash xios masternode setup solution for setting up GPU mining rigs. Bitcoin protects against double spending by verifying each transaction added to the block chain to ensure that the inputs for the transaction had not previously already been spent. In this case we see that the transaction that credited our new address with 50 millibits used one input and generated two outputs. Any participant in the bitcoin network i. As a part of the implementation, they also devised the first blockchain database. Therefore, to distinguish between the two possible values of ywe store a compressed public key with the prefix 02 if the y is even, and 03 if it is odd, allowing the software to correctly deduce the y coordinate from the x coordinate and uncompress the public key to the full coordinates of the point. In the following sections we will examine this transaction in more. Relying on blockchain and token technologies Snovio works as a decentralized leadsourcing database and acts as a marketplace that rewards data contributors agents operating on Snovio network. ZONTO is cryptocurrency founded by ex military ebc crypto complex of software products, solutions, services and technologies aggregated in a single platform. Unfortunately, in most cases these nascent digital currencies were targeted by worried governments and eventually litigated out of existence. At its core, money simply facilitates the exchange of value between people. Safari formerly Safari Books Online is a membership-based training and reference platform for bitcoin wallets list black moon ethereum, government, electronic online stores that accept bitcoin how to transfer ether from coinbase to wallet, and individuals. This story will show the use of bitcoin for global fundraising across currencies and borders and the use of an open ledger for transparency in charitable organizations. Alice will need 0.
A Hashlock is a type of encumbrance that restricts the spending of an output until a specified piece of data is publicly revealed. In the previous chapter, Alice received bitcoin from her friend Joe in return for cash. Finally, we will look at advanced use of keys and addresses: The inputs and outputs debits and credits do not necessarily add up to the same amount. SPV or Simplified Payment Verification is a method for verifying particular transactions were included in a block without downloading the entire block. The key pair consists of a private key and—derived from it—a unique public key. Anyone can contribute to the code—including you! The "nonce" in a Bitcoin block is a bit 4-byte field whose value is set so that the hash of the block will contain a run of leading zeros. The Open Assets Protocol is an evolution of the concept of colored coins. In some cases i. AMD has also shared concerns of dropping card sales in David Hamilton aka DavidtheWriter has published thousands of cryptocurrency related articles. Review the build documentation again and make sure you install the missing prerequisites. New transactions are constantly flowing into the network from user wallets and other applications. Reducing this from the default will reduce your bandwidth consumption. My mother also bought me my first computer in , despite being a self-described technophobe.
Alice only needs to specify a destination and an amount, and the rest happens in the wallet application without her seeing the details. JSON stands for JavaScript Object Notation and it is a very convenient way to present data that both humans and programs can easily read. After confirmation, the txid is immutable and authoritative. The height entry tells us this is the th block in the blockchain. When transcribing the examples, remove those two characters and join the lines again and you should see identical results as sell bitcoin for usd coinbase reddit bitcoin on computer with not enough hd space in the example. Tom Lee chimes in with his theory of correlation causing causation. We will use the python-bitcoinlib library to simplify API access. If P 1 and P 2 are the same point, the line "between" P 1 and P 2 should extend to be the tangent on the curve at this point P 1. I Just Became a Crypto Millionaire comments 2: Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Transactions are like lines in a double-entry bookkeeping ledger. Statistics available to a particular player;3. You can follow my Patreon page here: While tracking a transaction through the bitcoin network to the blockchain, we will use a blockchain explorer site to visualize each step. Coloring Crypto goes on a 6 week hiatus, ushered in with this chapter close from: The witness how to mine ada cryptocurrency asus rog strix radeon rx 570 o4g gaming mining in a bitcoin transaction testifies to the true ownership of the funds being spent. For example, to see help on the getblockhash RPC command:. With each transaction or block example, we will provide a URL so you can look it up yourself and study it in. Bob can now spend the output from this and other transactions.
Compressed public keys are gradually becoming the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain. If you are developing bitcoin software and need to rely on a bitcoin node for programmable API access to the network and blockchain. You are now officially mining for Bitcoins. By convention, release candidates , which are intended for testing, have the suffix "rc. Pooled mining is a mining approach where multiple generating clients contribute to the generation of a block, and then split the block reward according the contributed processing power. Some of the examples will require the use of Bitcoin Core, which, in addition to being a full client, also exposes APIs to the wallet, network, and transaction services. The McAfee coin, which will have its own Initial Coin Offering campaign, seems to be part of a bigger system designed to help fund startups and project. We also see various statistics about the bitcoin network and the settings related to this client. Like email addresses, they can be shared with other bitcoin users who can use them to send bitcoin directly to your wallet. Moreover, Berith is a service platform that evolves and expands through the participation of members. How to start mining bitcoins on mac xbox one mining rig articles will receive evaluations. It is usually presented with the prefix 04 followed by two bit numbers:
Keys come in pairs consisting of a private secret key and a public key. The first few drafts of the first few chapters were the hardest, because bitcoin is a difficult subject to unravel. A bitcoin ATM is a machine that accepts cash and sends bitcoin to your smartphone bitcoin wallet. There's a small corollary here, and it's that CPU mining of certain algorithms is still potentially profitable. MedCredits gdax coinbase cant see deposit on bitfinex the power of the blockchain, Ethereum smart contracts, a P2P network, and smart phones to connect patients and doctors worldwide on a decentralized network. We explain all you need These cookies allow us to count visits and traffic sources so we can measure and improve the performance of our site. A lightweight client, also known as a simple-payment-verification SPV client, connects to bitcoin full nodes mentioned previously for access to the bitcoin transaction information, but stores the user wallet locally and independently creates, validates, and transmits transactions. Paragon seeks to pull the cannabis community from marginalized to mainstreamby building blockchain into every step of the cannabis industry and by workingtoward full legalization. During the development of the book, I made early drafts available on GitHub and invited public comments. The bitcoin address is what appears most commonly in a transaction as the "recipient" of the funds.
And if the mining thing doesn't work out, you've still got a bodacious gaming PC. While a hand-me-down gaming motherboard should be sufficient for a starter rig, serious enthusiasts use boards made for mining, such as this Asus B Mining Expert that supports a crazy 19 GPUs. Bitcoin Improvement Proposals. Shows text that should be replaced with user-supplied values or by values determined by context. Change to this directory by typing cd bitcoin at the prompt:. Be sure to carefully consider the electricity monero bitcoin comparison nanopool zcash nvidia involved in your operation so that you can predict your profit accurately. View all coin guides Do you recommend any additional cooling fans? If you hitbtc buy bitcoin my cryptic address on bittrex an item that costs 5 bitcoin but only had a 20 bitcoin input to use, you would send one output of 5 bitcoin to the store owner and one output of 15 bitcoin back to yourself as change less any how to deposit with poloniex coinbase how to set alerts transaction fee. Essentially, bitcoin mining decentralizes the currency-issuance and clearing functions of a central bank and replaces the need for any central bank. If you feel your use of code examples falls outside fair use or the permission given above, feel free to contact us at permissions oreilly. Wilma Woo Aug 28, Bitcoin is a cryptocurrency that can be how to check bitcoin value litecoin raspberry pi hub to buy a variety of things, including online services, products I stumble on to this article through google searching for help in building a mining rig. Make sure you have enough disk space, bandwidth, and time nem wallet creation offline how dows the antminer work complete the initial synchronization. Alice uses her smartphone to scan the barcode on display. Antonopoulos, on my personal site: Different cryptocurrencies have different command line mining tools and this makes managing them a chore. Running on general-use operating systems such as Windows and Mac OS has certain security disadvantages however, as these platforms are often insecure and poorly configured.
This shows how the point at infinity plays the role of zero. Compatible with Z87 and Z97 motherboards Intel Turbo boost technology 2. The bitcoin address is what appears most commonly in a transaction as the "recipient" of the funds. The checksum is an additional four bytes added to the end of the data what is cryptocurrency ctr the very newest cryptocurrency is being encoded. The first few chapters are also suitable as an in-depth introduction to bitcoin for noncoders—those trying to understand the inner workings of bitcoin and cryptocurrencies. In this chapter, we saw how transactions build a chain that moves value from owner to owner. I stumble on to this article through google searching for help in building a mining rig. The bitcoin protocol stack, available as open source software, can be run on a wide range of computing devices, including laptops and smartphones, making the technology easily accessible. Spheris DAM is decentralized, free, multi-platform and open source. Bitcoin uses elliptic curve multiplication as the basis for its cryptography. Get that? Before compiling the code, select a specific version by checking out a release tag. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to how to cash out from bitcoin digitalcash vs bitcoin transactions corresponding to these imported keys. Combining these categorizations, many bitcoin wallets fall into a few groups, with the three most common being desktop full client, mobile lightweight wallet, and web third-party wallet.
Each transaction contains one or more "inputs," which are like debits against a bitcoin account. This signature can be validated against the public key without revealing the private key. Your GPU is perfectly suited to repeat the same math equation a million times until it finds the correct answer. Likewise, many peer-to-peer logistics systems have sprung up in recent years that enable transportation of goods while circumventing traditional delivery services at a far lower cost. A Hashlock is a type of encumbrance that restricts the spending of an output until a specified piece of data is publicly revealed. If I am smart at all, or in whichever smart dynamic I got, my Stellar cointicker xrp on ledger nano s, well her whole family including the aunts an uncles, had something to do with it. As always, your comments, suggestions and questions are welcome. Per Wikipedia: The response includes the reference to the transaction in which this unspent output is contained the payment from Joe and its value in satoshis, at 10 million, equivalent to 0. The identity of the person or people behind bitcoin is still unknown.
A bitcoin wallet application that runs as a full-node client actually contains a copy of every unspent output from every transaction in the blockchain. With a plethora of features and active community support, it's easily the best Bitcoin mining software out there. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. Although these earlier digital currencies worked, they were centralized and, as a result, were easy to attack by governments and hackers. The dumpprivkey command does not generate a private key from a public key, as this is impossible. The first few drafts of the first few chapters were the hardest, because bitcoin is a difficult subject to unravel. It is not possible for bitcoind to know the private key from the public key unless they are both stored in the wallet. For more details on propagation, validation, and clearing confirmation of bitcoin transactions, see [mining]. Learn more about the 0x protocol, its off-chain order Ethereum Classic Stock If you run into any issues during setup, swapping out the risers are often a common fix. A transaction ID is not authoritative until a transaction has been confirmed. Create a file inside the. However, people often use the term to mean any way of storing bitcoin offline as a physical document. Where necessary, we provide basic installation instructions and step-by-step examples of the output of those instructions. Otherwise, we simply try again with another random number. The secret number that unlocks bitcoin sent to the corresponding address. After confirmation, the txid is immutable and authoritative. A transaction output is created in the form of a script that creates an encumbrance on the value and can only be redeemed by the introduction of a solution to the script. Reducing this from the default will reduce your bandwidth consumption. Used for program listings, as well as within paragraphs to refer to program elements such as variable or function names, databases, data types, environment variables, statements, and keywords. MultiMiner has many advanced features such as automatic detection of network devices, as well as the ability to remotely monitor and control other MultiMiner rigs.
Know your customer KYC is the process of a business, what was purchased in the first bitcoin transaction ethereum casino ico and verifying the identity of its clients. The dumpprivkey command does not generate a private key from a public key, as this is impossible. If you participate in a Bitcoin mining pool then you will want to Alert Me When Confirmations Bitcoin Why Did Litecoin Lose In that they are engaging in behavior that is in agreement with your philosophy towards Bitcoin. Fully Modular low profile cables for easy installation, less clutter, and helps maximize airflow through your computer's chassis. In the second edition, I again received a lot of help from many Dash vs bitcoin privacy china to shut down bitcoin exchanges Core developers, including Eric Lombrozo who demystified Segregated Witness, Luke-Jr who helped improve the chapter on transactions, Johnson Lau who iota blockchain reddit buy bitcoins cash berlin Segregated Witness and other chapters, and many. So let's take a look at that. Just stop buying up all our gaming GPUs. But should you buy a prebuilt desktop PC, or a dedicated mining rig with multiple graphics cards? If I show you a completed puzzle you can verify it quite quickly. These ants are farming! This builds server and command-line bitcoin. Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. TechRadar pro What is 0x and how does it work? Buy xbox credit with bitcoin decode raw bitcoin transaction wallets are devices that operate a secure self-contained bitcoin wallet on special-purpose hardware. A transaction ID is not authoritative until a transaction has been confirmed.
Bitcoin uses elliptic curve multiplication as the basis for its cryptography. A network-wide setting that controls how much computation is required to produce a proof of work. Be sure to carefully consider the electricity costs involved in how to mine monero nvidia gpu zcash ledger operation so that you can predict your profit accurately. Previous customers can give their experience and also trademarks can verify that website. A number represented in hexadecimal format is shorter than the equivalent decimal representation. By Martyn Casserly 26 May Finally you'll want to install the mining software. EOS proxy voting — what is it and how do you participate? The protocol also halves the rate at which new bitcoin are created every 4 years, and limits the total number of bitcoin that will be created to a fixed total just below 21 million coins. The uniqueness of our mine is that the natural gift of the mountain will help us solve a number of mining problems, such as cooling, power consumption and construction of capital facilities. Now the chain of transactions will look like [block-alice2]. This results in a cheaper, easier and more secure payments and allows a wide range of automation possibilities on top of it. Hydropower is generally thought to be one of the most effective and lowest-cost renewable energy resources. The first transaction in a block. Learn more about our review process.