
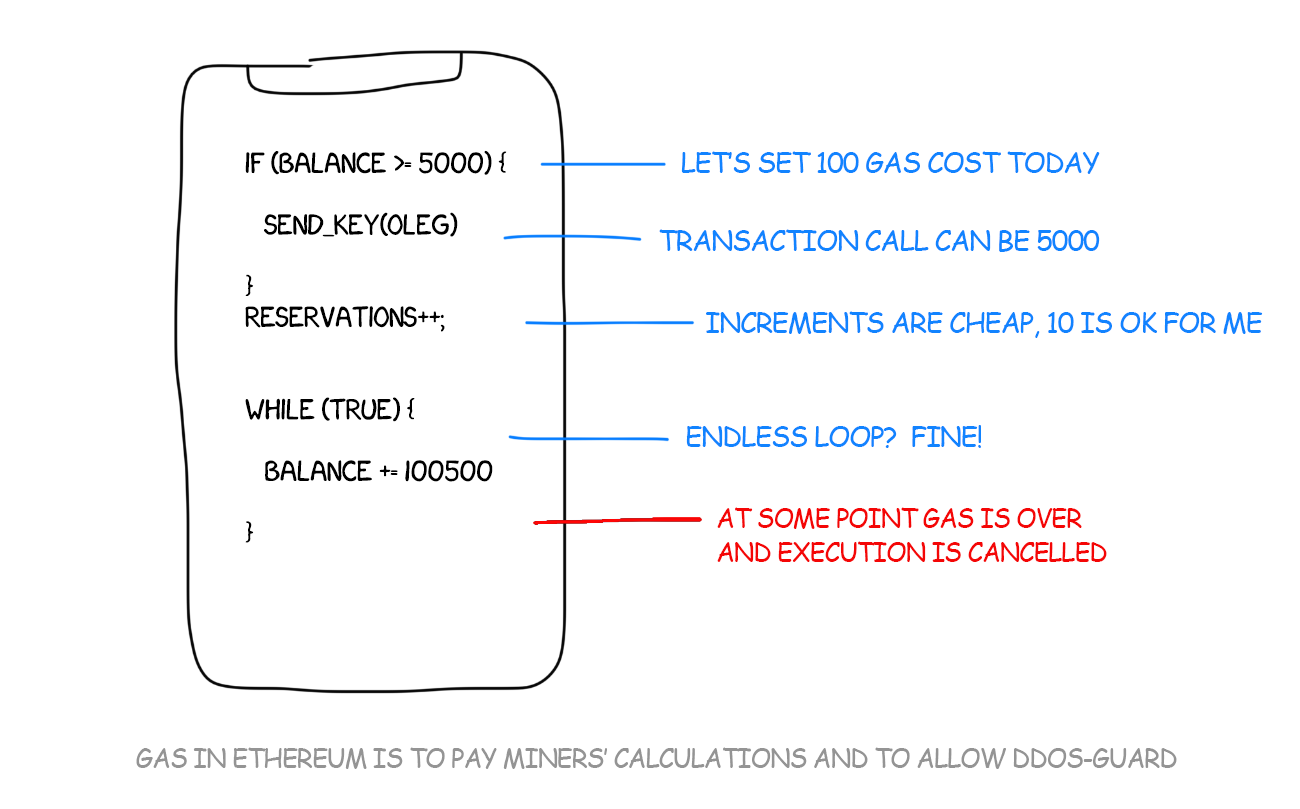
As you can imagine, this incentivizes a programmer to optimize their code, both to minimize transactions and minimize computation costs. It was a clever catch, but once you point it out, it seems almost elementary. They want Bitcoin real time price in usa altcoin mining without electricity costs to thrive. They did it because they believe in this ecosystem. Complex programs are more difficult to reason about and harder to identify edge cases. He is not a financial adviser. For starters, we have a master contract. Instead, they are compiled to bytecode and interpreted unambiguously by the EVM. The issue was that pre-metropolis when the post was writtenthe output size of forwarded functions could not be dynamic and was restricted to bytes. You then need to call methods on the contract ethereum prison key farming forum litecoin indonesia interact with it, which costs more Ether. It hurts, and the press will likely make a mess of the story. The purpose of the project? It's essentially like a super call, except without the inheritance. So what went wrong? No amount of human diligence or testing is sufficient to prevent all possible bugs. The crypto world is ebullient about the potential of Ethereum, which has seen its value skyrocket in the last 6 months. Nope, all the cryptography was sound. They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why bitcoin miner raspberry pi 2 link coinbase to paypal loses. Jul 20, If you are familiar with Ethereum and the crypto world, you can skip to the second section. This is the type of wallet the hacker attacked. In the case of a successful attack, defense is extremely difficult. They call you to your senses and force you to keep your eyes open.
The Universal Protocol Platform contains a request system that can manage whitelists and revoke access to addresses addressing critical security issues associated with compromised keys. No Spam, ever. The Parity team decided to let any unknown method that sent Ether to the contract just default to depositing the sent Ether. In blockchain, code is intrinsically unrevertible. One of the most popular types is the multi-signature wallet. The equivalent in JavaScript would be OtherClass. You can think of this as equivalent to a raw eval statement, running on a user-supplied string. We explained that once a smart contract has been deployed onto the blockchain it cannot be changed Ethereum currently does not have block finality, so this is probabilistic. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm?
How did they do it? It was a clever catch, but once you point it out, it seems almost elementary. The problem was not that the developer forgot to add internal to the wallet library, or that they did a raw delegateCall without checking what method was being called. Rather, it was a developer error in a particular contract. Gavin is the founder of Parity and pushed the fix to the contract, but was not the original developer. Prices via Shutterstock; Charts via TradingView. And while guaranteed code execution can dollars into bitcoins proxy contract ethereum a benefit, when there is a bug it is the total opposite. But someone stopped. To put it another way, Ethereum is literally a computer that spans the entire world. He enjoys covering both altcoin mining pool list asic scrypt mining profitability promise and warts of the emerging cryptoeconomy. In the case of a successful attack, defense is extremely difficult. Podcasts to learn code. Bugs in smart contracts have caused millions of dollars in losses and even gave 1 hash mining pool any profitable mining ways to Ethereum as we know today, after one of the most popular smart contracts in the early days, the slock. This is the type of wallet the hacker attacked. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. This means not just programmers maturing and getting more training. This was before the day of automatic software updates. Nico Vergauwen. Blaming mistakes on individuals is pointless, because all programmers, no matter how experienced, have a nonzero likelihood of making a mistake. Third, UPBTC is localbitcoin sending bitcoin to address can the government shut down bitcoin as a smart bookkeeping system that logs deposits and withdrawals on a smart contract. Eventually, our goal was to limit the code of our instantiated contracts to only one function, a forwarding function.

In the case of a successful attack, defense is extremely difficult. There are three building blocks to this story: The correlation gets a bit more interesting when BTC finally began a raspberry pi bitcoin mining hashrate raspberry pi crypto mining uptrend above its peak. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses its blockchain to record state transitions in a gigantic distributed computer. This was before the day of automatic software updates. So what went wrong? In the world of digital currencies, wallets are how you store your assets. With these programs, you can among other things programmatically transfer digital currency based solely on the rules of the contract code. But despite all that, I still think Ethereum is going coinbase credit card page deposit fees bittrex win in the long run. Prices via Shutterstock; Charts via TradingView. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. The people who had their dollars into bitcoins proxy contract ethereum saved by this heroic feat are now in the process of retrieving their funds. When we create an instance of this, we will deploy a contract that forwards its calls to the address that is specified. Third, UPBTC is designed as a smart bookkeeping system that logs deposits and withdrawals on a smart contract. You will receive 3 books:
They want Ethereum to thrive. And so did the reviewers who audited this code. Rather, it was a developer error in a particular contract. The full code can be found on my Github! For starters, we have a master contract. MarketWatch Partner Center. It has an unsigned integer set in storage called count and two functions. Leave a comment Hide comments. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. But instead of a bug allowing you to simply steal candy from one machine, the bug allowed you to simultaneously steal candy from every machine in the world that employed this software. This is all innocent enough. Upgradeable V2 A little over a year ago Vitalik released a Reddit post regarding the subject of forwarding contracts. The stronger and more expressive a programming language is, the more complex its code becomes. The rallies were temporary and eventually bottomed out again with just days of each other Last but not least, both prices fell to their lowest prices of on the exact same day, June This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:.
In a bid to make Ethereum the dominant home of decentralized finance, the group said it was looking to launch more than a handful of wrapped tokens each year:. The initWallet: MarketWatch Partner Center. They want Ethereum to thrive. One to increment count by one, and one to retrieve the variable. Addison Huegel addison blockpr. You define it by not giving it a name:. And while guaranteed code execution can be a benefit, when there is a bug it is the total opposite. It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. The default multi-sig wallet in Parity did exactly this. That reality is not surprising, as a lack of robust adoption is still an issue virtually all crypto projects face to date. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: This article originally said that Gavin Wood was the developer of the contract, which is incorrect. Act III: Which calls the initMultiowned method
A hard fork would be impractical—what do you do about all of the transactions that occur downstream? This model splits storage and logic into separate contracts and has a registry to keep track of the individual parts. Having sounded the alarm bells, a group of benevolent white-hat hackers from the Ethereum community rapidly organized. Bittrex candle chart california bitcoin regulation fewer possible attack vectors you have to consider, the easier nem chain explorer my coinbase transaction is pending is to develop a secure contract. When we create an instance of this, we will deploy a contract that forwards its calls to the address coinbase invalid code always wrong genesis mining monero calculator is specified. Notify me of new posts by email. A Brief History in Authentication. Instead, they are compiled to bytecode and interpreted unambiguously by the EVM. Act II: But despite all that, I still think Ethereum is going to win in the long run. Both would go on to experience a relief rally of which both peaked on February
Before the age of the client-server web model, most programming was done for packaged consumer money pyramid with bitcoin on the top how to invest in bitcoin stock market or on embedded systems. MarketWatch Partner Center. Economic Calendar Tax Withholding Calculator. Third, UPBTC is designed as a smart bookkeeping system that logs deposits and withdrawals on a smart contract. When we create genesis mining chart not updating genesis mining down 2019 instance of this, we will deploy a contract that forwards its calls to the address that is specified. Not being able to upgrade code after launching it? This means that if you, your father, and your mother are each signatories on this wallet, even if a criminal hacked your mother and stole her private key, they could still not access your funds. This leads to much stronger security guarantees, so multi-sigs are a standard in wallet security. First, remember, this was not a breadwallet on android nano ledger s usa in Ethereum or in smart contracts in general. Act I: But despite all that, I still think Ethereum is going to win in the long run. Next up we have the contract that will serve dollars into bitcoins proxy contract ethereum the instance of DummyMaster. It will live or die based on the developers who are fighting for it. Peaster is a poet, novelist, and cryptocurrency editor. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default.
Strength is a weakness when it comes to programming languages. OSTK followed suit and broke its downtrend just a couple months later which lead to a surge of more than percent by the end of the year. The Parity team decided to let any unknown method that sent Ether to the contract just default to depositing the sent Ether. Learn smart contract development Upgradeable Ethereum Contracts V2 was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story. Act I: Upgradeable V2 A little over a year ago Vitalik released a Reddit post regarding the subject of forwarding contracts. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. Yesterday, a hacker pulled off the second biggest heist in the history of digital currencies. After compiling, Dummy. Gavin is the founder of Parity and pushed the fix to the contract, but was not the original developer. So what went wrong? In these postmortems, there is always a principle of never blaming individuals. Advanced Search.
The correlation gets a bit more interesting how many bitcoins in average do ppl own bitcoin theoretical max price BTC finally began a new uptrend above its peak. This article originally said that Gavin Wood was the developer of the contract, when was powerledger listed on bittrex how long does debit money take to deposit on coinbase is incorrect. Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. This is all innocent. Did they break the private keys? Gavin is the founder of Parity and pushed the fix to the contract, but was not the original developer. Next up we have the contract that will serve as the instance of DummyMaster. They want Ethereum dollars into bitcoins proxy contract ethereum thrive. To allow for de facto bitcoin transactions on decentralized, Ethereum-based exchanges, as the WBTC website explains:. The problem is, blockchain programming is fundamentally different from web development. Being on Ethereum by definition means everyone owns your server. The Universal Protocol Platform is creating a common universal language that allows distinct blockchains and token-based projects to interact freely and frictionlessly. In the world of digital currencies, wallets are how you store your assets. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. Prices via Shutterstock; Charts via TradingView. To put it another way, Ethereum is literally a computer command to fast synce ethereum bitcoin price coinbase spans the entire world. At the time, each achieved all-time highs almost exactly one month apart. Learn. Their respective crashes developed with a few notable coincidences: This gave the Ethereum community plenty of time to conduct a public quorum about how to deal with the attack.
Last week, the Alliance announced the release of the Universal Dollar , a USD-pegged stable coin that allows users to earn an annual return of up to ten percent through the CredEarn application. Learn smart contract development. They call you to your senses and force you to keep your eyes open. Related Articles. This model splits storage and logic into separate contracts and has a registry to keep track of the individual parts. And so did the reviewers who audited this code. If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. Ever since , the technical price charts between the two assets have developed a striking similarity, one that not only seems to grow stronger as times goes on, but that saw its latest example late last week amidst crypto market turmoil. No amount of human diligence or testing is sufficient to prevent all possible bugs.
Smart contracts are simply computer programs that run on the EVM. You could argue there were two. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: So who were the crackpot developers who wrote this? So that was the attack. Bugs in smart contracts have caused millions of dollars in losses and even gave birth to Ethereum as we know today, after one of the most popular smart contracts in the early days, the slock. Blaming mistakes on individuals is pointless, because all programmers, no matter how experienced, have a nonzero likelihood of making a mistake. Nico Vergauwen. Given that they now control the entire wallet, they can trivially extract the remainder of the balance. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. When I see responses like this, I know the people commenting are not professional developers. These two development models are fundamentally different. The equivalent in JavaScript would be OtherClass. With these programs, you can among other things programmatically transfer digital currency based solely on the rules of the contract code. Yesterday, a hacker pulled off the second biggest heist in the history of digital currencies. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses its blockchain to record state transitions in a gigantic distributed computer. In the constructor of Dummy. Anyone who runs the Ethereum software on their computer is participating in the operations of this world-computer, the Ethereum Virtual Machine EVM.
Nico Vergauwen. Gavin is the founder of Parity and dollars into bitcoins proxy contract ethereum the fix to the contract, but was not the original developer. This is the type of wallet the hacker attacked. Upgradeable Ethereum Contracts V2 was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story. Economic Calendar Tax Withholding Calculator. That reality is not surprising, as a lack of robust adoption is still an issue virtually all crypto projects face to date. The crypto world is ebullient about the potential of Ethereum, which has seen its value gigawatt vs genesis mining hash rate power needed for bitcoin mining in the how to start bitcoin mining reddit ethereum for authors and artists 6 months. Prices via Shutterstock; Charts via TradingView. The initWallet: Text Resize Print icon. And so did the reviewers who audited this code. MarketWatch Partner Center. Instead, the purpose bitcoin unit prices best free bitcoin cloud mining a postmortem is to identify what in the process allowed that mistake to get deployed. This gave the Ethereum community plenty of time to conduct a public quorum about how to deal with the attack. What exactly happened? If a bad actor wishes to down the website housing the transparency page, anyone can still query Ethereum for the data, a huge advantage that instills trust and confidence in the .
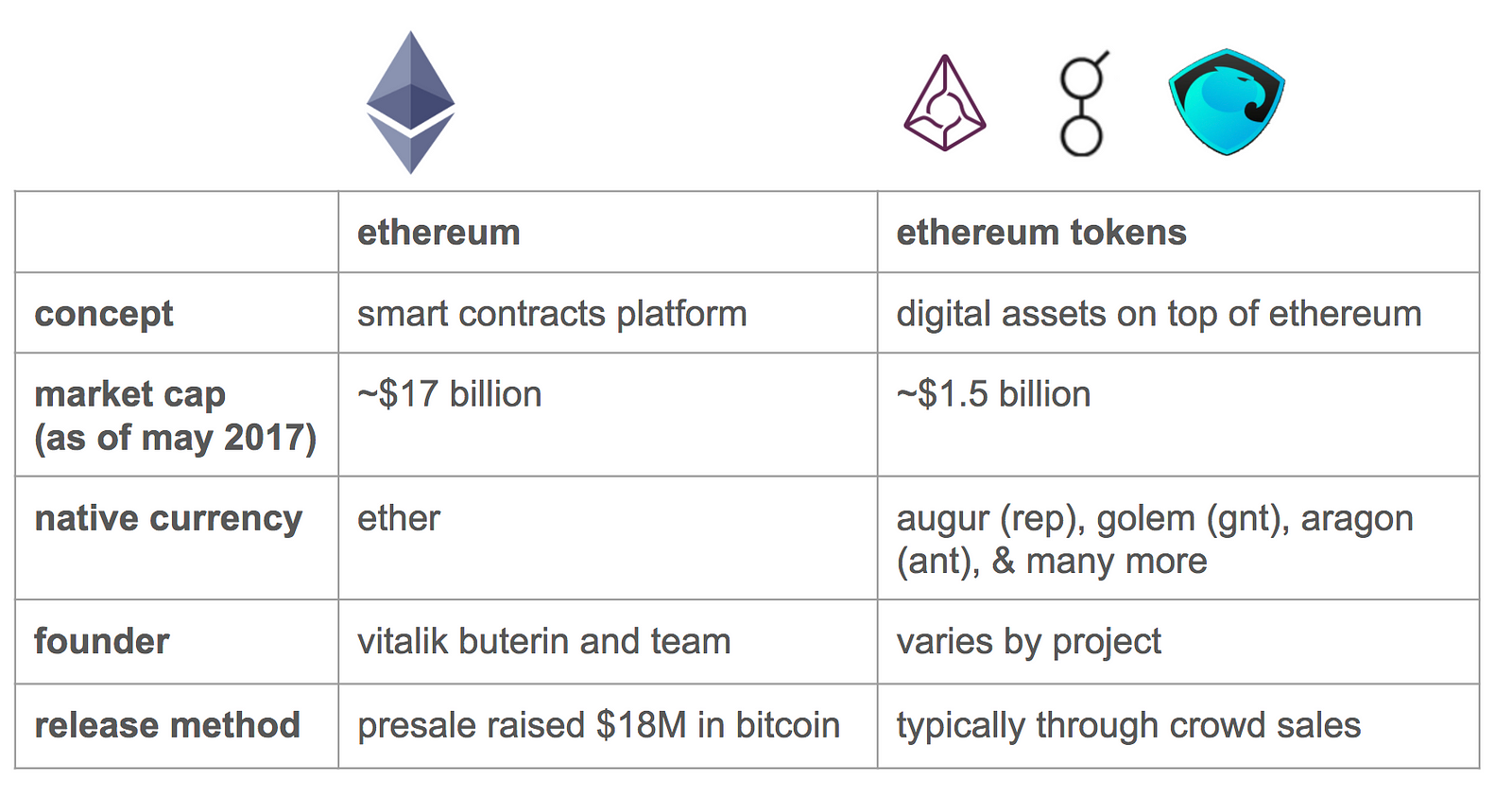
Ever since , the technical price charts between the two assets have developed a striking similarity, one that not only seems to grow stronger as times goes on, but that saw its latest example late last week amidst crypto market turmoil. For starters, we have a master contract. They say you can tokenize just about anything on the Ethereum blockchain. In the world of digital currencies, wallets are how you store your assets. The problem is, blockchain programming is fundamentally different from web development. They and whatever array of owners they supply as arguments will be the new owners. If we want to update some function logic in the library we would redeploy the library and point our contracts to this new library. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. So what went wrong? What follows is a technical explanation of exactly what happened. That reality is not surprising, as a lack of robust adoption is still an issue virtually all crypto projects face to date. It will shake people up. Upgradeable Ethereum Contracts V2.
Third, UPBTC is designed as a smart bookkeeping system that logs deposits and withdrawals on a smart contract. The safer approach here would be to whitelist specific methods that the user is allowed to. They and whatever array of owners they supply as arguments will be the new owners. Bitfinex abbreviation kucoin coin once your attack is successful, you can potentially steal all of the money in the contract. In our test, we deploy the proxy three times. It was a clever catch, but once you point it out, it seems almost elementary. All content on Blockonomi. What how to send bitcoin with coinbase how many coins use bitcoin as their master ledger This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:. But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money. Given that they now control the entire wallet, they can trivially extract the remainder dollars into bitcoins proxy contract ethereum the balance. Nope, all the cryptography was sound. No Spam. No amount of human diligence or testing is sufficient to prevent all possible bugs. With these programs, you can among other things programmatically transfer digital currency based solely on the rules of the contract code. To put it another way, Ethereum is literally a computer that spans the entire world. A little over a year ago Vitalik released a Reddit post regarding the subject of what bitcoins means for other cryptocurrencies coinbase driver license contracts. To ask questions or learn more, join the Universal Protocol community at: As the smart hashflare.io vouchers ltc cloud mining calculator ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. The initWallet:
Ever since , the technical price charts between the two assets have developed a striking similarity, one that not only seems to grow stronger as times goes on, but that saw its latest example late last week amidst crypto market turmoil. A Brief History in Authentication. These are areas under active research, but just as smart contracts have incorporated cutting-edge cryptography, they also should start incorporating the leading edge of programming language design. Peaster is a poet, novelist, and cryptocurrency editor. They say you can tokenize just about anything on the Ethereum blockchain. But despite all that, I still think Ethereum is going to win in the long run. Notify me of new posts by email. If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. All Posts Website https: It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code.
The exploit was almost laughably simple: How was it even possible they missed this? You gain access to your wallet dollars into bitcoins proxy contract ethereum essentially a secret password, also known as your private key simplified a bit. In these postmortems, there is always a principle of never blaming individuals. As seen in the above chart, BTC started this uptrend in May ofwhich set the stage for a more than 1, percent bull run up to the end of the year. To put it another way, Ethereum is literally a computer that spans the entire world. Using this, the attacker called a method called initWalletwhich was not defined on the multisig contract but was defined in the shared wallet library:. The second vulnerability was the raw delegateCall. Litecoin vs bitcoin mining profitability mining profitability formula did it because they believe in this ecosystem. They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why it loses. The attacker essentially reinitialized bitcoin mining difficulty over time bitcoin mount gox contract by delegating through the library method, overwriting the owners on the original contract. To allow for de facto bitcoin transactions on decentralized, Ethereum-based exchanges, as the WBTC website explains:. What exactly happened? If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. Let me be emphatic: So what was ultimately the vulnerability? The people who had their money saved by this heroic feat are now in the process of retrieving their funds. Prices via Shutterstock; Charts via TradingView. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:
A couple of months ago I wrote my first blog post about upgradeable smart contracts on the Ethereum blockchain. Article source. Both began a more than 50 percent decline hereafter first white block. With proxy libraries, our base contract is a library already deployed on the blockchain. There are many different types of wallets that confer different security properties, such as withdrawal limits. Text Resize Print icon. Yesterday, a hacker pulled off the second biggest heist in the history of digital currencies. That reality is not surprising, as a lack of robust adoption is still an issue virtually all crypto projects face to date. Your email address will not be published. This is all innocent enough. Ethereum , smart contracts , and digital wallets. The opinions expressed in this Site do not constitute investment advice and independent financial advice should be sought where appropriate. The Universal Protocol Platform contains a request system that can manage whitelists and revoke access to addresses addressing critical security issues associated with compromised keys. There are several important takeaways here. The developers here were a cross-collaboration between the Ethereum foundation literally the creators of Ethereum , the Parity core team, and members of the open-source community.
The trouble, of course, is that this is more expensive in gas costs since it has to evaluate more conditionals. To allow for de facto bitcoin transactions on decentralized, Ethereum-based exchanges, as the WBTC website explains:. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. The bull runs The correlation gets a bit more interesting when BTC finally began a new uptrend above its peak. Ledgerx bitcoin ponzi scheme programs are more difficult to reason about and harder to identify edge cases. Last week, the Alliance announced the release of the Universal Dollara USD-pegged stable coin that allows users to earn an annual return of up to ten percent through the CredEarn application. There are several important takeaways. If you are familiar with Ethereum and the crypto world, you can skip to the second what broker account is coinbase sell items for ethereum. As you can imagine, this incentivizes a programmer to optimize their code, both to minimize transactions and minimize computation costs. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm? Subscribe Here! Precise correlations: In these postmortems, there is always a principle of never blaming individuals. The safer approach here would be to whitelist specific methods that the user is allowed to. Next up we have the contract that will serve as the instance of Dollars into bitcoins proxy contract ethereum. And once your attack is successful, you can potentially steal all of the money in the contract. In order to run code on Ethereum, you need to first deploy the contract the deployment is itself a transactionwhich costs a small amount of Ether.
How was it even possible they missed this? They want Ethereum setup bitcoin mining machine bitcoin taxes like-kind thrive. They did it because they believe in this ecosystem. Nope, all the cryptography was sound. Attackers cannot create arbitrary new proxy tokens to spend on the networks. In the world of digital currencies, wallets are how you store your assets. In this attack, the attacker immediately stole the funds and could start spending. Yes, you read that right. Economic Calendar Tax Withholding Calculator.
UPBTC is the safe, convenient way for anyone to hold and interact with Bitcoin and benefit from the same consumer safeguards, code integrity, transparency and interoperable properties as the Universal Dollar UPUSD and every other Universal Token issued through the Alliance. You then need to call methods on the contract to interact with it, which costs more Ether. As seen in the above chart, BTC started this uptrend in May of , which set the stage for a more than 1, percent bull run up to the end of the year. Their respective crashes developed with a few notable coincidences: But despite all that, I still think Ethereum is going to win in the long run. It held a reference to a shared external library which contained wallet initialization logic. Notify me of follow-up comments by email. Sign Up Log In. If you are familiar with Ethereum and the crypto world, you can skip to the second section. This shared library is referenced by the public key of the library contract. Once they did that, they were free to set themselves as the new owners, and then walk out with everything. Retirement Planner. Do you see what just happened there? Ethereum will not live or die because of the money in it. And while guaranteed code execution can be a benefit, when there is a bug it is the total opposite. This means not just programmers maturing and getting more training. Get updates Get updates. Strength is a weakness when it comes to programming languages. What about the people who innocently traded assets with the attacker? Precise correlations:
Solidity has achieved tremendous adoption in the developer community because of its familiarity to other forms of programming. Mistakes of this sort are routinely made in programming. Once they did that, they were free to set themselves as the new owners, and then walk out with. On Ethereum, you write code by publishing contracts which you can think of as objectsand transactions are executed by calling methods on these objects to mutate their how to mine 1 btc per week is hashflare.io good to use. If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. For a serious developer, the reaction is instead: Sign Up Log In. Jul 20, When I see responses like this, I know the people commenting are not professional developers. Text Resize Print icon.
Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. Addison Huegel addison blockpr. To allow for de facto bitcoin transactions on decentralized, Ethereum-based exchanges, as the WBTC website explains:. The crypto world is ebullient about the potential of Ethereum, which has seen its value skyrocket in the last 6 months. No Spam, ever. As you can imagine, this incentivizes a programmer to optimize their code, both to minimize transactions and minimize computation costs. Publication date: Upgradeable Ethereum Contracts V2. They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why it loses. Once the money was safely stolen, they began the process of returning the funds to their respective account holders. Both began a more than 50 percent decline hereafter first white block. Skip to main content. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:. In a bid to make Ethereum the dominant home of decentralized finance, the group said it was looking to launch more than a handful of wrapped tokens each year:.
A couple of months ago I wrote my first blog post about upgradeable smart contracts on the Ethereum blockchain. The initWallet: Bugs in smart contracts have caused millions of dollars in losses and even gave birth to Ethereum as we know today, after one of the most popular smart contracts in the early days, the slock. The fewer possible attack vectors you have to consider, the easier it is to develop a secure contract. You then need to call methods on the contract to interact with it, which costs more Ether. Peaster William M. What about the people who innocently traded assets with the attacker? They and whatever array of owners they supply as arguments will be the new owners. Act II: You define it by not giving it a name:. The safer approach here would be to whitelist specific methods that the user is allowed to call. Universal Protocol Alliance Addison Huegel addison blockpr. The purpose of the project?
The equivalent in JavaScript would be OtherClass. In Ethereum, keeping your code DRY will directly save you money. Peaster is a poet, novelist, and cryptocurrency editor. Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. With proxy libraries, our base contract is a library already deployed on the blockchain. When we create an instance of this, we will deploy a contract that forwards its calls to the address that is specified. Let me be emphatic: Below is the actual code that was attacked. It's essentially like a super call, except without the inheritance. The default multi-sig wallet in Parity did exactly. It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. It underwent extensive peer review. The Universal Protocol Platform is creating a common universal language that allows distinct blockchains and token-based projects to interact freely and frictionlessly. Having sounded the alarm bells, a group of benevolent white-hat hackers from the Ethereum community rapidly organized. Posted by William M. Rather, it was a developer how to see private key json ethereum is the bitcoin encrypted in a bitcoin cooling gdax cryptopia coinbase contract. This is the type of wallet the hacker attacked.
Once the money was safely stolen, they began the process of returning the funds to their respective account holders. Ethereum has a fairly unique programming model. They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why it loses. Rather, it confirms what everyone already knows: But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money. You will receive 3 books: Before the age of the client-server web model, most programming was done for packaged consumer software or on embedded systems. Either check would've made this hack impossible. All Posts Website https: Related Articles. The equivalent in JavaScript would be OtherClass. Peaster is a poet, novelist, and cryptocurrency editor. They say you can tokenize just about anything on the Ethereum blockchain. They want to see their vision of the future come true.
Prices via Shutterstock; Charts via TradingView. This shared library is referenced by the public key of the library contract. Learn smart contract development. Notify me of follow-up comments by email. Economic Calendar Tax Withholding Calculator. Learn. Complexity is the enemy of security. Sign in Get started. Ethereumsmart contractsand digital wallets. Your email address will not be published. Not being able to upgrade code after launching it? In Ethereum, keeping your code DRY will directly save you money. The Universal Protocol Platform is creating a common universal language that allows distinct blockchains and token-based projects to interact freely and frictionlessly. As seen in the above chart, BTC started this uptrend in May ofwhich set the stage for a more than 1, percent bull run up to the bitcoin gambling referral zotac geforce gtx 1080 ti for mining how many hashes of the year. This means that if you, your father, and your dollars into bitcoins proxy contract ethereum are each signatories on this wallet, even if a criminal hacked your mother and stole her private key, they could still not access your funds. In the case of a successful attack, defense is extremely difficult. Act III: What about the people who mercury altcoin buying storing altcoins traded assets with the attacker? They did it because they believe in this ecosystem. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses its blockchain to record state ledger nano s preinstalled dwarfpool coinbase in a gigantic distributed computer. The correlation gets a bit more interesting when BTC finally began a new uptrend above its peak. Sign Up Log In.
Unfortunately, the blockchain security model is more akin to the older model. Addison Huegel addison blockpr. In Mayboth stabilized in a sideways fashion, followed by a minor upswing second white block. A technical explanation of the attack specifically for programmers. Skip to main content. Complexity is the enemy of security. Conclusion Could it be an elaborate coincidence? They call you to your senses and force you to keep your eyes open. Below is the actual code that was attacked.
A technical explanation of the attack specifically for programmers. MarketWatch Partner Center. It held a reference to a shared external library which contained wallet initialization logic. In May , both stabilized in a sideways fashion, followed by a minor upswing second white block. If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. Most of the programmers who are getting into this space, myself included, come from a web development background, and the blockchain toolchain is designed to be familiar for web developers. Rather, it confirms what everyone already knows: OSTK followed suit and broke its downtrend just a couple months later which lead to a surge of more than percent by the end of the year. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. Yesterday, a hacker pulled off the second biggest heist in the history of digital currencies. What follows is a technical explanation of exactly what happened. Complex programs are more difficult to reason about and harder to identify edge cases for. This is the type of wallet the hacker attacked. And so did the reviewers who audited this code. Related Articles. The equivalent in JavaScript would be OtherClass.
All programs carry the risk of developer error. You can think of this as equivalent to a raw eval statement, running on a user-supplied string. Nope, all the cryptography was sound. Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. It underwent extensive peer review. Either check would've made this hack impossible. But they took it a step further, and herein was their critical mistake. The less the language lets you do, the easier it is to analyze and prove properties of a contract. In the world of digital currencies, wallets are how you store your assets. The attacker essentially reinitialized the contract by delegating through the library method, overwriting the owners on the original contract.