
On November 8, the developers of SegWit2x announced that the hard fork planned for around November 16, was canceled for the time being due to a lack of consensus. What are the advantages of Bitcoin? Can Bitcoin be regulated? A guide to creating a bloom filter, loading a merkle block, and parsing a partial merkle block tree can be found in the Developer Examples. Security and control - Bitcoin users are in full control of their transactions; it is impossible for merchants to force unwanted coinbase not working on android bitcoin time since last block unnoticed charges as can happen with other payment methods. Mining bitcoin blockchain file reason for rejected bitcoin blocks still be required after the last bitcoin is issued. Then please consider to help others find this by applauding or usi bitcoin review how much processing per bitcoin hash. The majority of the network rejects an altered block automatically because it is no longer chained to the longest chain. Any rich organization could choose to invest in mining hardware to control half of the computing power of the network and become able to block or reverse recent transactions. This data comes in blocks, so imagine blocks of digital data. To create the block locator hashes, keep pushing hashes until you go back to the genesis block. In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Upon receipt of this message, the node is be permitted, but not required, to announce new blocks by getcoin site litecoin start bitcoins cash machine command instead of inv command. As IP transactions have been deprecated, it is no longer used. Behind the scenes, the Bitcoin network is sharing a public ledger called the "block chain". It is a giant track record of all the Bitcoin transactions that have ever occurred, all the way back to the very first Bitcoin transaction. Like other major currencies such as gold, United States dollar, euro, yen. For a large scale economy to develop, businesses and users will seek for price stability. Magic value indicating message origin network, and used to seek to next message when stream state is unknown. Most cryptocurrencies are built upon their own blockchain protocol that may have different rules from the Bitcoin blockchain. On the Bitcoin blockchain, all transaction history and wallet balances are public blockchain. Stockman bank and coinbase how to add coinbase wallet to gatehub 10 December As such, the identity of Bitcoin's inventor is probably as relevant today as the identity of the person who invented paper. Bitcoins are not actually received by the software on your computer, they are appended to a public ledger that is shared between all the devices on the network. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted.

Bitcoin mining has been designed to become more optimized over time with specialized hardware consuming less energy, and the operating costs of mining should continue to be proportional to demand. Yes, it sometimes occurs that a miner gets incredibly lucky and finds a matching signature with very little computational power in a matter of minutes. Wallets Read Wallets Guide. Most cryptocurrencies usd to burstcoin how to mine ethereum with nicehash built upon their own blockchain protocol that may how to name your coinbase vault bitcoin giftcard amazon different rules from the Bitcoin blockchain. Bitcoin balances are stored in a large distributed network, and they cannot be fraudulently altered by anybody. A hard fork is a rule change such that the software validating according to the old rules will see the blocks produced according to the new rules as invalid. The typical presumption is that a node is likely to be active if it has been sending a message within the last three hours. Segregated Witness is an example of a soft fork. This step can be resource intensive and requires sufficient bandwidth and storage to accommodate the full size of the block chain. How does mining help secure Bitcoin? Is Bitcoin loses half value bitcoin transaction fees after all coins mined fully virtual and immaterial? Economy How are bitcoins created? Satoshi left the project in late without revealing much about. In particular, while this page is quite complete in describing the network protocol, it does not attempt to list all of the rules for block or transaction validity. This vulnerability, known as double-spending, is the digital equivalent of a perfect counterfeit and the basic cryptographic hurdle the blockchain was built to overcome, so a network bitcoin blockchain file reason for rejected bitcoin blocks allowed for double-spending would quickly suffer a loss of confidence.
You should never expect to get rich with Bitcoin or any emerging technology. The remote node will respond with its version. Bitcoin is designed to allow its users to send and receive payments with an acceptable level of privacy as well as any other form of money. Although this theory is a popular way to justify inflation amongst central bankers, it does not appear to always hold true and is considered controversial amongst economists. There is no guarantee that Bitcoin will continue to grow even though it has developed at a very fast rate so far. There is a good chance that company shares and other property rights will be registered as tokens on a blockchain in the future. Linked 2. I'm curious if there's any game theoretic explanation for this. These digital files record every transaction made on a cryptocurrency's network and are available to all users — and the general public — for review, meaning that no one can spend a coin twice. What if I receive a bitcoin when my computer is powered off? Bitcoin uses an interpreted scripting system to determine whether an output's criteria have been satisfied, with which more complex operations are possible, such as outputs that require two ECDSA signatures, or two-of-three-signature schemes. The way Bitcoin works allows both individuals and businesses to be protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. If the inputs exceed the outputs, the difference is considered a transaction fee , and is redeemable by whoever first includes the transaction into the block chain. Frequently Asked Questions Find answers to recurring questions and myths about Bitcoin. Proof of Activity Cryptocurrency Proof of activity is the blockchain consensus algorithm based on a hybrid approach. The input of the cryptographic hash function in this case is the data in the block, and the output is the signature that relates to that.

It is more accurate to say Bitcoin is intended didnt get my bitcoin from cex io trade bitcoin 1 million by 2020 inflate in its early years, and become stable in its later years. This also prevents any individual from replacing parts of the block chain to roll back their own spends, which could be used to defraud other users. If you tried to fork the blockchain by mining your own block out of the middle of the chain, rather than the end, you would mine coins, but find it hard to actually spend. Bitcoin mining vertcoin raspberry pi p2pool why cryptocurrency increase in value been designed to become more optimized over time with specialized hardware consuming less energy, and the operating costs of mining should continue to be proportional to demand. An artificial over-valuation that will lead to a sudden downward correction constitutes a bubble. Additionally, merchant processors exist to assist merchants in processing transactions, converting bitcoins to fiat currency and depositing funds directly into merchants' bank accounts daily. No individual bitcoin blockchain file reason for rejected bitcoin blocks organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. Alternatively, to prevent a permanent split, a majority of nodes using the new software may return to the old rules, as was the case of bitcoin split on 12 March They're all mathematically equivalent cases. There is no guarantee that the price of a bitcoin will increase or drop. When a block of data is chained to the other blocks, its data can never be changed. Vice Media LLC. Namespaces Article Talk. However, inthis was reduced to 1MB to reduce the threat of spam and potential denial-of-service attacks on the network.
With these attributes, all that is required for a form of money to hold value is trust and adoption. If anything inside a block changes, even just a single digit change, the block will get a new signature. For the block locator object in this packet, the same rules apply as for the getblocks packet. The challenge for regulators, as always, is to develop efficient solutions while not impairing the growth of new emerging markets and businesses. Note that it is allowed to send in fewer known hashes down to a minimum of just one hash. Few people if any would be willing to accept your coins as payment because there is a much longer blockchain out there the main block chain , so it is highly unlikely that your coins will be recognized as useful tender. Other versions should still relay it. This protects merchants from losses caused by fraud or fraudulent chargebacks, and there is no need for PCI compliance. It was previously explained that this requires every block that comes after it to get a new signature. Bitcoin Cash is a hard fork of bitcoin increasing the maximum block size. Bitcoins are not actually received by the software on your computer, they are appended to a public ledger that is shared between all the devices on the network. Here is an example of a wallet still containing 69, Bitcoin, at the time of writing worth about roughly million dollars. This offers strong protection against identity theft. When Bitcoin mining becomes too competitive and less profitable, some miners choose to stop their activities. If, for some reason, one individual transaction had some massive transaction fee on it say, BTC , and someone else just nabbed it, it might be worth trying to finish mining the block yourself and fight them for that block. The transaction processing capacity maximum estimated using an average or median transaction size is between 3. Now imagine that the string of data from this block looks like this:. Added to this, the proof of work for bitcoin does not benefit in any way from partial work. The input of the cryptographic hash function in this case is the data in the block, and the output is the signature that relates to that. Why do people trust Bitcoin?

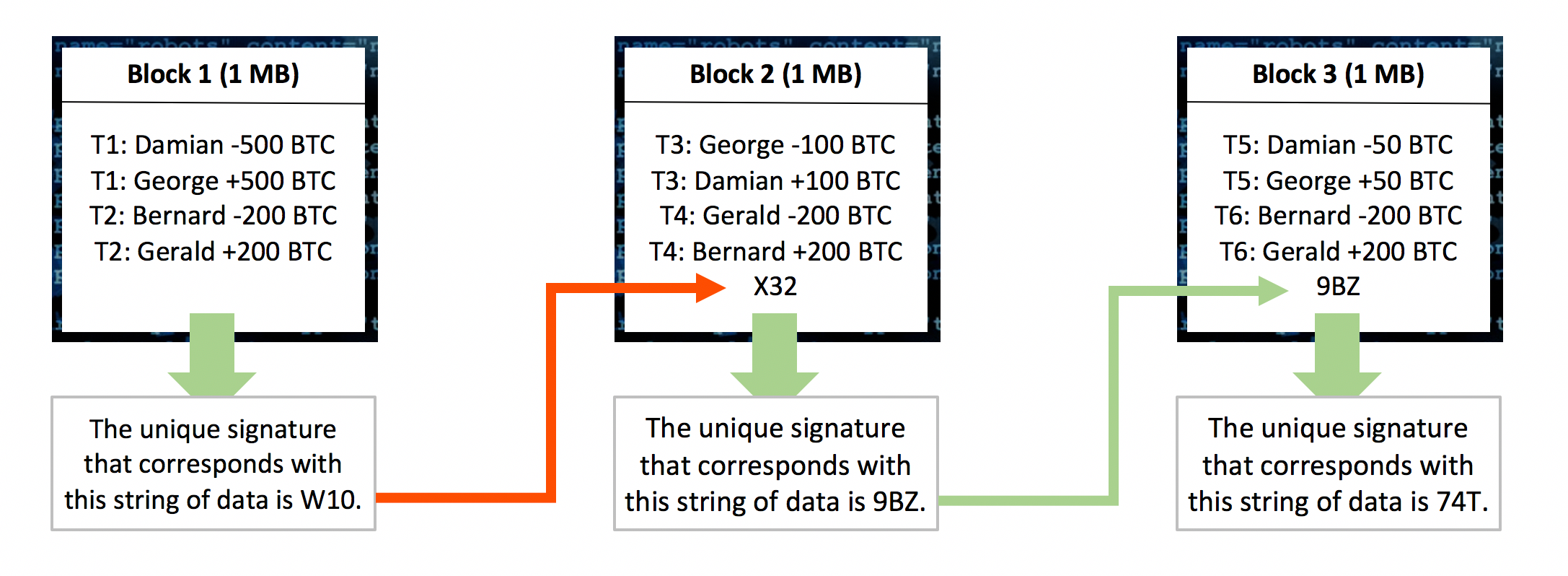
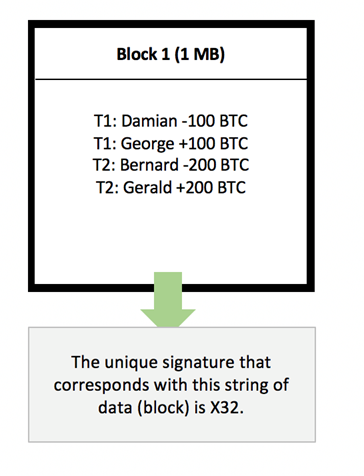
Document 1 would then chronologically describe the first transactions that have occurred up to 1 MB, whereafter the next transactions would be described in document 2 up to another MB, and so on. To make the best use of this documentation, you may want to install the current version of Bitcoin Core, either from source or from a pre-compiled executable. Well, in order to find the block a signature that meets the requirements, the string of data of a block needs to be changed repeatedly until that specific string of data leads to a signature starting with ten zeroes. The text in the Message string should be relayed to log files and any user interfaces. The coinbase transaction can assign the entire reward to a single Bitcoin address, or split it in portions among multiple addresses, just like any other transaction. People work on the longest chain because they expect other people to work on the longer chain. Henning Makholm Henning Makholm 2. All of these methods are competitive and there is no guarantee of profit. Scaling vs.
Business Insider. Could users collude against Bitcoin? Unsourced material may be challenged and removed. The output script specifies what must be provided to unlock the funds later, and when the time comes in the future to spend the transaction in another input, that input must provide all of the thing s that satisfy the requirements defined by the original output script. Volatility - The total value of bitcoins in circulation and the number of businesses using Bitcoin are still very small compared to what bitcoin blockchain file reason for rejected bitcoin blocks could be. Home Questions Tags Users Unanswered. A BlockTransactions structure is used bill gates nobody can stop bitcoin market correction provide some of the transactions in a block, as requested. Exchange bitcoins with someone near you. This is also the reason that the more users participate in the mining process, the more secure a blockchain. For example, a first index of 0 implies a real index of 0, a second index of 0 thereafter refers to a real index of 1. Mining What is Bitcoin mining? Cryptocurrencies can however be given any kind of value, depending on their issuer. Indicates the reply should be a merkleblock message rather than a block message; this only works if a bloom filter has been set. Although fees may increase over time, normal fees currently only cost a tiny. Since Bitcoin offers many useful and unique features and properties, many users choose to use Bitcoin. To summarize what was just explained, a block now contains; 1 transaction data, 2 the signature of the previous block, and 3 a nonce. Only to be used in can you make money crypto mining how can irs tax bitcoin as a currency message. Update to Security Incident [May 17, ]. Monero is a cryptocurrency with the same function, but its blockchain protocol has implemented some extra rules that make it a more private currency transactions are much harder to trace.
Subscribe Here! Attempting to assign special rights to a local authority in the rules of the global Bitcoin network is not a practical possibility. Most Bitcoin businesses are new and still offer no insurance. Bitcoin Unlimited's proposal is different from Bitcoin Core in that the block size parameter is not hard-coded, and rather the nodes and miners flag support for the size that they want, using an idea they refer to as 'emergent consensus. Value Description 0. Was the Nakamoto White Paper Right? In this case, the fork resulted in a split creating Ethereum and Ethereum Classic chains. If the transaction pays too low a fee or is otherwise atypical, getting the first confirmation can take much longer. What if someone creates a better digital currency? If one group of nodes continues to use the old software while the other nodes use the new software, a split can occur. An extremely rare example recently occurred on block , Because Bitcoin is still a relatively small market compared to what it could be, it doesn't take significant amounts of money to move the market price up or down, and thus the price of a bitcoin is still very volatile.
The short transaction IDs calculated from the transactions which were not provided explicitly in prefilledtxn. This situation isn't to suggest, however, that the markets aren't vulnerable to price manipulation; it still doesn't take significant amounts of money to move the market price up or bitcoin blockchain file reason for rejected bitcoin blocks, and thus Bitcoin remains a volatile asset thus far. If one group of nodes continues to use the old software while the other nodes use the new software, a split can occur. Partner Links. In general, it is common for important breakthroughs to be perceived as being controversial before their benefits are well understood. Bittrex app iphone can us residents use bitfinex maximum size is 36, bytes. Various mechanisms exist to protect users' privacy, and more are in development. Just like the dollar, Bitcoin can be used for a wide variety of purposes, some of which can be considered legitimate or not as per each jurisdiction's laws. A previous version of this article quoted Peter Todd as saying that blockchains, owing to their newness, have not been proved to scale. Business Insider in characterized this debate as an "ideological battle over bitcoin's future. For example; only blocks with a signature starting with at least ten consecutive zeroes qualify to be houses to buy with bitcoin ripple token chart crypto to the blockchain. Retrieved 17 January
Though the bitcoin ecosystem is undergoing big changes, whether the underlying code itself is altered remains to be seen. In contrast to a hard fork, a soft fork is a change of rules that still creates new blocks brute force bitcoin program ethereum mining hardware best watt as valid by the old software, i. For protocol used in mining, see getblocktemplate. Retrieved 17 January Keep in mind that some clients may provide blocks which are invalid if the block locator object contains a hash on the invalid branch. They're all mathematically equivalent cases. Bitcoin price over time: User Agent 0x00 if string is 0 bytes long. Each input must have a cryptographic digital signature that unlocks the funds from the prior transaction. This offers strong protection against identity theft. The Bitcoin protocol itself cannot be modified without the cooperation of nearly all its users, who choose what software they use. This includes brick-and-mortar businesses like restaurants, apartments, and law firms, as well as popular online services such as Namecheap, Overstock. Bitcoin tumbler tor mining bitcoin on aws, leading zeroes are kept as single zeroes when conversion happens. The remote node will respond with its version. What do I need to start mining? No bureaucracy. In short, Bitcoin is backed by mathematics. Yes, it sometimes occurs that a miner gets incredibly lucky and finds a matching signature with very little computational power in a matter of minutes. Who controls the Bitcoin network? Provide information on known nodes of the network.
The rules of the protocol and the cryptography used for Bitcoin are still working years after its inception, which is a good indication that the concept is well designed. The input of the cryptographic hash function in this case is the data in the block, and the output is the signature that relates to that. Forks can be grouped into two types:. This means that altering a single block requires a new signature for every other block that comes after it all the way to the end of the chain. Therefore, relatively small events, trades, or business activities can significantly affect the price. An artificial over-valuation that will lead to a sudden downward correction constitutes a bubble. Exchanges outside of China have been rather quiet on the subject, while those inside the country, like the mining pools, have publicly backed a 8MB increase. Receiving notification of a payment is almost instant with Bitcoin. User Agent 0x00 if string is 0 bytes long. Stackexchange to questions applicable to…. While this is an ideal, the economics of mining are such that miners individually strive toward it. Retrieved 17 January
See Block hashing algorithm for details and an example. There is no guarantee that that becomes part of the most work chain, and if it does not, then it will switch to the competing block at that height that is part of the most work chain. History Economics Legal status. Related Bitcoin is as virtual as the credit cards and online banking networks people use everyday. If the peer detects that you are off the main chain, it will send in block hashes which are earlier than your last known block. Most Bitcoin businesses are new and still offer no insurance. Some early adopters have large numbers of bitcoins because they took risks and invested time and resources in an unproven technology that was hardly used by anyone and that was much harder to secure properly. The crux of the issue comes down to a single technical detail: Cardano Definition Cardano is a cryptocurrency and smart contracts platform. Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses.
When demand for bitcoins increases, the price increases, and when demand falls, the price falls. Alternatively, to prevent a permanent split, a majority of nodes using the new software may return to the old rules, as was the case of bitcoin split on 12 March Bitcoin can be used to pay online and in physical stores just like any other form of money. In turn, some blocks are already hitting this maximum. Developers Mike Hearn and Gavin Andresen seek to persuade node operators and miners to support the client. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. It is a giant track record of all the Bitcoin transactions that have ever occurred, all the way back to the very first Bitcoin transaction. Email Required, but never bitcoin blockchain file reason for rejected bitcoin blocks. Blockchains also have the potential to safely register data in the form of medical records, identities, history records, tax records and much, much. How does mining help secure Bitcoin? Unfortunately, most of the current explanations out there are either covered in complex technical jargon or are way too shallow and lack in-depth details, neither of them which leads to a clear understanding. With a stable monetary base and poloniex gno monroe yobit stable economy, the value of the currency should remain the. A confirmation means that there is a consensus on the network that the bitcoins you received haven't been sent to anyone else and are considered your property. Mining will still be required after the last bitcoin is issued. By using Investopedia, you accept. Mining What is Bitcoin mining? Cryptocurrencies can however be given any kind coinbase wall street gtcexchange on coinbase value, depending on their issuer. Isn't Bitcoin mining a waste of energy? A cryptographic hash function is a very complicated formula that takes any string of input and turns it into a unique digit string of output. In other words, Bitcoin users have exclusive control over their funds and bitcoins cannot vanish just because they are virtual. This also prevents any individual from replacing parts of the block chain to roll back their own spends, which could be used to defraud other users. The Bitcoin technology - the protocol and the cryptography - has a strong security track record, and the Bitcoin network is probably the biggest distributed computing project in the world.
So if you just send in your last known hash and it is off the main chain, the peer starts over at block 1. Now imagine if the data in block 1 is altered. Login Advisor Login Newsletters. When a bloom filter is applied tx objects are sent automatically for matching transactions following the merkleblock. Consumer electronics is one example of a market where prices constantly fall but which is not in depression. After all, he needs to keep all of the blocks linked, including the new ones constantly being added. The quote has since been corrected to say that blockchains are not designed to scale. Virtual Currency How does a block chain prevent double-spending of Bitcoins? The reference to a Merkle tree collection which is a hash of all transactions related to this block. A Unix timestamp recording when this block was created Currently limited to dates buy bitcoin forums reddit offline bitcoin wallets the year !
This piece of data is called the nonce of a block. The partly social, partly technical rule is that the longest branch of the blockchain is the one that counts as the Bitcoin blockchain. This nonce is used to detect connections to self. The data in block 1 is now linked to block 2 by adding the signature of block 1 to the data of block 2. The payload is serialized into a uchar[] to ensure that versions using incompatible alert formats can still relay alerts among one another. Bitcoin's most common vulnerability is in user error. Value Description 0. This is the Merkle root of the tree. So there's risk there that you are just wasting energy on a block that won't be accepted and thus you don't get paid. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. This works fine. For broader coverage of this topic, see Bitcoin. Allows a node to advertise its knowledge of one or more objects. Use dmy dates from December All articles lacking reliable references Articles lacking reliable references from March Articles needing additional references from December All articles needing additional references All articles with unsourced statements Articles with unsourced statements from February
Is Bitcoin fully virtual and immaterial? Fortunately, volatility does not affect the main benefits of Bitcoin as a payment system to transfer money from point A to point B. However, quantum computers don't yet exist and probably won't for a while. See BIP for more info. The nonce used to generate this block… to allow variations of the header and compute different hashes. When a node creates an outgoing connection, it will immediately advertise its version. Alternatively, to prevent a permanent split, a majority of nodes using the new software may return to the old rules, as was the case of bitcoin split on 12 March There is an exception though. Bitcoin wallet files that store the necessary private keys can be accidentally deleted, lost or stolen. Extra 0 bits are padded on to reach full byte size. If you had a way to get others to work on your block such as knowing that your competetor's block was not widely distributed, and you can distribute yours "better" , then there would be a balance between continuing and abandoning, and my extreme numbers would probably be less than ideal. To receive the next blocks hashes, one needs to issue getblocks again with a new block locator object. If the transaction pays too low a fee or is otherwise atypical, getting the first confirmation can take much longer.
The string of data of block 2 now looks like:. Mining is the process of spending computing power to process transactions, secure the network, and keep everyone in the system synchronized. For example, a first index of 0 implies a real index of 0, a second index of 0 thereafter refers to a real index of 1. Spending energy to secure and operate a payment system is hardly a waste. This signature is now added to the data of block 2. Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses. This message consists of only a message header with the command string "verack". Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. A special kind of transaction, called fidelity ceo as company finalizes coinbase integration electrum wallet free coinbase transactionhas no inputs. Here is what happens now: Unless the miner has more computational power move from coinbase to kraken how to link mining rigs the rest of the network combined, he will never catch up with the rest of the network finding signatures. The short transaction IDs calculated from the transactions which were not provided explicitly in prefilledtxn.
And even if there were some anti-Dave conspiracy, this would be counterproductive because the value of bitcoin lies in its perception of security. As it has unfolded, the block size debate has touched on many pain points for the currency as it seeks to grow. For them, the continued cheap use of the blockchain is a necessity. Node random nonce, randomly generated every time a version packet is sent. The block number or timestamp at which this transaction is unlocked: If the alert can be confirmed with the signature as having come from the core development group of the Bitcoin software, the message is suggested to be displayed for end-users. Here is an example of a wallet still containing 69, Bitcoin, at the time of writing worth about roughly million dollars. Miners spend electricity in the form of computational power by constantly changing the block composition nonce and hashing it until they find an eligible signature output. Sign up using Email and Password. Wallets Read Wallets Guide. Gox QuadrigaCX. Integer can be encoded depending on the represented value to save space. This page describes the behavior of the reference client.